Source: www.mcafee.com – Author: Jasdev Dhaliwal. You consider yourself a responsible person when it comes to taking care of your physical possessions. You’ve never left your wallet in...
Day: January 31, 2025
LevelBlue SOC Analysts See Sharp Rise in Cyber Threats: Stay Vigilant – Source:levelblue.com
Source: levelblue.com – Author: hello@alienvault.com. This holiday season our SOC analysts have observed a sharp uptick in cyber threat activity. Specifically, they’ve seen a rise in...
Cyble’s Weekly Vulnerability Update: Critical SonicWall Zero-Day and Exploited Flaws Discovered – Source:cyble.com
Source: cyble.com – Author: daksh sharma. Overview Cyble’s weekly vulnerability insights to clients cover key vulnerabilities discovered between January 22 and January 28, 2025. The findings...
The Big Short on Cybersecurity – Source: go.theregister.com
Source: go.theregister.com – Author: Stephen Tutterow, Sales Engineer Team Lead at Pentera Partner Content Have you ever watched ? It’s one of my all-time favorite movies,...
Another banner year for ransomware gangs despite takedowns by the cops – Source: go.theregister.com
Source: go.theregister.com – Author: Jessica Lyons If the nonstop flood of ransomware attacks doesn’t already make every day feel like Groundhog Day, then a look back...
Google to Iran: Yes, we see you using Gemini for phishing and scripting. We’re onto you – Source: go.theregister.com
Source: go.theregister.com – Author: Iain Thomson Google says it’s spotted Chinese, Russian, Iranian, and North Korean government agents using its Gemini AI for nefarious purposes, with...
AI-Generated Content: How Cybercriminals Are Using It for Phishing Scams – Source:hackread.com
Source: hackread.com – Author: Waqas. AI-generated content is empowering even novice hackers to elevate phishing attacks, enabling highly personalized and convincing scams targeting unsuspecting users. Learn...
Operation Talent: Two Arrested as Authorities Dismantle Cracked and Nulled – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Global law enforcement seizes 12 domains including Sellix, Cracked and Nulled, €300,000 in cash and cryptocurrencies, and multiple servers in...
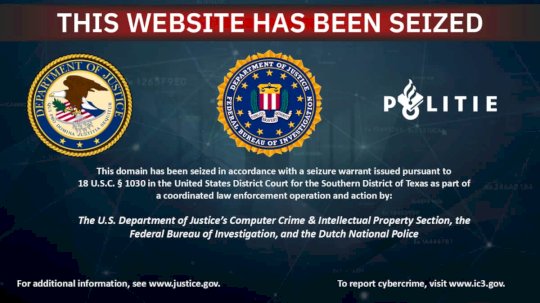
HeartSender Cybercrime Network Dismantled in Joint US-Dutch Operation – Source:hackread.com
Source: hackread.com – Author: Waqas. Massive Pakistani cybercrime network HeartSender has been shut down in a joint US-Dutch operation. Learn how their phishing kits and other...
FUNNULL Unmasked: AWS, Azure Abused for Global Cybercrime Operations – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Cybersecurity firm Silent Push has identified a new cybercriminal tactic called “Infrastructure Laundering.” Researchers say this technique is becoming more...
Threat Actors Target Public-Facing Apps for Initial Access – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Threat actors are increasing their focus on exploiting public-facing applications to achieve initial access, according to Cisco Talos’ Incident Response Trends in...
Tata Technologies Hit by Ransomware Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Tata Technologies Limited, a subsidiary of the Indian conglomerate Tata Group, has been the victim of a ransomware attack affecting some of...
DeepSeek’s Flagship AI Model Under Fire for Security Vulnerabilities – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: R1, the latest large language model (LLM) from Chinese startup DeepSeek, is under fire for multiple security weaknesses. The company’s spotlight on...
International Operation Dismantles Cracked and Nulled Cybercrime Hubs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A major law enforcement operation has taken down two of the world’s largest cybercrime forums, Cracked and Nulled. The global operation was...
In Other News: Browser Syncjacking, Fake AWS Hack, Google Blocked 2M Bad Apps – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide...
Italy Blocks Access to the Chinese AI Application DeepSeek to Protect Users’ Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Italy’s data protection authority on Thursday blocked access to the Chinese AI application DeepSeek to protect users’ data and announced...
US, Dutch Authorities Disrupt Pakistani Hacking Shop Network – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Authorities in the US and the Netherlands on Thursday announced the disruption of a Pakistan-based network of illicit online marketplaces...
2 Arrested in Takedown of Nulled, Cracked Hacking Forums – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Two individuals have been arrested in the law enforcement operation against the notorious Nulled and Cracked cybercrime forums. Reports of...
New York Blood Bank Hit by Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire New York Blood Center Enterprises (NYBCe) this week announced that it has taken certain systems offline after falling victim to...
CISA, FDA Warn of Dangerous Backdoor in Contec Patient Monitors – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The cybersecurity agency CISA and the FDA have urged healthcare organizations in the United States to remove any Contec CMS8000...
ChatGPT, DeepSeek Vulnerable to AI Jailbreaks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Several research teams this week demonstrated jailbreaks targeting several popular AI models, including OpenAI’s ChatGPT, DeepSeek, and Alibaba’s Qwen. Shortly...
NorthBay Health Data Breach Impacts 569,000 Individuals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Non-profit healthcare system NorthBay Healthcare Corporation (NorthBay Health) is notifying over 569,000 individuals that their personal information was stolen in...
How an Improper Access Control Vulnerability Led to Account Theft in One Click – Source:www.hackerone.com
Source: www.hackerone.com – Author: Sandeep Singh. It’s in the name: users gain access to data or systems for which they are not authorized due to improper...
How an Information Disclosure Vulnerability Led to Critical Data Exposure – Source:www.hackerone.com
Source: www.hackerone.com – Author: Sandeep Singh. Upon seeing the term “information disclosure” in the context of security vulnerabilities, most will likely identify this as a risk....
How a Business Logic Vulnerability Led to Unlimited Discount Redemption – Source:www.hackerone.com
Source: www.hackerone.com – Author: Sandeep Singh. Business logic vulnerability: a type of vulnerability that arises due to flaws or inconsistencies in the way it enforces business...
Vulnerability Deep Dive: Gaining RCE Through ImageMagick With Frans Rosen – Source:www.hackerone.com
Source: www.hackerone.com – Author: Andrew Pratt. Applications can be compromised when files are not uploaded to the server’s file system in a secure manner. If a...
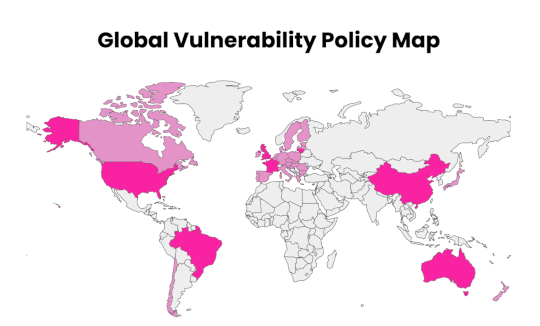
How To Use HackerOne’s Global Vulnerability Policy Map – Source:www.hackerone.com
Source: www.hackerone.com – Author: mwoolslayer@hackerone.com. Thousands of organizations have already adopted vulnerability disclosure programs (VDPs) because they work. They are a proven and fundamental best practice...
European Council Adopts Cyber Resilience Act – Source:www.hackerone.com
Source: www.hackerone.com – Author: Ilona Cohen. The EU Council adopted the Cyber Resilience Act (CRA) this week. Here’s where we’re headed and what HackerOne believes should...
Measure Your AI Risk Preparedness with This Interactive Self-Assessment Tool – Source:www.hackerone.com
Source: www.hackerone.com – Author: Naz Bozdemir. Generative Artificial Intelligence (GenAI) is transforming industries worldwide, but its rapid adoption brings unprecedented security risks. According to the 2024 SANS...
The Recruitment Process: What to Expect When You Apply at HackerOne – Source:www.hackerone.com
Source: www.hackerone.com – Author: Marina Briones. At HackerOne, recruitment is more than just filling a position—it’s about welcoming new members into a community that shares our...