Source: securityboulevard.com – Author: Avoid The Hack! Welcome to the world of online/digital privacy! Like its sister guide for cybersecurity, this privacy guide was written for...
Year: 2024
USENIX Security ’23 – Fieke Miedema, Kelvin Lubbertsen, Verena Schrama, Rolf van Wegberg – Mixed Signals: Analyzing Ground-Truth Data on the Users and Economics of a Bitcoin Mixing Service – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Netcraft Report Surfaces Spike in Online Healthcare Product Scams Why the US Needs Comprehensive Cybersecurity Legislation A New...
The State of Software Supply Chain Security 2024: Key takeaways – Source: securityboulevard.com
Source: securityboulevard.com – Author: Carolynn van Arsdale Software supply chain attacks are now mainstream events — a change in tactics by cyber-attackers that you can measure...
UK Privacy Watchdog Probes GenAI Privacy Concerns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Geo Focus: The United Kingdom , Geo-Specific ICO Call for Evidence to Focus on Legal...
Datto Presents: The State of MSP – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Mimecast Appoints Marc van Zadelhoff as New CEO – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Leadership & Executive Communication , Training & Security Leadership Leadership Transition Comes After 21 Years Under Peter Bauer as CEO Chris...
Webinar | Empower Agile Government Transformation with Cloud-Native Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Christina Hausman Product Marketing Manager Security Christina Hausman has over 20 years of expertise in product management, marketing, sales & partner...
Webinar | Reactive to Proactive: Elevating OT Cybersecurity with Threat Intelligence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Josh Hanrahan Principal Adversary Hunter, Dragos Josh Hanrahan is a Principal Adversary Hunter at Dragos. As part of the Threat Discovery...
Money Launderers, Fraudsters Flocking to Tether: UN Report – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Cryptocurrency Has ‘Supercharged’ Organized Crime in Southeast Asia Rashmi Ramesh...
NC Health System Agrees to Pay $6.6M in Web Tracking Case – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific Novant Health Is Among Latest Organizations Opting to Settle Patient Privacy Claims...
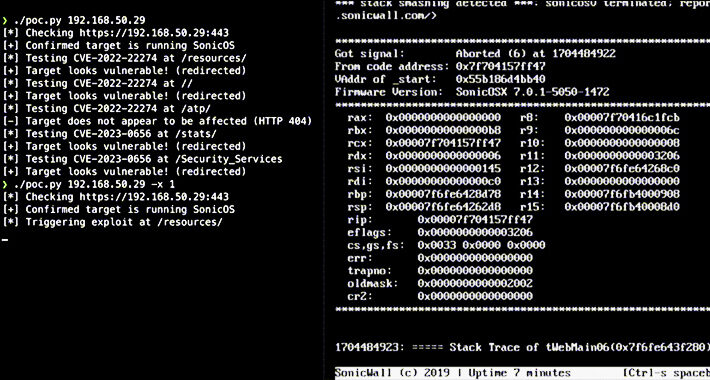
Alert: Over 178,000 SonicWall Firewalls Potentially Vulnerable to Exploits – Act Now – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 16, 2024NewsroomVulnerability / Network Security Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at least one of...
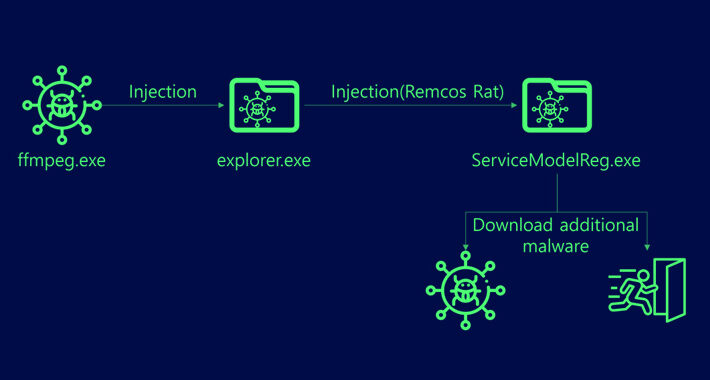
Remcos RAT Spreading Through Adult Games in New Attack Wave – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 16, 2024NewsroomBotnet / Malware The remote access trojan (RAT) known as Remcos RAT has been found being propagated via webhards...
A lightweight method to detect potential iOS malware – Source: securelist.com
Source: securelist.com – Author: Maher Yamout Introduction In the ever-evolving landscape of mobile security, hunting for malware in the iOS ecosystem is akin to navigating a...
Ho, Ho, Hoooold on a Minute: A New Year Resolution That IoT Isn’t a Gift That Keeps on Taking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Tom Eston Some IoT products may make your life easier, but they also may be somewhat of a Trojan Horse. The post...
Vulnerabilities Expose PAX Payment Terminals to Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Vulnerabilities in Android-based PoS terminals from PAX can be exploited to downgrade bootloaders, execute arbitrary code. The post Vulnerabilities Expose...
Remotely Exploitable ‘PixieFail’ Flaws Found in Tianocore EDK II PXE Implementation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Quarkslab finds serious, remotely exploitable vulnerabilities in EDK II, the de-facto open source reference implementation of the UEFI spec. The...
Remote Code Execution Vulnerability Found in Opera File Sharing Feature – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in Opera browser’s file sharing feature My Flow could be exploited for remote code execution. The post Remote...
180k Internet-Exposed SonicWall Firewalls Vulnerable to DoS Attacks, Possibly RCE – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Two DoS vulnerabilities patched in 2022 and 2023 haunt nearly 180,000 internet-exposed SonicWall firewalls. The post 180k Internet-Exposed SonicWall Firewalls...
VMware Urges Customers to Patch Critical Aria Automation Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Aria Automation is affected by a critical vulnerability that could be exploited to gain access to remote organizations and workflows....
Hacker Conversations: HD Moore and the Line Between Black and White – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek talked to HD Moore, best known as the founder and original developer of Metasploit. The post Hacker Conversations: HD...
Government, Military Targeted as Widespread Exploitation of Ivanti Zero-Days Begins – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The recently disclosed Ivanti VPN zero-days have been exploited to hack at least 1,700 devices, including government, telecoms, defense, and...
Atlassian warns of critical RCE flaw in older Confluence versions – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Atlassian Confluence Data Center and Confluence Server are vulnerable to a critical remote code execution (RCE) vulnerability that impacts versions...
Ivanti Connect Secure zero-days now under mass exploitation – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Two zero-day vulnerabilities affecting Ivanti’s Connect Secure VPN and Policy Secure network access control (NAC) appliances are now under mass...
Comprehensive Guide to Patch Management Templates – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal We all know that maintaining up-to-date systems is crucial. Patch management plays a vital role in this process. This article...
How to Create an End-to-End Privileged Access Management Lifecycle – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Key takeaways: Why privileged access management requires a continuous approach; The common pitfalls of poor privileged access management; How to...
Framework Discloses Data Breach After Third-Party Got Phished – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Framework Computer announced the discovery of a data breach that exposed the private data of an unspecified number of its...
Google Workspace: Cybersecurity Friend or Foe? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Vladimir Unterfingher Kevin Mitnick, once dubbed the World’s Most Famous Hacker said that “hackers are breaking the systems for profit. Before, it...
Sea Turtle Hackers Spy on Dutch ISPs and Telecommunication Companies – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Sea Turtle Turkish state-backed group changed to focus on internet service providers (ISPs), telcos, media, and Kurdish websites. Sea Turtle...
Turkish Hackers Target Microsoft SQL Servers with Mimic Ransomware – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Threat actors use AnyDesk to install Mimic ransomware and exploit poorly configured MSSQL database servers. Security researchers dubbed this ransomware campaign...
Managed Service Provider (MSP) Best Practices: A Insider’s Guide – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici MSPs have carved their way into the business environment by offering a unique value proposition: by managing a wide range...