Source: socprime.com – Author: Steven Edwards
Potentially Unwanted Applications (PUAs) like NimScan.exe can silently operate within enterprise environments, probing internal systems or facilitating lateral movement. Detecting these tools early is critical to prevent network-wide compromise.
A SentinelOne detection rule recently analyzed in SOC Prime’s Uncoder AI platform highlights this threat by identifying events where the target process path or IMPhash signature indicates the presence of NimScan.
Detection Logic Overview
This SentinelOne query is designed to trigger when:
- The target process image path contains
NimScan.exe, - OR the process image has one of several known IMPhash values linked to NimScan variants.
These values map to known samples of the PUA and allow for detection even if the executable is renamed or moved.
Input we used (click to show the text)
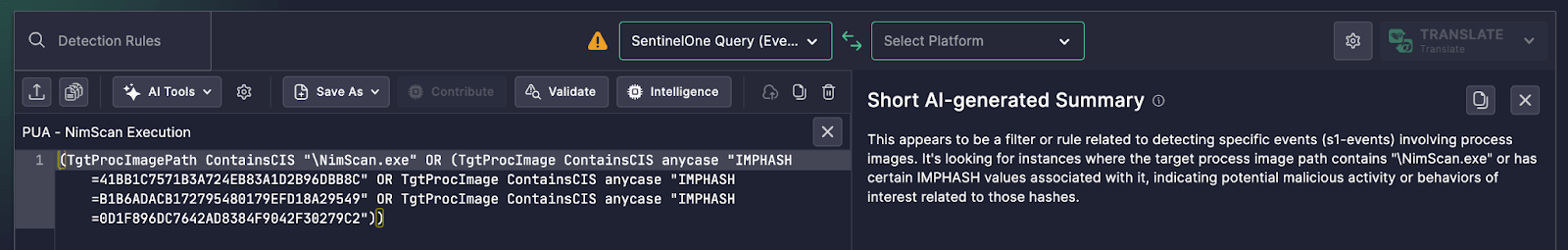
(TgtProcImagePath ContainsCIS "NimScan.exe" OR (TgtProcImage ContainsCIS anycase "IMPHASH=41BB1C7571B3A724EB83A1D2B96DBB8C" OR TgtProcImage ContainsCIS anycase "IMPHASH=B1B6ADACB172795480179EFD18A29549" OR TgtProcImage ContainsCIS anycase "IMPHASH=0D1F896DC7642AD8384F9042F30279C2"))
What Uncoder AI’s Summary Delivered
Uncoder AI’s Short AI-generated Summary translated the rule into a human-readable explanation
This AI-generated context helps security teams understand that the rule detects either:
- A direct match on the file name (NimScan.exe), or
- A hash match on known malicious binaries associated with NimScan.
AI Output (click to show the text)
This appears to be a filter or rule related to detecting specific events (s1-events) involving process images. It's looking for instances where the target process image path contains "NimScan.exe" or has certain IMPHASH values associated with it, indicating potential malicious activity or behaviors of interest related to those hashes.
Why This Matters
- Early PUA Detection: Identifying NimScan early helps stop its use in lateral movement or internal scanning.
- Hash-Based Matching: Even obfuscated or renamed versions of the tool are caught through IMPhash detection.
- Faster Rule Understanding: Analysts no longer need to manually interpret matching conditions—Uncoder AI delivers immediate clarity.
From SentinelOne Syntax to Actionable Insight
Without Uncoder AI, understanding SentinelOne’s rule structure—especially those involving compound hash conditions—requires deep product familiarity. With the Short Summary feature, the detection logic becomes instantly actionable, enabling teams to triage alerts faster and with higher confidence.
Original Post URL: https://socprime.com/blog/detecting-nimscan-activity-in-sentinelone-with-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,NimScan,SentinelOne detection,Uncoder AI – Blog,SOC Prime Platform,NimScan,SentinelOne detection,Uncoder AI
Views: 6




















































