Source: securityboulevard.com – Author: Alexandra Aguiar
The average vulnerability and patch management backlog now contains over 100,000 vulnerabilities, making better vulnerability prioritization essential to ensure the most pressing threats are promptly addressed. In this blog, we’ll delve deeper into the different dimensions of prioritizing vulnerabilities—severity, exploitability, exposure business context, and controls—and explore the best practices, tools, and resources that empower organizations to fortify their security posture and stay ahead of potential threats.
Understanding Vulnerability Prioritization
Vulnerability prioritization is the process of systematically evaluating and ranking vulnerabilities based on their potential impact and exploitability to help organizations identify which should be addressed first. By better prioritizing vulnerabilities, organizations can effectively allocate their resources and focus on mitigating the most critical risks to their systems and data.
To understand vulnerability prioritization, it is crucial to recognize that not all vulnerabilities are created equal. Some vulnerabilities may have a higher potential impact, while others may be more easily exploitable. The key is to assess and rank vulnerabilities based on these factors to identify the most critical ones.
Effective prioritization helps security teams to use their limited resources judiciously, focusing on the most critical vulnerabilities to their business that could lead to severe breaches or system compromises. It not only enhances the efficiency of remediation efforts but also fortifies an organization’s overall security posture by ensuring that the most pressing threats are addressed promptly.
The ability to discern which vulnerabilities require immediate attention is paramount. To do so effectively, organizations must structure their approach around the four critical dimensions of effective prioritization: severity, exploitability, business context, and controls.
- Severity: Magnitude of the Threat
Severity refers to the potential impact a vulnerability can have on a system, application, or organization. Vulnerabilities are typically rated based on a scale such as the Common Vulnerability Scoring System (CVSS), which considers factors like access complexity, authentication requirements, and impact on confidentiality, integrity, and availability.
To evaluate a vulnerability’s overall severity:
- Establish a Clear Scoring System: Develop a well-defined scoring system that aligns with industry standards like CVSS. This provides a consistent and objective way to assess severity.
- Regularly Update Severity Ratings: Periodically reevaluate the severity of vulnerabilities as new information emerges, or threat landscapes evolve.
- Allocate Resources Proportionally: Allocate more resources to addressing high-severity vulnerabilities while balancing overall risk management efforts.
- Exploitability: Likelihood of Exploitation
Exploitability is the ease in which a vulnerability can be exploited by a malicious actor. Key aspects that define exploitability include ease of exploitation and public exploitability.
To effectively assess the exploitability:
- Leverage Vulnerability Intelligence: Stay informed about the latest threats, exploits, and attack patterns to understand the current exploit landscape. Several resources exist and are widely used to help organizations understand the urgency of vulnerabilities, including:
- The Cybersecurity Infrastructure Security Agency (CISA) maintains a Known Exploited Vulnerabilities (KEV) catalog. The CISA KEV catalog is a list of known vulnerabilities that malicious actors actively use to compromise systems.
- The Exploit Prediction Scoring System (EPSS) leverages estimates the probability of a software vulnerability being exploited according to a data-driven algorithm developed by the Forum of Incident Response and Security Teams (FIRST)
- Assess Patch Availability: Prioritize vulnerabilities for which patches or mitigations are not available or are difficult to implement.
- Consider Vulnerability Exposure: Evaluate if a vulnerability is exposed to the internet or within the organization’s internal network, impacting the potential for exploitation. Understanding the potential attack path of the adversary is important here.
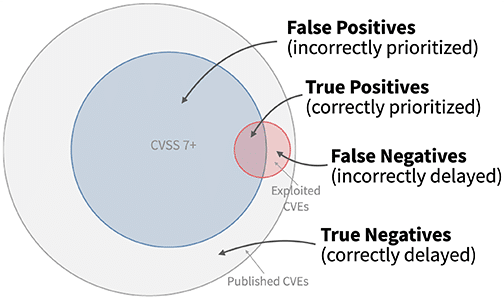
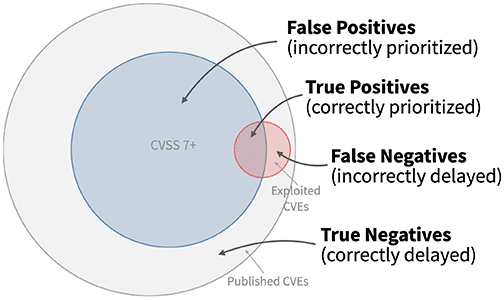
Clearly, even one additional layer of intelligence can significantly improve the vulnerability prioritization process. However, even critical, actively exploited vulnerabilities is not foolproof—and can still leave an overwhelming backlog.
Image Source: FIRST.org
- Business Context: Environmental Considerations
Context is about understanding how a vulnerability relates to the specific organizational environment, including the system’s role, data it handles, and its criticality to business operations. The vulnerability on a mission-critical system will have a higher priority than one in a less critical system.
To effectively incorporate context into the vulnerability prioritization process:
- Define Organizational Risk Tolerance: Understand the organization’s risk tolerance and align vulnerability prioritization accordingly.
- Account for Asset Sensitivity: Consider the sensitivity of the assets affected by the vulnerability and their importance to the organization’s operations.
- Flag Business-Critical Systems: Focus on vulnerabilities that could have a direct impact on business continuity, financial operations, or sensitive data.
- Controls: Existing Safeguards & Countermeasures
Controls refer to the security measures and safeguards in place to mitigate the potential impact of a vulnerability. Evaluating vulnerabilities in the context of available controls helps in efficient resource allocation.
Best practices to incorporate the controls dimension include:
- Review Current Security Measures: Assess the effectiveness of compensating security controls, such as firewalls, intrusion detection systems, and access controls.
- Consider Defense-in-Depth Strategies: Give higher priority to vulnerabilities in systems lacking multiple layers of defense.
- Account for Security Hygiene: Prioritize vulnerabilities in systems with poor security practices or outdated security configurations.
| Dimension | Definition | Why it’s important | Key Considerations |
|---|---|---|---|
| Severity | The impact a vulnerability can have on a system, application, or organization | Ensures that resources are allocated to address the most damaging and likely vulnerabilities first. | Potential Damage: Consider the potential harm the vulnerability could cause in terms of data loss, financial impact, or operational disruption.
Data Exposure: Evaluate the type of data that could be exposed if the vulnerability is exploited, such as sensitive customer information or financial records. Ease of Exploitation: Assess the level of skill and effort an attacker would need to exploit the vulnerability successfully. |
| Exploitability | Exploitability focuses on the likelihood that a vulnerability will be exploited by malicious actors. | Helps teams to focus on vulnerabilities that are most likely to be targeted by attackers. | Availability of Exploits: Check if there are known and accessible exploits targeting the vulnerability, as this increases the likelihood of exploitation.
Ease of Exploitation: Evaluate how easy it is for a potential attacker to exploit the vulnerability. Vulnerabilities that are easy to exploit are often prioritized higher. Exposure to the Internet: Consider if the affected system is exposed to the internet, as this increases the risk of exploitation. |
| Context | The understanding of the unique circumstances and environment of an organization | Empowers teams to tailor the response to vulnerabilities based on their potential impact on the organization. | Asset Criticality: Vulnerabilities on critical assets, such as servers containing sensitive data, should take precedence over those on less critical assets.
Business Impact: Assess how a vulnerability might impact the organization’s core business functions, reputation, or regulatory compliance. Sensitive Data Handling: Evaluate if the affected systems handle sensitive data and the potential impact on privacy and compliance. |
| Controls | Existing security measures or defenses in place that can mitigate the impact of a vulnerability. | Ensures that investments are made where they can provide the most significant security improvements. | Mitigation Controls: If strong mitigation controls are already in place for a vulnerability, it may be lower on the priority list since the risk is effectively reduced.
Compensating Controls: Assess whether compensating controls can be implemented to reduce the risk of a vulnerability while a patch or remediation plan is developed. Resilience of the System: Consider the system’s overall resilience to potential exploitation and its ability to limit the damage. |
Prioritizing vulnerabilities is a multifaceted process that requires a thorough evaluation of severity, exploitability, context, and compensating controls. By adopting a systematic approach that integrates these dimensions, organizations can effectively allocate resources, reduce risks, and enhance their overall cybersecurity posture. Staying vigilant and continually refining this approach is crucial in the dynamic landscape of cybersecurity.
When done correctly, effective vulnerability prioritization provides a roadmap for organizations to navigate the complex landscape of threat and vulnerability management, enabling them to allocate resources wisely, align cybersecurity efforts with business goals, and ultimately build a resilient security posture that can effectively combat evolving cyber threats.
Discover how Noetic empowers teams to prioritize the protection of their organization’s most valuable assets: Noetic Threat and Vulnerability Management Solutions.
*** This is a Security Bloggers Network syndicated blog from Noetic: Cyber Asset Attack Surface & Controls Management authored by Alexandra Aguiar. Read the original post at: https://noeticcyber.com/mastering-the-art-of-vulnerability-prioritization/
Original Post URL: https://securityboulevard.com/2023/09/mastering-the-art-of-vulnerability-prioritization-a-step-by-step-guide/
Category & Tags: Security Bloggers Network,Blog – Security Bloggers Network,Blog
Views: 2