Source: www.darkreading.com – Author: Ganesh Pai, Founder & CEO, Uptycs
Most enterprise chief information security officers (CISOs) are very familiar with infostealers, a pervasive breed of malware that quietly gathers website credentials, passwords, and other financial information from a compromised user account. Infostealers are nothing new; they have been a common tool in the threat actor’s toolbox since 2006, when the Zeus online banking Trojan was first spotted in the wild.
However, new research by the Uptycs research team has uncovered a stark increase in the distribution of infostealer malware over the past year. The study, “Stealers Are Organization Killers,” details a variety of new infostealers preying on Windows, Linux, and macOS systems. It shows that incidents more than doubled in the first quarter of 2023 compared with the same time last year.
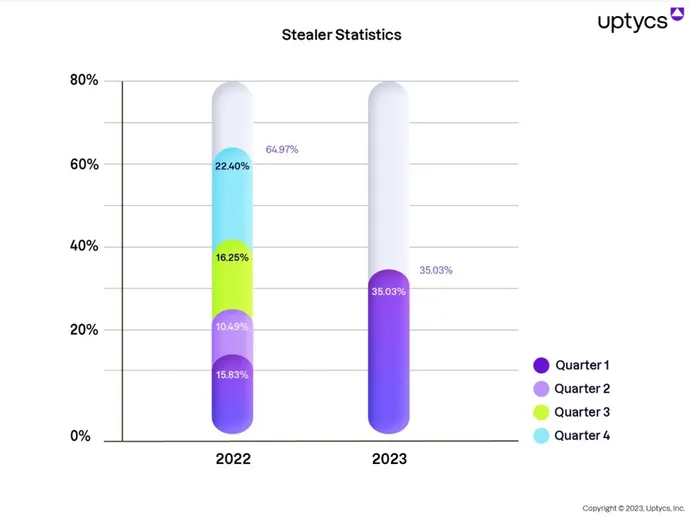
But it’s not just the growth in the volume of infostealers that’s raising eyebrows among threat researchers and security analysts. More concerning is how criminal organizations are finding novel ways to customize, market, and deploy infostealer malware at an unprecedented scale.
The Rapidly Evolving Infostealer Market
Initially designed as simple, single-purpose malware, infostealers have become sophisticated tool sets with advanced evasion techniques and modular architecture. Some operators even use generative artificial intelligence (AI) to mimic human-like behaviors.
This transformation has been fueled not only by criminal groups’ relentless pursuit to infiltrate more systems but also by the emergence of new Web platforms that facilitate creating and deploying infostealers.
Building and deploying an infostealer once required basic coding and IT operations skills. These days, anyone with a laptop and as little as $50 in their bank account can kickstart their own malicious campaigns by signing up for a malware-as-a-service offering that can be found on any number of Dark Web forums.
Encrypted communications platforms like Telegram and Discord have become the favored emporium for operators and buyers. These platforms have also become popular vehicles for buying and selling pilfered data. Their intuitive interfaces and end-to-end encryption make them attractive to operations security-minded cybercriminals, infostealer gangs, and newcomers. Stolen logs are often advertised and traded in private channels or groups, with a growing volume of transactions occurring directly within the platforms.
Three Strategies to Mitigate Infostealer Threats
If these trends continue, there’s little doubt that the infostealer market — and the operators’ sophistication — will grow in scale and scope. CISOs should consider adopting the following three strategies to mitigate this growing threat:
- Prioritize real-time detection: While vulnerability assessments are crucial for identifying weaknesses an attacker might exploit, they’re inherently reactive and do little to prevent malware operators from leveraging user credentials to bypass hardened authentication systems. By adopting a comprehensive extended detection and response (XDR) approach, CISOs can streamline telemetry data collection to gain a unified view across networks, endpoints, servers, and cloud workloads. This type of integrated approach is critical for accelerating the threat detection and response process, enabling security teams to proactively and quickly address infostealer and related emerging threats.
- Enforce strict access controls: Infostealers typically target data including personally identifiable information (PII), financial information, login credentials, and proprietary business data. Establishing governance over your entire infrastructure starts by properly segregating your networks so that sensitive data won’t be inadvertently exposed. Security leaders should prioritize protecting these data categories and implement stronger safeguards where gaps exist. Encrypt sensitive data at rest and in transit to make the information unreadable to unauthorized users.
- Understand the context of potential vulnerabilities: Like other cyber threats, infostealer attacks are continuously evolving as malware operators test and refine their techniques and tactics. By understanding the broader context of an infostealer attack, such as the data most likely to be targeted or the most actively exploited vulnerabilities, security teams can better predict and prioritize potential vulnerabilities to mount a fast and effective response. Having a contextual understanding of existing vulnerabilities is also essential for proactive threat hunting, which can help guide the search and shrink the time to remediation.
A Step Ahead
The battle against infostealers is yet another example of the ongoing cycle of adaptation and counter-adaptation between threat actors and security teams. As we’ve seen before, staying one step ahead of malware operators will require a comprehensive strategy that encompasses advanced technology, constant vigilance, proactive threat hunting, and ongoing education.
Original Post URL: https://www.darkreading.com/vulnerabilities-threats/3-strategies-to-defend-against-resurging-infostealers
Category & Tags: –
Views: 3




















































