Source: www.infosecurity-magazine.com – Author: 1
Google’s Threat Analyst Group has confirmed that Iran-backed hackers have used their cyber capabilities to undercut public support for the Israel-Hamas conflict in the US and Israel.
In Tool of First Resort: Israel-Hamas War in Cyber, a joint threat intelligence report published on February 14, Google’s Threat Analyst Group (TAG) and Mandiant found that Iranian adversaries accounted for 80% of all government-backed phishing activity that targeted users based in Israel in the six months leading up to Hamas’s attack.
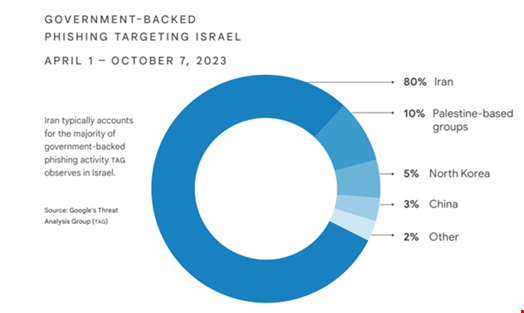
The Iran-backed groups observed to be active during the analyzed period are familiar to the Google researchers, Mandiant Intelligence’s VP, Sandra Joyce, said during a press conference.
Some of these include APT32 (aka Charming Kitten, Mint Sandstrom), Dusty Cave (aka Imperial Kitten, Crimson Sandstorm) and Dune (aka Banished Kitten, STORM-0842).
In 2023, these threat groups aggressively targeted US and Israeli entities, often with mixed results.
Google researchers found that Iranian adversaries consistently tried to emphasize and often exaggerate the impact of those attacks.
“On more than one occasion, for targets that were not exceptionally impactful, threat actors tried to come up with something that appeared as something more than it actually was,” Joyce explained.
Focused Efforts to Undercut Public Support for the Israel-Hamas War
After the October 7 attack Hamas conducted against Israel, Iran-backed threat groups’ tactics shifted to focus even more on Israel, and the tempo of attacks increased significantly.
“From October 2023, we have seen a focused effort to undercut public support for the war,” the report reads.
Some of these groups’ cyber activity following the Hamas attack included:
- Destructive attacks against key Israeli organizations
- Hack-and-leak operations, including exaggerated claims of attacks against critical infrastructure in Israel and the US
- Information operations (IO) to demoralize Israeli citizens, erode trust in critical organizations and turn global public opinion against Israel
- Phishing campaigns directed toward users based in Israel and the US to collect intelligence on critical decision-makers

Aside from this Iranian activity uptick, the days following the October 7 attack was not associated with a general spike in adversary cyber activity, Google researchers found.
“We saw nothing like what we observed during and after the 2022 Russian invasion of Ukraine,” Joyce said.
Cyber Espionage Campaigns Ongoing
For years, pro-Hamas hackers have been observed conducting a mix of intra-Palestine targeting, as well as regular targeting of Israel, the US, Europe and countries neighboring Israel and Palestine.
Google TAG and Mandiant found that some of these Hamas-linked groups, such as Blackstem (aka Molerats, Extreme Jackal) and Desert Varnish (aka Desert Falcons, Arid Viper, Renegade Jackal) have also been conducting cyber espionage campaigns throughout 2023 to collect intelligence from targets within the Palestinian Territories and Israel prior to the October 7 attack.
They have been using “simple-but-effective” techniques, tactics and procedures (TTPs), added the researchers.
These TTPs include mass phishing campaigns targeting users in Palestine and its regional neighbors as well as persistent efforts to target Israeli entities using a variety of custom and open-source cyber capabilities, including Android malware and spyware.
One campaign, conducted by Blackatom in September 2023, showed signs of more advanced capabilities, including elaborate social engineering tailored to software engineers and custom malware developed for Windows, Mac, and Linux.
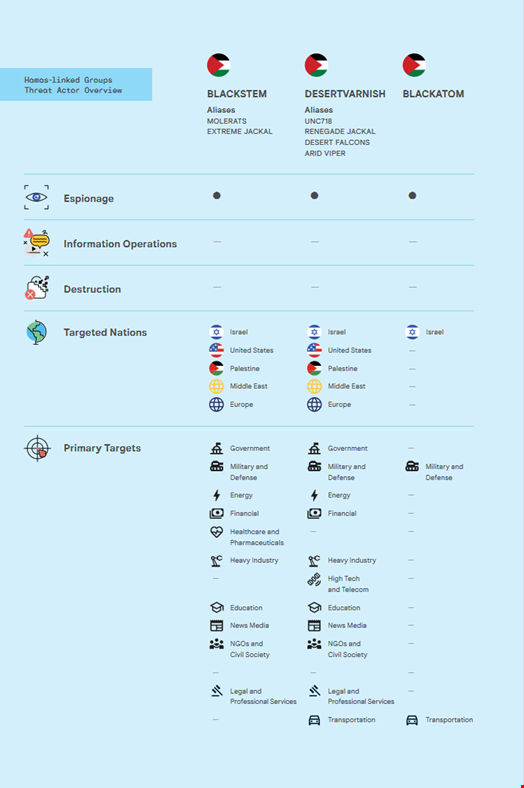
Nevertheless, the researchers assessed that Hamas did not use cyber operations to tactically support the October 7 attack.
Unattributed Predatory Sparrow Targeted Iran
Finally, Google’s researchers found that in at least one instance in 2023, Iranian critical infrastructure was disrupted by an actor claiming to be responding to the conflict.
The threat group, calling themselves “Gonjeshke Darande” (Predatory Sparrow) claimed it had taken a majority of gas stations in Iran offline, attacking their infrastructure and payment systems.
Although Iran has attributed this activity to Israel, Google researchers said they do not have sufficient evidence to evaluate these claims or give any attribution at this point.
John Hultquist, Mandiant Intelligence’s chief analyst, commented: “There have been discussions about the level of resources necessary to conduct this and previous attacks attributed to Predatory Sparrow, which could lead to thinking it’s a skilled adversary, but I would be careful not to draw any conclusions.”
Google’s Cyber Threat Predictions for 2024
Based on their observations, Google’s researchers provided some forward-looking assessments regarding these threat actors for 2024. These include:
- Iran-linked groups are likely to continue to conduct destructive cyber-attacks, particularly in the event of any perceived escalation to the conflict, to include kinetic activity against Iranian proxy groups in various countries, such as Lebanon and Yemen.
- Hack-and-leak operations and information operations will remain key components in these efforts to telegraph intent and capability throughout the war, both to Iran’s adversaries and to other audiences that they seek to influence.
- While the outlook for future cyber operations by Hamas-linked actors is uncertain in the near term, we anticipate Hamas cyber activity will eventually resume, with a focus on espionage for intelligence gathering on intra-Palestine affairs, Israel, the US, Europe, and other regional players in the Middle East.
Original Post URL: https://www.infosecurity-magazine.com/news/iran-target-israel-sway-public/
Category & Tags: –
Views: 1




















































