Source: www.securityweek.com – Author: Associated Press The information display screens at Beirut’s international airport were hacked by domestic anti-Hezbollah groups. The post Lebanon Airport Screens Display...
Year: 2024
Vulnerability Handling in 2023: 28,000 New CVEs, 84 New CNAs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A total of more than 28,000 CVE IDs were assigned in 2023 and 84 new CVE Numbering Authorities (CNAs) were...
The latest cyber kidnapping victim, U.S. exchange student – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the U.S. state of Utah, police discovered a teenage Chinese exchange student alone in a freezing cold tent,...
New Research: Tackling .NET Malware With Harmony Library – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have recently unveiled strategic insights into countering .NET malware through the innovative use of the Harmony library. The research,...
Anti-Hezbollah Groups Hack Beirut Airport Screens – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Beirut’s international airport faced a cyber-attack on Sunday, January 8, reportedly orchestrated by domestic anti-Hezbollah groups. The attack comes amid escalating tensions...
Turkish APT Sea Turtle Resurfaces, Spies on Dutch IT Firms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Sea Turtle, a group of hackers aligned with the Turkish government, has returned after going undetected since 2020. Dutch cybersecurity provider,...
North Korean Hackers Stole $600m in Crypto in 2023 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 North Korean hackers stole at least $600m in cryptocurrency in 2023, around a third of the total value of such heists,...
Merck Settles With Insurers Over $700m NotPetya Claim – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Merck has finally reached a settlement with its insurers after they had refused to pay out following the NotPetya campaign due...
Security Firm Certik’s Account Hijacked to Spread Crypto Drainer – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Web3 security vendor was tricked by a social media phishing attack which hijacked its account and enabled scammers to share...
US, Israel Used Dutch Spy to Launch Stuxnet Malware Against Iran – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 1 Min Read Source: Mohammad Aaref Barahouei via Alamy Stock Photo After a two-year investigation into the...
Cacti Monitoring Tool Spiked by Critical SQL Injection Vulnerability – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Nate Hovee via Shutterstock A critical vulnerability in the Cacti Web-based open source framework for monitoring network...
Turkish APT ‘Sea Turtle’ Resurfaces to Spy on Kurdish Opposition – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Marius Graf via Alamy Stock Photo A group aligned with the interests of the government of Turkey...
‘Swatting’ Becomes Latest Extortion Tactic in Ransomware Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading 1 Min Read Source: Nipiphon Na Chiangmai via Alamy Stock Photo Using a tactic known as...
Beirut Airport Cyberattack Targets Hezbollah – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden Source: Leonid Andronov via Alamy Stock Photo Screen displays at the Rafic Hariri International Airport in Lebanon were defaced with...
Protecting Critical Infrastructure Means Getting Back to Basics – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Lancaster Jr. Source: Andrii Yalanskyi via Alamy Stock Photo Critical infrastructure organizations are undergoing dramatic changes in their technology and cybersecurity...
Iranian Crypto Exchange Misstep Exposes User Details – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: gabriel cassan via Alamy Stock Photo A misconfigured object storage system used by Iranian crypto exchange bit24.cash has...
Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 08, 2024NewsroomMalware / Cybercrime Threat actors operating under the name Anonymous Arabic have released a remote access trojan (RAT) called...
Swiss Air Force sensitive files stolen in the hack of Ultra Intelligence & Communications – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Swiss Air Force sensitive files stolen in the hack of Ultra Intelligence & Communications Documents belonging to the Swiss Air...
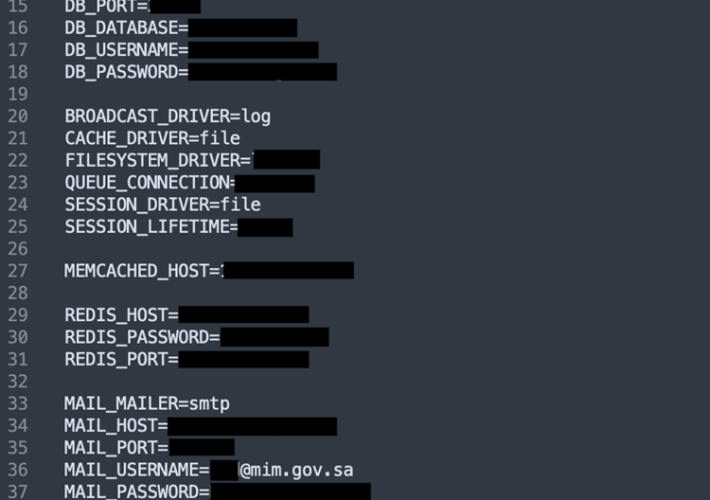
Saudi Ministry exposed sensitive data for 15 months – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Saudi Ministry exposed sensitive data for 15 months Saudi Ministry of Industry and Mineral Resources (MIM) had an environment file...
DoJ charged 19 individuals in a transnational cybercrime investigation xDedic Marketplace – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini DoJ charged 19 individuals in a transnational cybercrime investigation xDedic Marketplace 19 individuals worldwide were charged in a transnational cybercrime...
Long-existing Bandook RAT targets Windows machines – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Long-existing Bandook RAT targets Windows machines A new variant of the Bandook remote access trojan (RAT) was spotted in attacks...
Grab 9 Ethical Hacking Courses for $25 and Improve Your Business Security – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 8, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Secure Browser Usage Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: A web browser is an indispensable feature of every computer and, in some cases, the only truly essential feature (such as with...
Hackers hijack Beirut airport departure and arrival boards – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley On Sunday evening electronic departure boards at Beirut’s airport were hijacked by hackers who used them to display anti-Iranian and...
Stuxnet: The malware that cost a billion dollars to develop? – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley A report from the Netherlands claims that a Dutch man played a key role in the notorious Stuxnet worm attack...
Second Interdisciplinary Workshop on Reimagining Democracy – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Last month, I convened the Second Interdisciplinary Workshop on Reimagining Democracy (IWORD 2023) at the Harvard Kennedy School Ash Center....
US mortgage lender loanDepot confirms ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Leading U.S. mortgage lender loanDepot confirmed today that a cyber incident disclosed over the weekend was a ransomware attack that led...
Capital Health attack claimed by LockBit ransomware, risk of data leak – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The LockBit ransomware operation has claimed responsibility for a November 2023 cyberattack on the Capital Health hospital network and threatens...
Securing helpdesks from hackers: What we can learn from the MGM breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software In the wake of the MGM Resorts service desk hack, it’s clear that organizations need to rethink their...
NIST Warns of Security and Privacy Risks from Rapid AI System Deployment – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 08, 2024NewsroomArtificial Intelligence / Cyber Security The U.S. National Institute of Standards and Technology (NIST) is calling attention to the...