Source: securityboulevard.com – Author: Michael Williams
Does A Focus on Phishing Make Sense?
Most high-profile breaches that I’ve seen in the news tend to focus on phishing attacks that led to a breach, often with ransomware as a secondary impact. With security resources being scarce, should organizations continue to focus on phishing authentication attacks? Or, are other attacks of equal or greater importance? Further, are other attacks masquerading as phishing attacks?
Guidance Issued To Date
CISA, NIST, and the OMB have issued specific guidance about authentication attacks that include phishing. Taking the guidance as a whole, MFA Credential, Replay, Impersonation, and Infrastructure authentication attacks are also critical. Their guidance, along with Axiad’s, is summarized below:
| Source | Category | Threat |
| CISA | MFA Credential | Attacks including Password phishing, Push Bombing, SIM swaps, and SS7 protocol attacks (to collect credentials in transit) |
| NIST | Replay | Record and replay end user session to capture credentials and log in as end user |
| OMB | Impersonation | Impersonating a website or application (including authenticator) to gain access to accounts and credentials |
| NIST & Axiad | Attacker-in-the-Middle
Infrastructure |
Interception of shared secrets
Attacks to the authentication infrastructure – cloud, network, core software, vaults, etc. |
Lacking insights into the prevalence and success of all authentication attacks, many organizations are prioritizing phishing defenses and so are focusing on end user training to identify phishing risks. But, is that a prudent strategy?
Axiad partnered with Enterprise Strategy Group (ESG) to explore this topic (and many others) in detail. And, the results are definitely insightful!
Enterprise Strategy Group Survey Results
Not surprisingly, password-related attacks including phishing are still the largest single factor in compromising accounts or credentials. Various aspects of password-related attacks contributing to the compromise of accounts or credentials were cited by 33% – 37% of respondents shown below (multiple responses were accepted for the factors that led to each compromise).
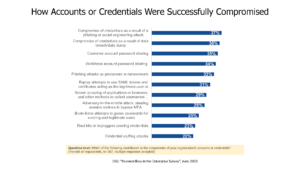
The most intriguing insights from a CISA, NIST, and OMB perspective are below the password-centric factors which were cited by 22%-31% of respondents (again, multiple responses were accepted for the factors that led to each compromise). Since they steal credentials that were leveraged in a compromise, many of these attacks could appear to be the result of a phishing attack:
- Replay attempts (31%): Capture and replay of end user authentication by an adversary is surprisingly high. This is quantitative backing for NIST’s focus on this factor.
- Screen scraping (29%): Screen scraping of userids and passwords can be done on both devices and the Web. It’s likely that the “other methods” listed also include impersonation of authenticators and websites. At nearly a third, this is suprisingly high as a factor for compromises given the variety of security defenses employed by most organizations.
- Adversary-in-the-middle (28%): Stolen session cookies can bypass a wide range of defenses – and for timeframes typically no less than 24 hours. Further, these attacks are highly effective even in complex authentication scenarios such as Virtual Desktop Infrastructure (VDI).
- Brute-force attempts (25%): A large number of applications and website tools do not provide brute-force protection by default and so this is a known risk. However, this rate is quite high and justifies auditing of all web-facing websites and applications.
- Root kits or keyloggers stealing credentials (23%): This is an attack tactic similar to screen scraping in that it captures credentials at entry. Since the malware is typically installed on the end user device, they can capture a wide range of credentials.
- Credential stuffing attacks (22%): These attacks most often involve taking a compromised credential from one site and trying it on another site in case the credential has been reused. As of 2020, there were 15 billion logins stolen from 100,000 breaches. So, it’s no wonder that these attacks are so successful.
These authentication attacks are successful even if end user behavior is free from error and the compromise is not due to a phishing attack. (Credential stuffing is perhaps a grey area since credentials should not be reused across systems but at times must be due to the architecture of the organization’s systems.) Further, since many of these attacks result in compromised credentials, they could masquerade as a phishing attack.
The high compromise rates uncovered by ESG in this survey highlight the gravity of the risks currently being outlined by CISA, NIST, OMB, and Axiad. Indeed, nearly half of organizations know they had accounts compromised over the last 12 months, and another 32% suspect this occurred. Among this group, more than three-quarters report multiple instances of credentials being compromised. Based on these findings from ESG’s research, the entire authentication process is under attack and must be secured from end to end.
Highlights
A summary of the complete ESG survey is available here. |
Recommendation: Take CISA, NIST, and OMB Guidance as a Whole
Organizations must take the above lessons to heart: while phishing and social engineering will always be a concern, threat actors are succeeding using a range of other attacks. And, these compromises can appear to be due to phishing attacks, thereby shifting the emphasis to neutralizing phishing threats rather than the actual culprits. Adding up guidance from CISA, NIST, OMB, and Axiad, the entire authentication environment is under attack – and each component is being compromised at surprisingly high rates.
To blunt these attacks, each component of the authentication environment – the primary device used by the end user, the secondary authentication device (typically a mobile phone), the authentication software (including authenticators), and the authentication environment – must be hardened and all keys and secrets protected with asymmetric cryptography to thwart successful penetrations.
A summary of the complete ESG survey is available here.
Learn More About Phishing Resistant Authentication
Axiad provides passwordless, phishing-resistant authentication for large organizations, including enterprises and government agencies. Axiad’s approach is resistant to the full range of authentication attacks – Phishing, MFA Credential, Replay, Infrastructure, and more.
The post Stop Focusing on Just Phishing appeared first on Axiad.
*** This is a Security Bloggers Network syndicated blog from Blog – Axiad authored by Michael Williams. Read the original post at: https://www.axiad.com/blog/stop-focusing-on-just-phishing/
Original Post URL: https://securityboulevard.com/2023/07/stop-focusing-on-just-phishing/
Category & Tags: Identity & Access,Security Bloggers Network,Authentication – Identity & Access,Security Bloggers Network,Authentication
Views: 0




















































