Source: www.techrepublic.com – Author: Cedric Pernet

Several ransomware groups and state-sponsored cyberespionage threat actors are exploiting a vulnerability affecting printing software tools PaperCut MF and PaperCut NG to compromise their targets. The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency issued a joint report detailing this vulnerability, CVE-2023-27350.
The FBI and CISA state there are two publicly known proofs of concept for executing code in vulnerable PaperCut software. The first method consists of using the print scripting interface to execute shell commands. The second one involves using the user/group sync interface to execute a living-off-the-land attack, which is a cyberattack using legitimate software and functions available in the system to perform malicious actions on it. The FBI and CISA state that threat actors may develop other methods for remote code execution.
SEE: Learn how traditional security methods may not cut it for cloud security, according to Palo Alto Networks.
We provide additional technical details about how the cybercriminals are targeting this vulnerability, who is impacted, and how to detect and protect against this security threat.
Jump to:
- What is this PaperCut vulnerability?
- How ransomware groups are actively exploiting this vulnerability
- Microsoft tweets about cyberespionage threat actors
- How to detect this cybersecurity threat
- How to protect from this PaperCut vulnerability threat
What is this PaperCut vulnerability?
The new PaperCut vulnerability, CVE-2023-27350, affects different PaperCut MF and PaperCut NG software, allowing an attacker to bypass authentication and execute arbitrary code with SYSTEM privileges.
A pc-app.exe file on vulnerable PaperCut servers runs with SYSTEM or root-level privileges depending on the configuration and might be exploited to execute other processes such as cmd.exe for command line or powershell.exe for PowerShell scripts. Those child processes benefit from the privileges of the pc-app.exe file, allowing the attackers to run code with high privileges on the server.
PaperCut announced the vulnerability in March 2023 and then updated its website to indicate the company now has evidence to suggest that unpatched servers are being exploited in the wild. A banner at the top of the company’s site features a link to the communication, which is marked as urgent for all PaperCut NG and MF customers. The patch has been available since March 2023.
Another vulnerability affecting PaperCut MF and NG software, CVE-2023-27351, allows an unauthenticated attacker to potentially pull information such as username, full names, email addresses, office information and any card numbers associated with the user. While PaperCut does not have evidence of this vulnerability being used in the wild, a tweet from Microsoft mentions the use of the vulnerability without providing more information about it.
How ransomware groups are actively exploiting this vulnerability
According to the FBI, the Bl00dy ransomware group gained access to victims’ networks across the Education Facilities Subsector, with some of these attacks leading to data exfiltration and encryption of those systems. The threat actor leaves a note on the affected systems asking for payment in cryptocurrency (Figure A).
Figure A

The threat actor exploited the PaperCut vulnerability through the printing interface of the software to download and execute legitimate remote management and maintenance software to achieve their goal. The FBI even identified information relating to the download and execution of malware including DiceLoader, TrueBot and Cobalt Strike beacons; although, it’s unclear about their use yet.
Microsoft Threat Intelligence tweeted about recent attacks exploiting the PaperCut vulnerability to deliver Clop ransomware since April 13, 2023. The group behind that operation is known to Microsoft as Lace Tempest, which previously exploited GoAnywhere and Raspberry Robin to deliver malware. Microsoft also reported about Lockbit deployments using the same vulnerability as the initial compromise vector.
Microsoft tweets about cyberespionage threat actors
With more than 70,000 organizations using PaperCut in more than 200 countries, other threat actors became interested in exploiting this vulnerability. CISA reports that 68% of the U.S.-exposed PaperCut servers (this includes vulnerable and non-vulnerable servers) belong to the Education Facilities Subsector. PaperCut also has customers in local governments, legal, life science, healthcare and higher education, according to its website.
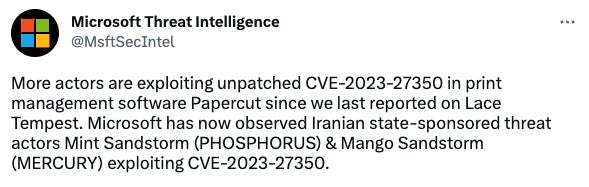
Microsoft tweeted on May 5, 2023, that two Iranian state-sponsored cyberespionage threat actors — Mint Sandstorm (a.k.a., Charming Kitten and Phosphorus) and Mango Sandstorm (a.k.a., Muddy Water, Static Kitten and Mercury) — have quickly adapted the exploit in their operations to achieve initial access after the public proof of concepts were published (Figure B).
Figure B
How to detect this cybersecurity threat
The CISA offers several methods for detecting this cybersecurity threat.
For starters, IT teams should monitor network traffic attempting to access the SetupCompleted page of a vulnerable and exposed PaperCut server; the CISA provides a Proofpoint Emerging Threat Suricata Signature to achieve this detection. PaperCut Application Server logs with debug mode enabled can help identify lines containing SetupCompleted at a time not correlating with the server installation or upgrade, which might be an indication of a compromise.
Any modification of config keys print.script.sandboxed or device.script.sandboxed by the admin user might indicate a compromise and needs to be checked carefully. Modifications of print scripts on printers by the admin or user/group sync settings change might also indicate a compromise.
In addition, domains associated with recent PaperCut exploitation should be searched for in DNS log files. The CISA provides a list of those domains in its report.
On the system monitorings, any child process spawned from a PaperCut server’s pc-app.exe process needs careful monitoring, as it might indicate a successful compromise, especially if it launches post-exploitation tools such as cmd.exe or PowerShell. PaperCut server settings and log files need to be extensively analyzed in search of any compromise.
How to protect from this PaperCut vulnerability threat
You should patch vulnerable PaperCut servers as soon as possible to prevent attackers from exploiting the CVE-2023-27350 vulnerability.
If patching in a timely manner is not possible, you should ensure vulnerable servers are not accessible from the internet. All inbound traffic from external IP addresses to the web management ports, which are 9191 and 9192 by default, should be blocked.
You should apply Allow List restrictions and set to only allow the IP addresses of verified site servers on your network.
As always, all systems and software should be up to date and patched to avoid being compromised by a common vulnerability.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Original Post URL: https://www.techrepublic.com/article/papercut-vulnerability/
Category & Tags: Microsoft,Networking,Security,cybersecurity,papercut,ransomware,vulnerability – Microsoft,Networking,Security,cybersecurity,papercut,ransomware,vulnerability
Views: 1




















































