The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2024
A Detailed Guide on AMSI Bypass
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 Türkiye Email Security Landscape Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 Authentication Report Enzoic final
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
200 IT Security Job Interview QuestionsThe Questions IT Leaders Ask
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Great Cybersecurity Frameworks
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How the definition of digital transformation continues to evolve… – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau From 2003-2004, Aman served as the Chief Technology Officer for AGF Technologies, during which time he also co-founded a company called...
OpenAI: Gen AI ‘Impossible’ Without Copyrighted Material – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Copyright Probes Continue to Trouble AI Developers Akshaya Asokan (asokan_akshaya)...
Live Webinar | Evolution of Legacy Shadow IT: How Does AI Change the Landscape in 2024? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Nate Smolenski Head of Cyber Intelligence Strategy, Netskope Nate Smolenski is an experienced CISO, Advisor, and technology leader with over two...
Live Webinar | Cybersecurity Compliance Essentials for Resource-Constrained State and Local Governments – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Jamie Tomasello Managing Director, Superbloom Jamie Tomasello (she/her and he/him) is a technology and policy leader with a strategic focus on...
Kyocera Printers Open to Path Traversal Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security Path Traversal Flaw Allows Malicious Actors to Exploit Kyocera’s Device Manager Prajeet Nair (@prajeetspeaks) • January 9, 2024 ...
Fallout Mounting From Recent Major Health Data Hacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Post-Breach List of Affected Individuals Growing; More Lawsuits Filed Marianne...
Microsoft Ships Urgent Fixes for Critical Flaws in Windows Kerberos, Hyper-V – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Patch Tuesday: Redmond patches critical, remote code execution vulnerabilities haunting Windows Kerberos and Windows Hyper-V. The post Microsoft Ships Urgent...
Delinea Acquires Authomize to Tackle Identity-Based Threats – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Delinea acquires Israeli startup Authomize to add identity threat detection and response (IDTR) technologies to its product portfolio. The post...
CISA Warns of Apache Superset Vulnerability Exploitation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire CISA has added a critical-severity Apache Superset flaw (CVE-2023-27524) to its Known Exploited Vulnerabilities catalog. The post CISA Warns of...
Adobe Patches Code Execution Flaws in Substance 3D Stager – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Patch Tuesday: Adobe patches six security flaws in the Substance 3D Stager product and warned of code execution risks on...
Siemens, Schneider Electric Release First ICS Patch Tuesday Advisories of 2024 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Industrial giants Siemens and Schneider Electric publish a total of 7 new security advisories addressing 22 vulnerabilities. The post Siemens,...
Turkish Hackers Target Microsoft SQL Servers in Americas, Europe – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Researchers at Securonix warn that Turkish threat actors are targeting organizations in the Americas and Europe with ransomware campaigns. The...
Continuity in Chaos: Applying Time-Tested Incident Response to Modern Cybersecurity – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matt Honea Despite the drastically newer and more complex technology, many of the core incident response principles remain the exact same and...
Bosch Nutrunner Vulnerabilities Could Aid Hacker Attacks Against Automotive Production Lines – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Hackers can take complete control of Bosch Rexroth nutrunners, installing ransomware or altering settings to cause financial impact and brand...
LoanDepot Takes Systems Offline Following Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Mortgage lending firm LoanDepot has disclosed a cyberattack resulting in data encryption and system disruptions. The post LoanDepot Takes Systems...
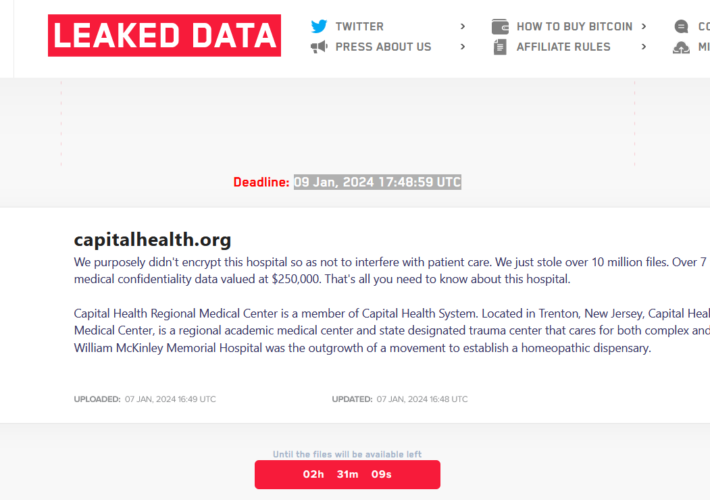
Ransomware Gang Claims Attack on Capital Health – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The LockBit ransomware gang claims to have stolen over 7 terabytes of data from hospital system Capital Health. The post...
Microsoft Patch Tuesday for January 2024 fixed 2 critical flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft Patch Tuesday for January 2024 fixed 2 critical flaws Microsoft Patch Tuesday security updates for January 2024 addressed a...
CISA adds Apache Superset bug to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Apache Superset bug to its Known Exploited Vulnerabilities catalog U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Apache...
LockBit ransomware gang claims the attack on Capital Health – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini LockBit ransomware gang claims the attack on Capital Health The LockBit ransomware gang claimed responsibility for the cyber attack on...
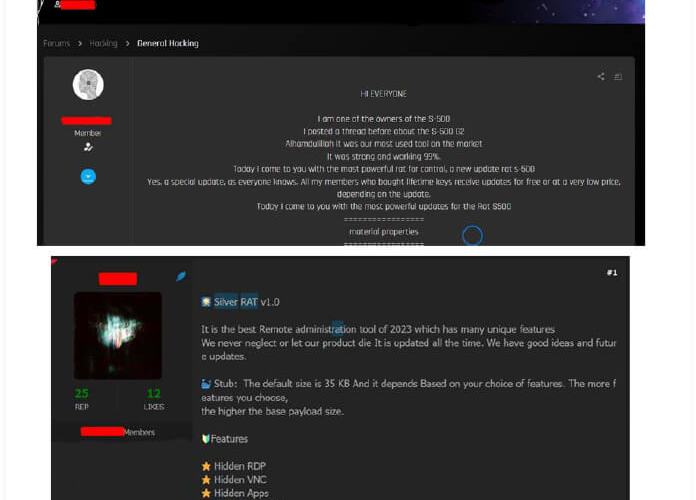
Syrian group Anonymous Arabic distributes stealthy malware Silver RAT – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Syrian group Anonymous Arabic distributes stealthy malware Silver RAT A hacker group that calls itself Anonymous Arabic is distributing a...
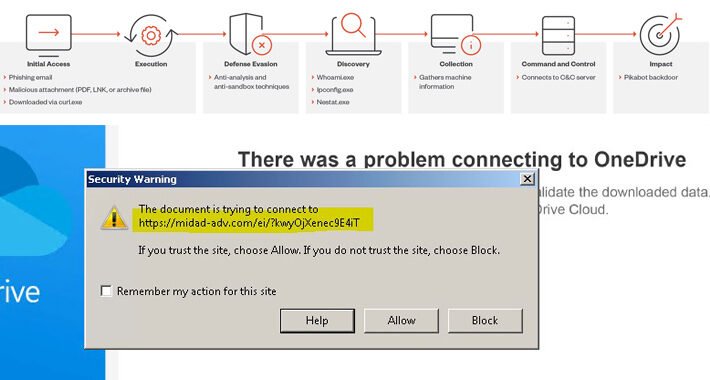
Alert: Water Curupira Hackers Actively Distributing PikaBot Loader Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024NewsroomMalware / Cyber Threat A threat actor called Water Curupira has been observed actively distributing the PikaBot loader malware...
Turkish Hackers Exploiting Poorly Secured MS SQL Servers Across the Globe – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024NewsroomData Security / Cyber Attack Poorly secured Microsoft SQL (MS SQL) servers are being targeted in the U.S., European...
Why Public Links Expose Your SaaS Attack Surface – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 09, 2024The Hacker NewsSaaS Security / Data Security Collaboration is a powerful selling point for SaaS applications. Microsoft, Github, Miro,...
ONLINE FRAUD SCHEMES: A WEB OF DECEIT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...