Source: securityboulevard.com – Author: Billy VanCannon, Director of Product Management
A ransomware gang known as Cl0p has found and exploited vulnerabilities in several file-transfer tools, including Fortra’s GoAnywhere, Accellion’s file transfer appliance (FTA), and Progress Software’s MOVEit. Though known as a ransomware group, they seem to be skipping the part where they encrypt the victim’s data and are simply extorting based on releasing the sensitive data to the public. Cl0p has claimed to compromise over 130 organizations, including governments, universities, healthcare, airlines, media, and financial institutions1. This list could be even worse, given many of the breached organizations are vendors. For example, one primary victim using MOVEit was Zellis, a human resources software maker, whose breach included payroll data for British Airways2. Another example is Guidehouse, which uses Accellion’s FTA and is a vendor for Morgan Stanley, the investment banking firm. Morgan Stanley has confirmed that documents with customers’ personally identifiable information (PII) were stolen3 due to a breach related to Guidehouse.
Security Measures Bypassed
One thing that stands out in these attacks is how several traditional security measures had to fail for the data to be stolen.
1) Unnecessary exposure to the Internet
Though the vulnerabilities of the three file-transfer vendors vary in the details, they are all remote execution bugs that should have been mitigated by avoiding exposure to the internet. However, researchers were able to use Shodan (a free internet search tool that can find publicly exposed databases and servers) to find thousands of MOVEit2 and GoAnywhere4 servers that were exposed to the internet. There is a constant stream of news about compromised servers, databases, and object stores (like AWS S3 buckets) that victims had assumed did not have internet access. While numerous security posture management tools are coming to the market to identify vulnerabilities such as this, they don’t fix or address the vulnerability (it’s the company’s responsibility to do that).
2) Keep all software fully patched
Another common security measure is to keep all software fully patched. This is absolutely required, however, when vulnerabilities are newly discovered (known as zero-day vulnerabilities) there is often no patch available. In the cases of MOVEit (CVE-2023-34362) and GoAnywhere (CVE-2023-0669) the first number of the CVE is 2023, meaning they were just reported in 2023. The Cl0p gang discovered the vulnerability and exploited it before the vendors could create a patch. The same can’t be said for the Accellion vulnerabilities (CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, CVE-2021-27104) that have been known since at least 2021 and CISA even listed them in the “Top Routinely Exploited Vulnerabilities” of 20215.
3) Stop using unsupported software
Accellion FTA brings up another missed security measure and that is to not use unsupported software. Accellion FTA is a 20-year old product that went end-of-life April 30, 2021 and replaced by “… modern and more secure platform, Kiteworks®”6.
4) Key management, where and how the data is encrypted
In the Morgan Stanley case mentioned above, the stolen data was encrypted, but the decryption keys were stolen as well. It is important to ensure the encrypted data is kept separate from the keys.
5) Protect data when it’s accessed (data in use), as well as data at rest and data in motion
Finally, all of these file-transfer tools encrypt the data in-motion (as it is being transferred) using TLS/SSL or SFTP protocols. However, the data is not being stolen while it is moving over the internet, rather the tools themselves are used to pull data from the source, where it is usually not encrypted. Even if the data is encrypted in a database or object store using transparent data encryption (TDE) or full disk encryption (FDE), this only protects against the hard drives being physically stolen and doesn’t help with remote attacks.
Baffle’s Solution
Baffle Data Protection Services for Object Stores provides the ability to encrypt files from any S3, Azure blob storage, SFTP or HTTPS source to any other destination using the same protocols. Entire files, elements of files (CSV, JSON, XML), or regex matches of text files can be encrypted using traditional AES encryption or format preserving encryption. Every tenant (user or service account) may be assigned their own keys for further data isolation.
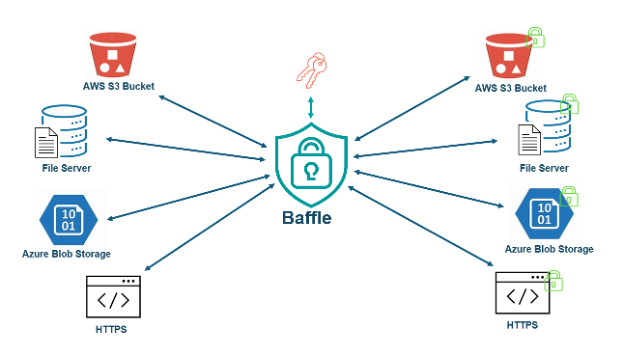
Figure 1. Baffle for Encryption of data-at-rest/ingestion
Another instance of Baffle is deployed at the receiving end of the file transfers to protect the data to the point of use (figure 2). To keep the encryption keys separated from the data, Baffle implements envelope encryption and therefore never has access to the key encryption keys (KEK). The KEKs in-turn are kept by a customer-managed key management service (KMS) and ultimately on a hardware security module (HSM) to protect from physical and remote attacks. Role-based access controls for each Baffle instance ensure decryption according to each user’s need to know. By encrypting the data from end-to-end, (data-at-rest, through the pipeline, and to the final user), the sensitive information is protected even if the database or file transfer tool is compromised.
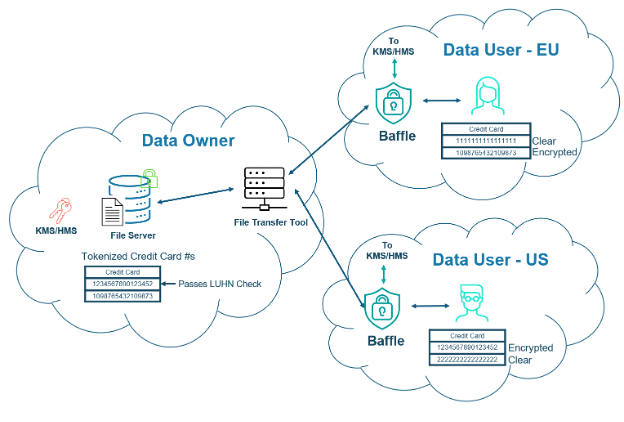
Figure 2. Baffle for Encryption until the data is used
Conclusion
Defense-in-depth is a concept that has been around for a long time, but this incident is a reminder that it is still relevant today. While all the other security measures are important, if end-to-end encryption is implemented and the hackers still manage to get the files, they are worthless. From PCI-DSS to GDPR, strong encryption and key management is recognized by all the major security and privacy standards for protecting data even when the ciphertext is accessed. This is the value of data-centric protection and it virtually eliminates the impact of data breaches.
Learn More
To see a demo of data masking and discuss your data protection concerns, please schedule a meeting with Baffle.
References:
1New victims come forward after mass-ransomware attack | TechCrunch
2Microsoft says Cl0p ransomware gang is behind MOVEit mass-hacks, as first victims come forward | TechCrunch
3The Accellion data breach continues to get messier | TechCrunch
4The GoAnywhere data breach explained | ITPro
5Top Routinely Exploited Vulnerabilities | CISA
The post A look into the file-transfer attack (and how to protect your data) appeared first on Baffle.
*** This is a Security Bloggers Network syndicated blog from Baffle authored by Billy VanCannon, Director of Product Management. Read the original post at: https://baffle.io/blog/a-look-into-the-file-transfer-attack-and-how-to-protect-your-data/
Original Post URL: https://securityboulevard.com/2023/06/a-look-into-the-file-transfer-attack-and-how-to-protect-your-data/
Category & Tags: Security Bloggers Network,Accellion,CL0P,clop,File Transfer Hack,File Transfer Security,GoAnywhere,MOVEit – Security Bloggers Network,Accellion,CL0P,clop,File Transfer Hack,File Transfer Security,GoAnywhere,MOVEit
Views: 6





















































