Source: securityboulevard.com – Author: Cofense
Found in Environments Protected By: Microsoft
By Tej Tulachan, Phishing Defense Center (PDC)
During the busy self-assessment season in the UK, threat actors take advantage of the heightened online activity to deceive unsuspecting individuals into revealing their sensitive information on fraudulent HM Revenue & Customs (HMRC) self-assessment websites. Phishing Defense Center (PDC) has noted this wave of attacks across various sectors and regrettably, these phishing emails often evade popular secure email gateways (SEGs) that are meant to provide protection for users.
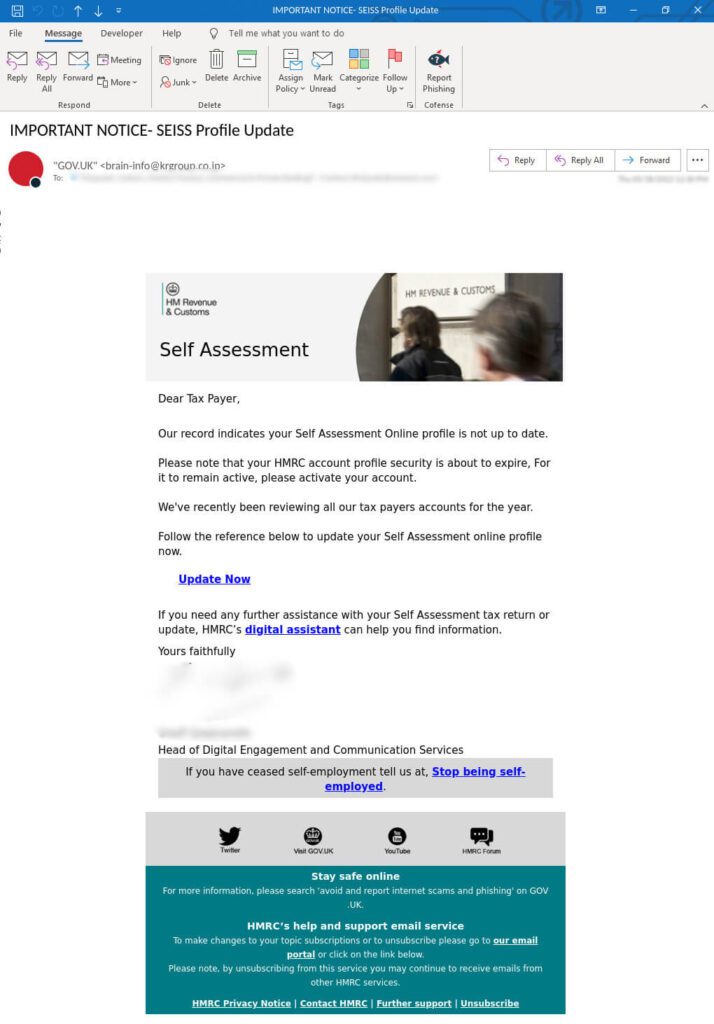
The phishing emails begin by pressuring users to immediately update their self-assessment online profile. This is a common tactic employed by threat actors to generate a deceptive perception of urgency and legitimacy. Figure 1 reveals that the sender’s address appears to be from GOV[.]UK, but upon closer examination, it becomes evident that it is a spoofed address: [email protected][.]co[.]jp. A spoofed address like this is used in phishing emails to trick recipients into thinking that the email originates from a trustworthy source, specifically HMRC in this instance. When users hover over the “Update Now” link as shown in Figure 1, users are redirected to a malicious URL: hxxps://rumanta[.]com/cs/hmrc. This marks the initiation of the first phase of the attack.
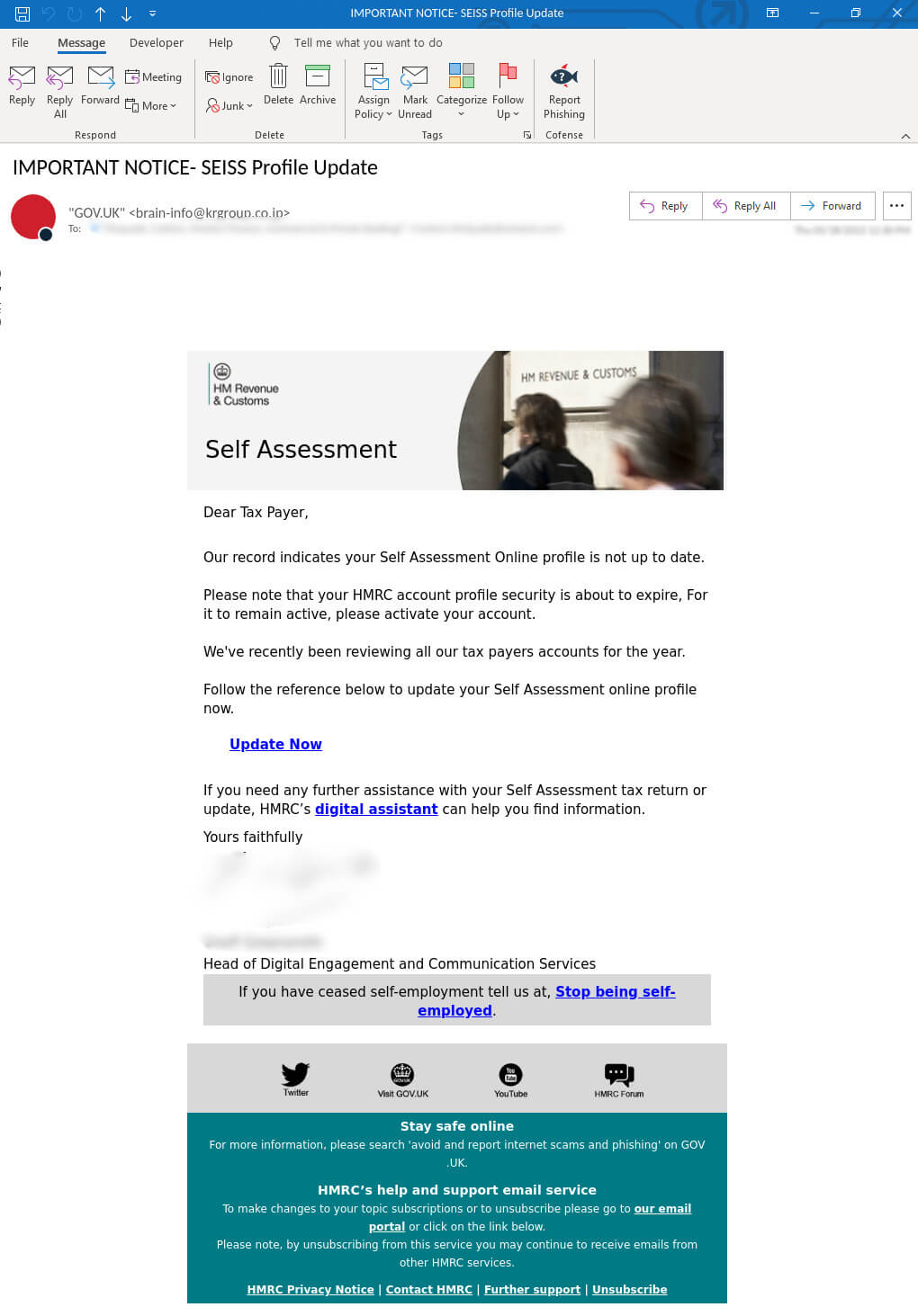
Figure 1 – Email body
Upon clicking the link, it redirects to the webpage illustrated in Figure 2. At first sight, this webpage appears to be the genuine government gateway page, which functions as a centralized registration platform for accessing online government services in the UK. Yet, upon further scrutiny of the URL displayed in the search bar, it becomes apparent that it is a phishing website.
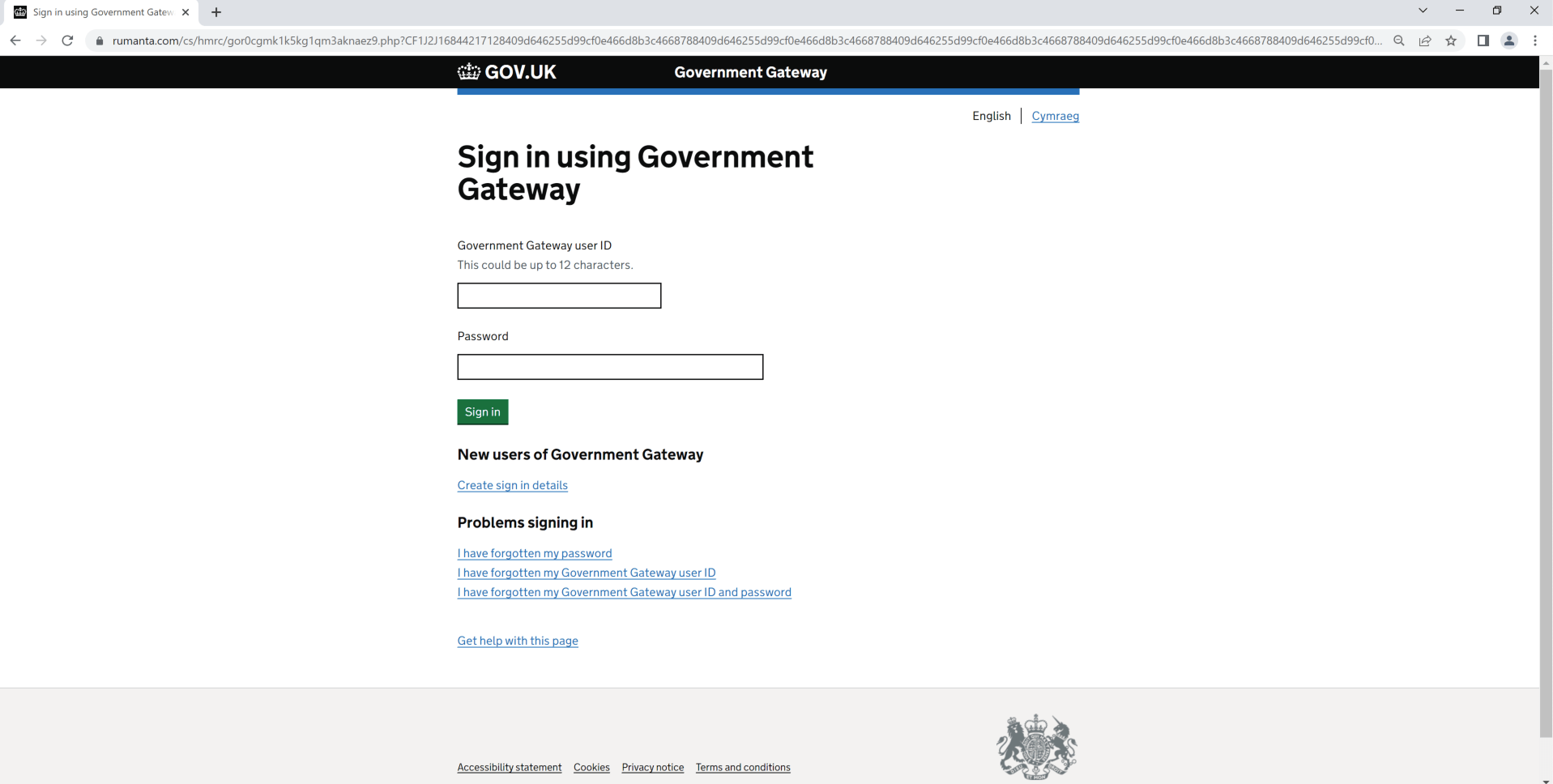
Figure 2 – Phishing Page
Once the fake credentials are entered into the form field, the HTTP POST request is sent to the indicated address shown in Figure 3.The HTTP POST request directed to the URL https://rumanta[.]com/cs/hmrc/_mstr_php?_do=same_form signifies that the entered data in the form is being sent to this specific address to undergo processing. This implies that the submitted information, potentially containing fabricated credentials, is being transmitted to a server hosted at rumanta[.]com. The intention behind this action is to enable the threat actor to manipulate or exploit the received data further. We can confidently affirm that the domain “rumanta[.]com” is experiencing downtime at the time of this writing.
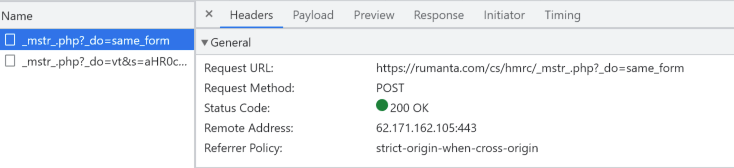
Figure 3 – HTTP POST
It is crucial for individuals to remain vigilant and cautious when handling emails and interacting with online platforms, especially during the self-assessment season. Recognizing the red flags of phishing attempts, such as urgency, suspicious sender addresses, and unusual URLs, is key to safeguarding personal and financial information.
Original Post URL: https://securityboulevard.com/2023/06/unmasking-hmrc-self-assessment-phish-how-attackers-outsmart-secure-email-gateways-segs/
Category & Tags: Security Bloggers Network,Internet Security Awareness|Phishing|Threat Intelligence – Security Bloggers Network,Internet Security Awareness|Phishing|Threat Intelligence
Views: 2