Source: hackread.com – Author: Waqas.
Summary
- Large-Scale Hacking Operation Uncovered: Researchers link ShinyHunters and Nemesis to an operation exploiting millions of websites to steal over 2 terabytes of sensitive data.
- Sophisticated Tools and Tactics: Hackers used Python, PHP, AWS IP ranges, and tools like ffuf, httpx, and Shodan to automate and expand their exploitation across regions.
- Collaborative Mitigation Efforts: Researchers worked with the AWS Fraud Team to notify affected users, implement mitigation measures, and identify individuals involved in selling stolen data on Telegram.
- Critical Discovery in Misconfigured S3 Bucket: An open S3 bucket used by the hackers exposed their stolen data, tools, and even potential identities, offering a unique glimpse into their operations.
- Call for Stronger Cybersecurity Practices: The incident shows the need for proper configurations to protect cloud environments and prevent such large-scale breaches.
Cybersecurity researchers have identified a large-scale hacking operation linked to notorious ShinyHunters and Nemesis hacking groups. In this operation, hackers exploited vulnerabilities in millions of websites and took advantage of misconfiguration to access sensitive information including customer data, infrastructure credentials, and proprietary source code.
According to Noam Rotem and Ran Locar, two independent researchers who conducted this research, these attacks were carried out from a French-speaking country. It is worth noting that one of the ShinyHunters members Le Français Sébastien Raoult (aka Sezyo Kaizen), a France national, was arrested in Morocco back in July 2022. In January 2024, he was sentenced in the US to three years in prison. However, after spending less than a year, the hacker returned to France just last week.
Tools and Tricks
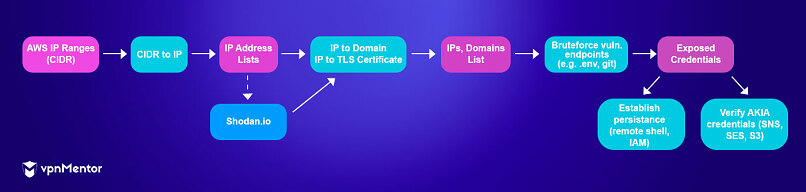
In their report for vpnMentor, researchers explained that the hackers were able to extract critical keys and secrets, which provided them with access to valuable data including application databases. The operation utilised several scripting languages, including Python and PHP, alongside specialized tools like ffuf and httpx, to automate the exploitation process.
Furthermore, the hackers used publicly available AWS IP address ranges to search millions of targets. They also used Shodan, a search engine for internet-connected devices, to perform reverse lookups and identify domain names associated with the discovered IPs. This method especially expanded their reach, allowing them to find and exploit numerous endpoints across different regions.
Researchers then collaborated with the AWS Fraud Team to implement mitigation measures and notify affected customers. The investigation also identified the names and contact information of some individuals behind the incident, assisting in further actions against the culprits who are selling their stolen data in dedicated Telegram channels for hundreds of Euros per breach.
The breach led to the theft of over 2 terabytes of data, including AWS customer keys and secrets that allowed access to various AWS services, as well as database and Git credentials, exposing source code and sensitive databases. SMTP and SMS credentials were also stolen, enabling attackers to send phishing emails and spam messages.
Moreover, cryptocurrency wallets and trading platform credentials were compromised, granting access to digital assets and trading accounts, alongside social media and email accounts, jeopardizing personal and business communications.
Link to ShinyHunters and Nemesis Groups
Investigations traced the infrastructure of this operation back to the ShinyHunters and Nemesis hacking groups because the tools and scripts used by the attackers held similarities to those previously associated with ShinyHunters, a group known for breaches at major companies like Ticketmaster, AT&T, Mashable and many more. The group also owned and administrated the notorious cybercrime and data breach forum Breach Forums for a while.
Additionally, the now-seized Nemesis Blackmarket was identified as a marketplace where the stolen credentials and access keys were being sold, often fetching hundreds of Euros per breach on platforms like Telegram.
Hackers Exposed Their AWS Bucket While Hunting Exposed Databases
One critical discovery was an open Amazon S3 bucket used by the attackers to store harvested data. This bucket acted as a shared storage space, mistakenly left unsecured by its owner, facilitating the easy collection and distribution of stolen information.
“The discovery provided a glimpse into the operations of a large-scale web-scanning operation, the code used by the attackers, and even the potential identities of the people behind it. Data harvested from the victims was stored in an S3 bucket, which was left open due to a misconfiguration by its owner. The S3 bucket was being used as a “shared drive” between the attack group members, based on the source code of the tools used by them. These tools are documented in French and signed by “Sezyo Kaizen”.
Researchers
Jim Routh, Chief Trust Officer at Saviynt, emphasized the scale and technical prowess of these criminal groups stating, “ShinyHunters and Nemesis represent highly organized cybercriminal syndicates operating on a large scale for profit. They exploit vulnerabilities in cloud services, often taking advantage of enterprises that may not fully understand the complexities and security controls of cloud environments. The range of targeted information, from credentials and cryptocurrency wallets to source code and cloud account secrets, shows their broad and opportunistic approach.”
Routh also highlighted the irony that the attackers themselves made a critical mistake by leaving an AWS S3 bucket open, which ultimately led to the detection of their activities.
Nevertheless, this incident shows why proper configuration and implementing cybersecurity practices are important to protect your online infrastructure. It will be interesting to see if the details shared by researchers with authorities lead to arrests or further revelations about the individuals involved in the hacking spree.
Original Post url: https://hackread.com/shinyhunters-nemesis-hacks-aws-s3-bucket-leak/
Category & Tags: Security,Cyber Crime,Cyber Attack,Cybersecurity,Data Breaches,Nemesis,ShinyHunters,Shodan,Ticketmaster – Security,Cyber Crime,Cyber Attack,Cybersecurity,Data Breaches,Nemesis,ShinyHunters,Shodan,Ticketmaster
Views: 2