Source: www.bleepingcomputer.com – Author: Sponsored by Wazuh

The concept of containerization has changed how applications are deployed and managed, offering flexibility and scalability. These changes have made compliance with security standards in containerized environments an important area of focus.
Maintaining visibility into container hosts, ensuring adherence to best practices, and conducting vulnerability assessments are some concerns in ensuring effective security.
This article will explore how Wazuh helps implement best security practices for containerized environments.
What are containers? They are lightweight, portable units that package an application and its dependencies, enabling consistent operation across different computing environments.
Examples of container technologies include Docker, Kubernetes Pods, LXC, and Windows containers.
Container security challenges
The increased adoption of containerized technologies presents challenges stemming from the dynamic nature and scale of containerized workloads. Key issues in achieving regulatory compliance for container environments include:
- Container visibility: Achieving compliance requires enterprises to have visibility across all their workloads, but understanding what container workloads are running, where they are running, and how they are configured may be challenging, especially at large scale. In some environments, workloads are spread across public and private clouds, and images may come from multiple sources. These issues, along with varying configurations, make visibility more difficult.
- Implementing granular access controls: Many regulatory standards require enterprises to implement granular access controls to prevent unauthorized access to sensitive data or system compromise. For example, PCI DSS requires enterprises to restrict access to cardholder data in a manner that is according to the principle of least privilege. Such a requirement solidifies the need for compliance even within containerized environments
- Managing vulnerabilities in external libraries and images: Container images pulled from untrusted repositories or third-party libraries and dependencies can introduce vulnerabilities to containerized environments. Enterprises need a plan to mitigate this risk and remain compliant.
Wazuh for container security
Wazuh is a free, open source security platform that offers unified XDR and SIEM capabilities across workloads in cloud and on-premises environments. The Wazuh platform offers capabilities like log data analysis, file integrity monitoring, threat detection, real-time alerting, and incident response.
Wazuh helps to meet regulatory compliance requirements like PCI DSS 4.0 requirements 10.2.4 and 10.2.5, and NIST SP 800-190 for Docker containers in the following ways:
- File integrity monitoring (FIM): Wazuh provides FIM to monitor the integrity of container images and other critical files, ensuring that unauthorized changes are promptly detected and reported.
- Configuration auditing: Wazuh audits container host configurations to meet compliance standards, identify misconfigurations, and ensure that security standards are followed.
- Vulnerability scanning: Wazuh integrates with vulnerability assessment tools to scan container images for known vulnerabilities, helping organizations mitigate risks and maintain compliance with security standards.
- Log analysis: Wazuh analyzes container logs for security events and anomalies, enabling organizations to identify threats and take appropriate action to address them.
- Malware detection: Wazuh includes malware detection capabilities, enhancing container security by identifying and mitigating threats from malicious software.
- Active response: Wazuh provides active response capabilities to execute actions like firewall blocking or account lockouts in response to security incidents. Wazuh ensures regulatory compliance by swiftly addressing security events in container hosts and enforcing security controls against evolving threats.
Monitoring Docker containers
Wazuh facilitates Docker container monitoring by installing the Wazuh agent on the Docker server and enabling the Wazuh Docker listener. This setup allows for collecting Docker-related logs and security events, ensuring effective container activity monitoring and incident detection.
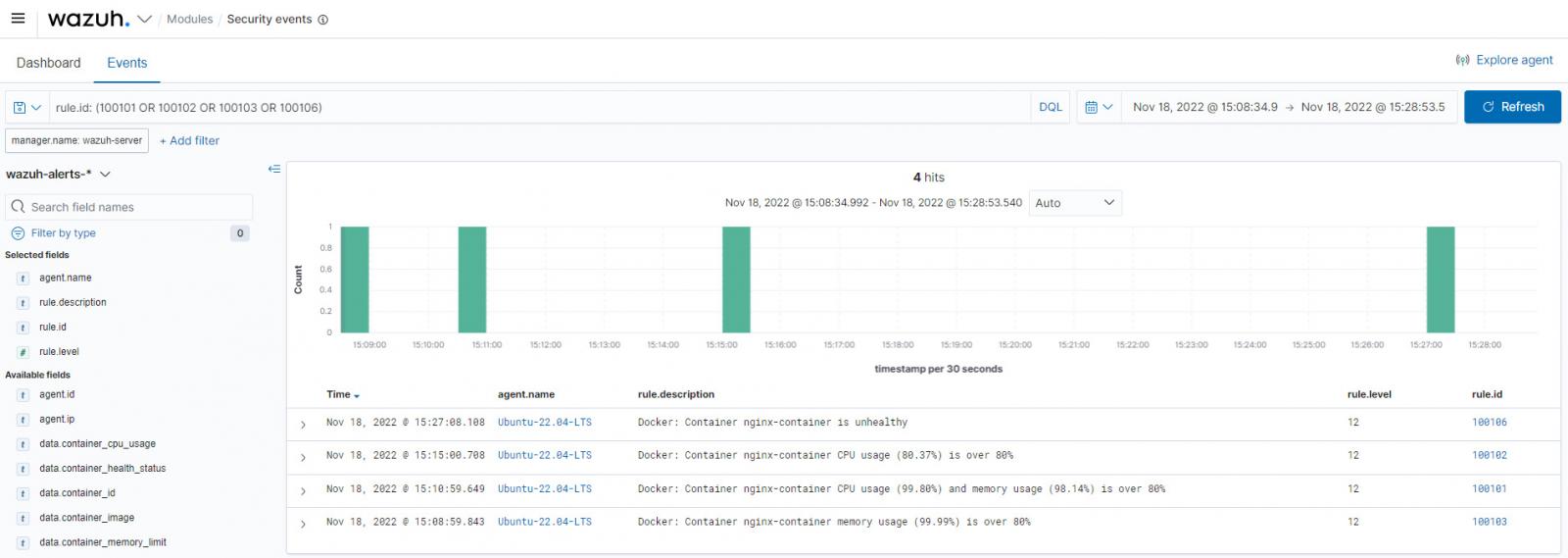
Wazuh actively monitors the runtime, application logs, and resource utilization in containerized environments. Wazuh provides real-time insights into container resource consumption, for instance, when container CPU and memory usage exceeds predefined thresholds.
This comprehensive monitoring with Wazuh enables prompt issue resolution, enhances security, and optimizes operational efficiency in Docker environments.
The image below shows when Wazuh detects Docker CPU and memory usage exceeding the defined threshold, as seen on the Wazuh dashboard.
Auditing Kubernetes
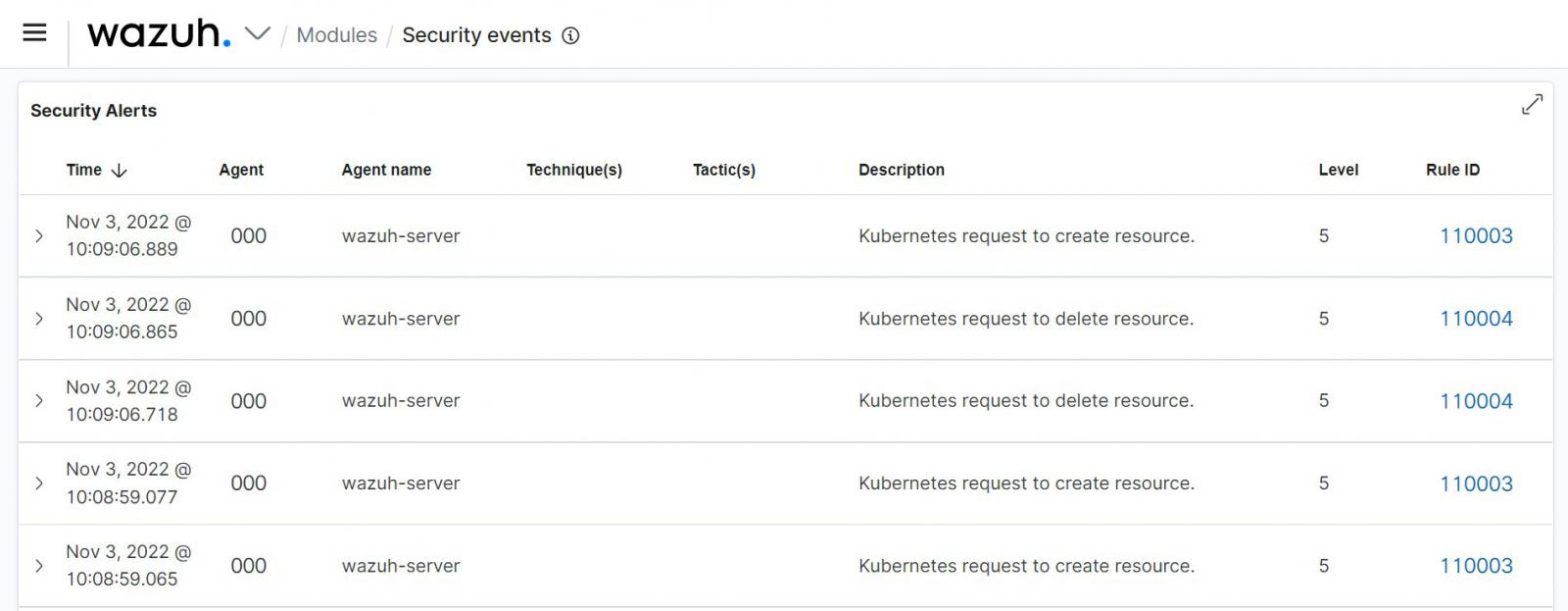
Wazuh monitors Kubernetes using a webhook listener set up on the Wazuh server to receive logs from the Kubernetes cluster. Auditing Kubernetes with Wazuh ensures real-time monitoring, storage, and indexing of Kubernetes audit logs.
This provides data search and analytics capabilities for detecting security threats.
The image below shows alerts triggered when resources were created and deleted on a Kubernetes cluster monitored by Wazuh.
Container vulnerability scanning
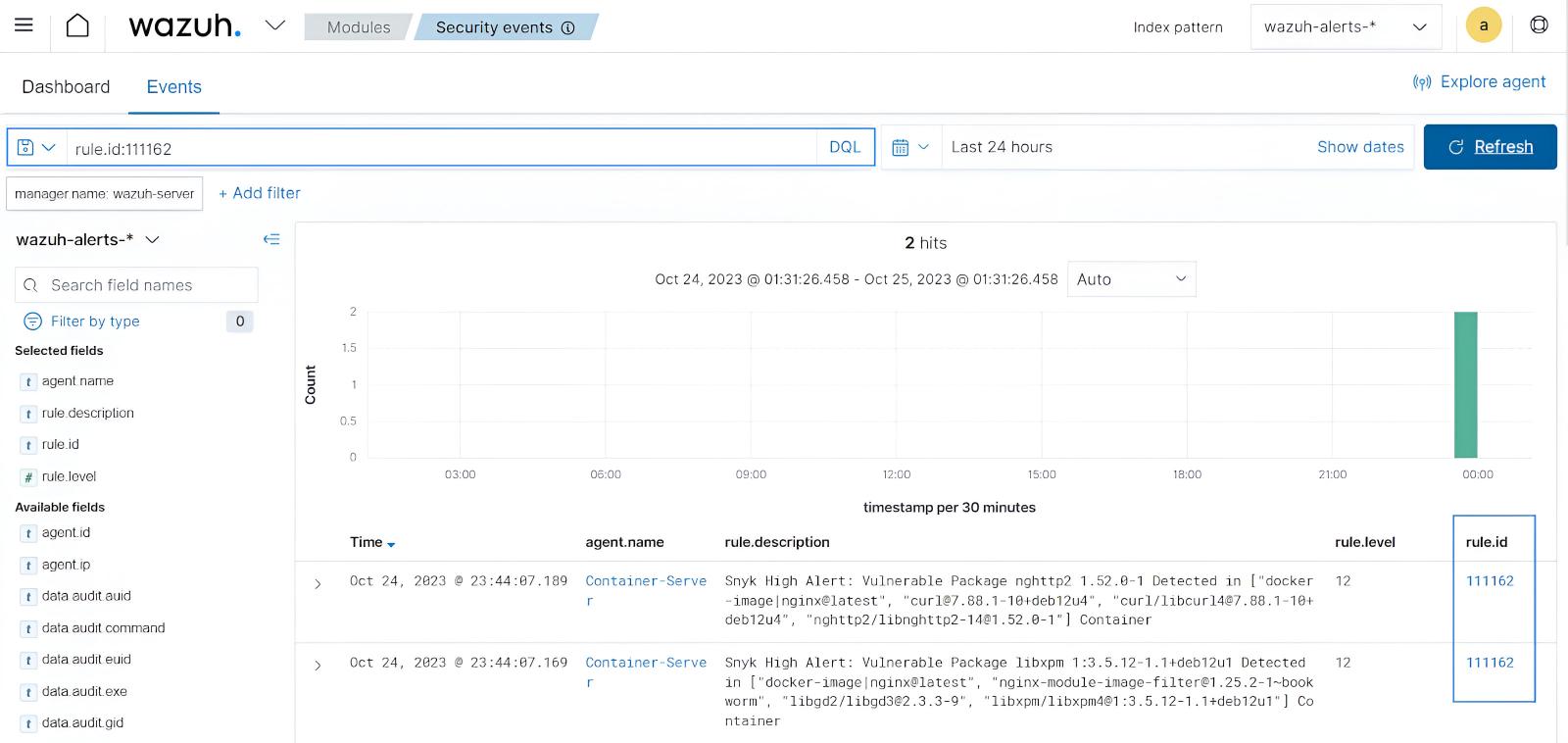
Wazuh enables container vulnerability scanning by integrating with a vulnerability assessment tool to conduct scans within container environments. This process includes executing custom bash scripts via the Wazuh command capability to trigger the vulnerability assessment tools for scans.
Custom rules are configured on the Wazuh server to monitor the outcome of the scan conducted at the endpoint.
The Wazuh agent monitors and forwards the vulnerability scan logs to the Wazuh server, enabling organizations to promptly identify and remediate vulnerabilities within their container environments.
Conclusion
Maintaining security compliance is important for mitigating risks and ensuring best practices within containerized environments.
Wazuh aids this effort by providing visibility into container security, threat detection and response, and insights into various standards and frameworks.
Wazuh is an open source and easy-to-deploy solution that simplifies regulatory compliance, making it an essential asset for organizations striving to maintain a secure and compliant environment.
Compliance with container best practices is a shared responsibility, and Wazuh streamlines the process, ensuring businesses stay protected and resilient.
Join the Wazuh community to get started.
Sponsored and written by Wazuh.
Original Post URL: https://www.bleepingcomputer.com/news/security/implementing-container-security-best-practices-using-wazuh/
Category & Tags: Security – Security
Views: 2




















































