Source: www.infosecurity-magazine.com – Author:
The November ransomware attack on supplier Blue Yonder that affected large companies like Starbucks, Sainsbury’s and Morrisons has been claimed by the Termite ransomware group.
On its data leak site, the group claims to have stolen 680GB of data, including more than 16,000 email lists that it plans to use for future attacks, and more than 200,000 insurance documents.
Blue Yonder has yet to comment on the ransomware group’s claim but said in a December 6 message that it was working with external cybersecurity experts to address these claims.
Termite has claimed attacks against several organizations across various sectors including government agencies, oil and gas and automotive manufacturing. It was previously responsible for an attack on the government of the French island nation of La Réunion.
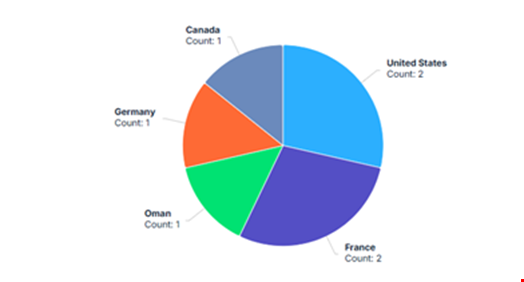
The group has claimed 10 victims worldwide, though many have not yet confirmed whether they were targeted. It seems that the group primarily focuses on Europe and North America.
Reports suggest that the group has been active since April 2024.
A Possible New Babuk Variant
Cyber threat intelligence analysts from Cyble have analyzed binaries from the ransomware implant deployed by Termite.
The threat intelligence provider assessed that the new ransomware group is essentially a rebranding of the notorious Babuk ransomware.
Broadcom has also noted the link between Termite and Babuk. It described the Termite logo as featuring a blue stylized termite integrated with circuit-like pathways.
Mikhail Pavolvich Matveev, aka WazaWaka, was allegedly arrested by the Russian authorities in early December. A 2023 US indictment described him as the leader of the Babuk ransomware group.
How Termite Ransomware Infects Victim’s Devices
Upon execution, the Termite ransomware uses the SetProcessShutdownParameters API to delay termination during system shutdown, maximizing encryption time. It also attempts to stop services on the victim’s machine by connecting to the Service Control Manager with the OpenSCManagerA() API, preventing disruptions during encryption.
After gaining access, the ransomware enumerates the services on the victim’s machine to retrieve their names, specifically looking for Microsoft’s Virtual Machine Management service (VMMS) or virtual machine backup and recovery systems like Veeam’s.
The ransomware enumerates running processes and terminates some if they’re shown to be running.
It then runs several processes to prevent system recovery and delete all files from the ‘Recycle Bin’ to ensure the victim cannot recover any files after encryption.
After scanning for processors running on the targeted device, Termite ransomware generates a ransom note for each detected CPU titled “How To Restore Your Files.txt”, encrypts files on the victim’s machine and appends the “.termite” extension.

Like Babuk ransomware, Termite also appends the signature “choung dong looks like hot dog” at the end of the encrypted file.
Cyble’s Mitigation Recommendations
Cyble analysts have listed some essential cybersecurity best practices to mitigate the threat of Termite ransomware. These include:
- Avoid opening untrusted links and email attachments without first verifying their authenticity
- Conducting regular backup practices and keeping those backups offline or in a separate network
- Tuning on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic
- Using a reputable antivirus and Internet security software package on your connected devices, including PC, laptop, and mobile
Original Post URL: https://www.infosecurity-magazine.com/news/termite-ransomware-blue-yonder/
Category & Tags: –
Views: 1



















































