Source: www.bleepingcomputer.com – Author: Bill Toulas The Turkish state-backed cyber espionage group tracked as Sea Turtle has been carrying out multiple spying campaigns in the Netherlands, focusing...
Year: 2024
Twilio will ditch its Authy desktop 2FA app in August, goes mobile only – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Authy desktop apps for Windows, macOS, and Linux will be discontinued in August 2024, with the company recommending users...
Meet Ika & Sal: The Bulletproof Hosting Duo from Hell – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In 2020, the United States brought charges against four men accused of building a bulletproof hosting empire that once dominated the...
Alert: New Vulnerabilities Discovered in QNAP and Kyocera Device Manager – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024NewsroomNetwork Security / Data Protection A security flaw has been disclosed in Kyocera’s Device Manager product that could be...
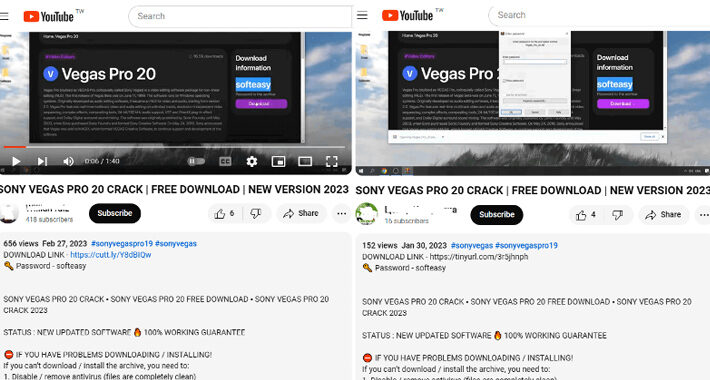
Beware! YouTube Videos Promoting Cracked Software Distribute Lumma Stealer – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024NewsroomMalware / Cyber Threat Threat actors are resorting to YouTube videos featuring content related to cracked software in order...
Guide to Malware Incident Prevention and Handling for Desktops and Laptops
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
LLM AI Security & Governance Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
IT AUDIT CHECKLIST
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Kubernetes Exploitation Introduction -Cheatsheet #1
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Incident Response Playbook: Dark Web Breaches
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Life in the Swimlane with Principal Data Scientist, Dima Skorokhodov – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelly Dougherty Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
Ditch the Passwords: Discover the Magic of WebAuthn and Passkeys – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author In today’s digital age, passwords have become a necessary evil. We rely on them to...
USENIX Security ’23 – ‘Know Your Cybercriminal: Evaluating Attacker Preferences by Measuring Profile Sales on an Active, Leading Criminal Market for User Impersonation at Scale’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Michele Campobasso, Luca Allodi Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the...
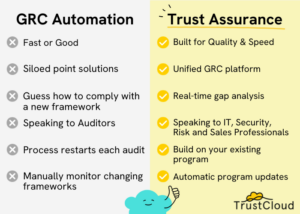
The CISO’s Guide to a Modern GRC Program with Trust Assurance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Erin Crapser The position of CISO is not an enviable one. Modern CISOs face enormous challenges like managing the complexity of on-prem...
Mastering the ‘cd’ Command: Tips and Tricks for Efficient Directory Navigation – Source: securityboulevard.com
Source: securityboulevard.com – Author: CyB3rBEA$T Navigating through directories is a fundamental aspect of working in a command-line interface, and the ‘cd’ command plays a crucial role...
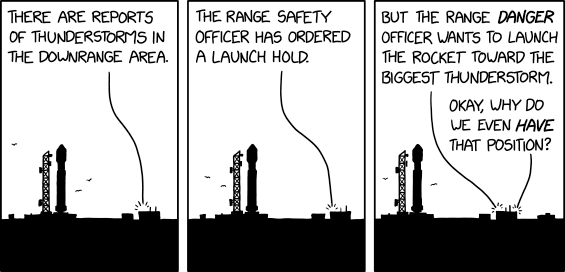
Randall Munroe’s XKCD ‘Range Safety’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Secure Your Secrets with .env – Source: securityboulevard.com
Source: securityboulevard.com – Author: Greg Bulmash Using environment variables to store secrets instead of writing them directly into your code is one of the quickest and...
NIST: Better Defenses are Needed for AI Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The accelerating development and expanding deployment of AI systems is creating significant security and privacy risks that aren’t being mitigated...
NIS2 Compliance: Updated for 2024, Complete Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare The Network Information Systems Directive (NIS) was published in 2016 and required EU critical infrastructure sectors to meet basic cybersecurity compliance...
USENIX Security ’23 – Zixin Wang, Danny Yuxing Huang, Yaxing Yao – ‘Exploring Tenants’ Preferences of Privacy Negotiation in Airbnb’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
NYS: Clinic Must Pay $450K Fine, Spend $1.2M on Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific State AG Settlement Comes After 2021 Lorenz Ransomware Attack on Health Center...
Live Webinar | Securing the Cloud: Mitigating Vulnerabilities for Government – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
LoanDepot Hit by Ransomware Attack; Multiple Systems Offline – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations Large Mortgage Lender’s Customers Say the Online Payment Portable Is Inaccessible Mathew J. Schwartz...
BreachForums Boss Jailed for Violating Release Requirements – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Conor Fitzgerald Allegedly Violated Computer Monitoring Requirement, VPN Ban Mathew J. Schwartz (euroinfosec) • January...
QNAP Patches High-Severity Flaws in QTS, Video Station, QuMagie, Netatalk Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire QNAP has released patches for a dozen vulnerabilities in its products, including several high-severity flaws. The post QNAP Patches High-Severity...
Turkish Cyberspies Targeting Netherlands – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Turkish state-sponsored group Sea Turtle has been targeting multiple organizations in the Netherlands for espionage. The post Turkish Cyberspies Targeting...
Major IT, Crypto Firms Exposed to Supply Chain Compromise via New Class of CI/CD Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Self-hosted GitHub Actions runners could allow attackers to inject malicious code into repositories, leading to supply chain attacks. The post...
NIST: No Silver Bullet Against Adversarial Machine Learning Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs NIST has published guidance on adversarial machine learning (AML) attacks and mitigations, warning that there is no silver bullet. The...
How to Get Started With Security Automation: Consider the Top Use Cases Within Your Industry – Source: www.securityweek.com
Source: www.securityweek.com – Author: Marc Solomon Organizations in different industries may approach security automation from a different entry point, but the requirements for an automation platform...
CISO Conversations: Jason Rebholz and Jason Ozin From the Insurance Sector – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek interviews two CISOs from the insurance sector: Jason Rebholz at Corvus Insurance and Jason Ozin at UK-based PIB Group....