A rash of printer-related vulnerabilities in 2023 have punctuated security expert warnings that printers continue to be a significant source of vulnerability within companies — especially as remote workers require printing resources or access to corporate printers.
So far in 2023, Lexmark advised that a publicly available remote exploit had already targeted a code execution flaw in its printers, HP warned of a vulnerable firmware version on some of its enterprise printers, and Microsoft fixed three remote code execution vulnerabilities in its printer drivers. And four months ago, security researchers at the Pwn2Own contest in Toronto showed off more than a dozen exploits against bugs in top printer brands, including Canon, HP, and Lexmark.
The spate of vulnerabilities underscores that printers remain a likely soft spot in most companies’ attack surface area, says Matt Lewis, commercial research director at NCC Group, particularly because printers are not always part of company’s asset management process and are often left out of security assessments.
“Many organizations don’t know where their printers are, what security status or configuration they are in, and they are certainly not monitoring or logging activity on those printers,” he says. “We don’t typically see printers featuring as any sort of priority on organizational security plans and risk registers.”
While security researchers have raised the issue of printer vulnerabilities over the past decade or more, the security of printers continues to be a major area of concern for companies. Only a quarter (26%) of information technology and cybersecurity professionals feel completely confident that their printing infrastructure is secure, according to the “Global Print Security Landscape Report 2022” published by technology-analyst firm Quocirca. In addition, 61% of CIOs and 44% of CISOs had difficulty keeping up with print-security challenges and demands, the report stated.
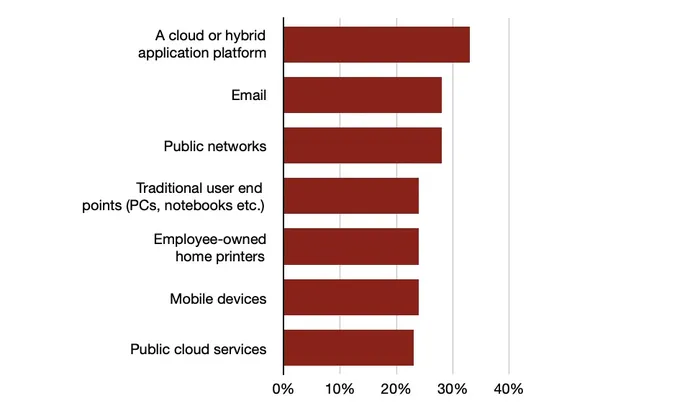
The digital vein of printer vulnerabilities is far from being tapped out, says Dustin Childs, head of threat awareness at Trend Micro’s Zero Day Initiative, which runs the Pwn2Own competition.
“As evidenced by the number of printer-related patches released by Microsoft every month, the attack surface is broad and poorly defended,” he says. “Printers are the sort of devices people don’t want to touch once they get them working. As a consequence, they rarely receive firmware updates or other routine maintenance — at least until something breaks.”
Overlooked Dangers
The hands-off approach to managing printers — or failing to manage printers — can sometimes be a blessing, as in the case of the latest vulnerability in some enterprise HP printer models. On April 3, the company acknowledged a vulnerability in the latest FutureSmart firmware (version 5.6), pulling down the six-week-old software and directing customers to revert their printers to FutureSmart version 5.5.0.3. The devices can leak information when IPSec is enabled, the company said in an advisory.
In a statement to Dark Reading, HP noted that the vulnerability only affected its printers for about a six-week window — between mid-February and the end of March — and only those installed with a specific version of firmware. The company did not say how many customers had downloaded or installed the vulnerable firmware and stated it would patch the latest version and make it available in 90 days.
Overall, printers represent a blind spot in most company’s infrastructure and an opportunity for attackers, says NCC Group’s Lewis.
“Printers can still offer an easy and less-detectable method for attackers to infiltrate a network and remain stealthy via backdoors planted within compromised printers,” he says. “Most modern printers lack security detection and prevention measures and are often not monitored by organizations — for these reasons, there’s no concrete data on how much printer compromise might actually be occurring globally.”
Bringing the Danger Home
A significant twist in the printer threat landscape is the expansion of hybrid work and the commensurate risks posed by employees’ home printers. Nearly two-thirds of companies (67%) are worried that home printers may pose risks to their business’s security, according to the Quocirca report.
Whether home printers are yet getting targeted is not clear, but they do pose a significant attack surface, says NCC Group’s Lewis.
“Home printers … typically lack any organizational configuration and policy lockdown, thus there is a need for organizations to provide useful advice and guidance for home workers on how they can secure their home printers,” he says.
Companies should ensure that their printers — both managed at the office and unmanaged at employees’ homes — are part of their security assessments. Overlooking those devices puts companies at risk, says Trend Micro’s Childs.
“Many enterprises only look at the big printers in their offices if they look at all,” he says. “They rarely consider the printers in the home office of their remote workers when threat modeling.”
Less than four in ten companies have reporting and analytics (38%) or formal risk assessments that include printers (38%) in place, according to the Quocirca report. Nearly nine in 10 companies will have or plan to implement a broad range of printer security measure in 2023, with seven in 10 companies planning to increase spending on security this year, the report stated.
Views: 1




















































