Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers looking at more than 10,000 scripts used by the Parrot traffic direction system (TDS) noticed an evolution marked by...
Year: 2024
Apple fixes first zero-day bug exploited in attacks this year – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Apple released security updates to address this year’s first zero-day vulnerability exploited in attacks that could impact iPhones, Macs, and...
Ivanti: VPN appliances vulnerable if pushing configs after mitigation – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Ivanti warned admins to stop pushing new device configurations to appliances after applying mitigations because this will leave them vulnerable...
loanDepot cyberattack causes data breach for 16.6 million people – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Mortgage lender loanDepot says that approximately 16.6 million people had their personal information stolen in a ransomware attack disclosed earlier...
Trezor support site breach exposes personal data of 66,000 customers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Trezor issued a security alert after identifying a data breach that occurred on January 17 due to unauthorized access to their...
Hackers start exploiting critical Atlassian Confluence RCE flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers are observing exploitation attempts for the CVE-2023-22527 remote code execution flaw vulnerability that affects outdated versions of Atlassian Confluence servers....
North Korean Hackers Weaponize Fake Research to Deliver RokRAT Backdoor – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 22, 2024NewsroomCyber Attack / Hacking Media organizations and high-profile experts in North Korean affairs have been at the receiving end...
MavenGate Attack Could Let Hackers Hijack Java and Android via Abandoned Libraries – Source:thehackernews.com
Source: thehackernews.com – Author: . Several public and popular libraries abandoned but still used in Java and Android applications have been found susceptible to a new...
NS-STEALER Uses Discord Bots to Exfiltrate Your Secrets from Popular Browsers – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 22, 2024NewsroomBrowser Security / Cyber Threat Cybersecurity researchers have discovered a new Java-based “sophisticated” information stealer that uses a Discord...
52% of Serious Vulnerabilities We Find are Related to Windows 10 – Source:thehackernews.com
Source: thehackernews.com – Author: . We analyzed 2,5 million vulnerabilities we discovered in our customer’s assets. This is what we found. Digging into the data The...
With hackers poisoning water systems, US agencies issue incident response guide to boost cybersecurity – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley US federal agencies have teamed up to release a cybersecurity best practice guidance for the water and wastewater sector (WWS)....
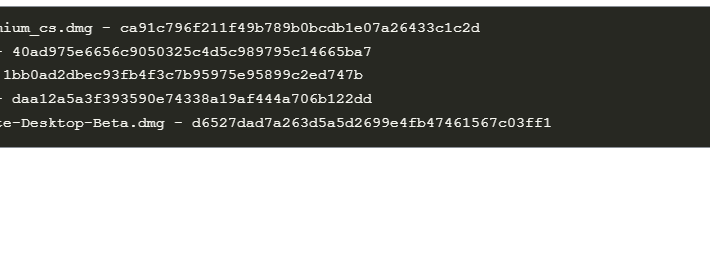
Cracked software beats gold: new macOS backdoor stealing cryptowallets – Source: securelist.com
Source: securelist.com – Author: Sergey Puzan A month ago, we discovered some cracked apps circulating on pirating websites and infected with a Trojan proxy. The malicious...
Data Privacy Week: Lack of Understanding, Underfunding Threaten Data Privacy and Compliance – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A lack of understanding combined with budgetary squeezes are significant obstacles for organization’s navigating data privacy and compliance with data protection...
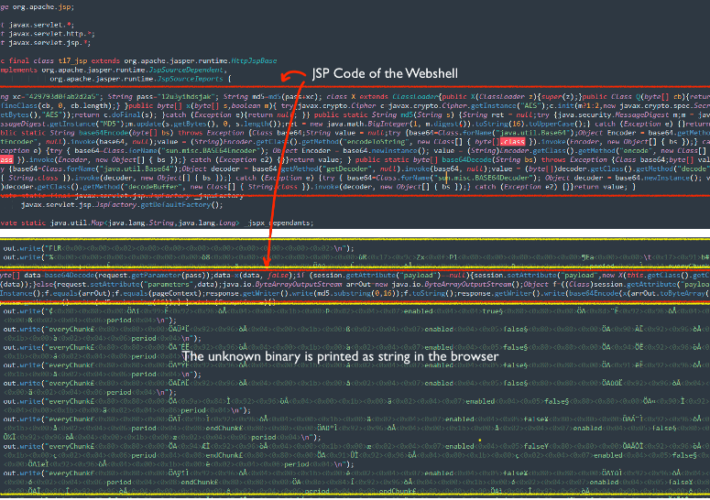
Threat actors exploit Apache ActiveMQ flaw to deliver the Godzilla Web Shell – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors exploit Apache ActiveMQ flaw to deliver the Godzilla Web Shell Researchers warn of a spike in attacks exploiting...
Cybercriminals leaked massive volumes of stolen PII data from Thailand in Dark Web – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cybercriminals leaked massive volumes of stolen PII data from Thailand in Dark Web Resecurity researchers warn of massive leak of...
Backdoored pirated applications targets Apple macOS users – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Backdoored pirated applications targets Apple macOS users Researchers warned that pirated applications have been employed to deliver a backdoor to...
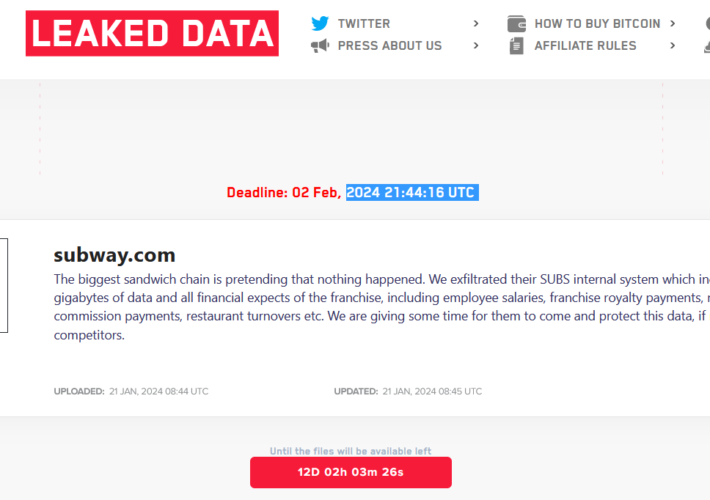
LockBit ransomware gang claims the attack on the sandwich chain Subway – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini LockBit ransomware gang claims the attack on the sandwich chain Subway The LockBit ransomware gang claimed to have hacked Subway,...
FTC Bans InMarket for Selling Precise User Location Without Consent – Source:thehackernews.com
Source: thehackernews.com – Author: . The U.S. Federal Trade Commission (FTC) is continuing to clamp down on data brokers by prohibiting InMarket Media from selling or...
Apache ActiveMQ Flaw Exploited in New Godzilla Web Shell Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 22, 2024NewsroomVulnerability / Malware Cybersecurity researchers are warning of a “notable increase” in threat actor activity actively exploiting a now-patched...
Tietoevry ransomware attack causes outages for Swedish firms, cities – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Finnish IT services and enterprise cloud hosting provider Tietoevry has suffered a ransomware attack impacting cloud hosting customers in one...
Watch out for “I can’t believe he is gone” Facebook phishing posts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A widespread Facebook phishing campaign stating, “I can’t believe he is gone. I’m gonna miss him so much,” leads unsuspecting...
Brave to end ‘Strict’ fingerprinting protection as it breaks websites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Brave Software has announced plans to deprecate the ‘Strict’ fingerprinting protection mode in its privacy-focused Brave Browser because it causes...
Court charges dev with hacking after cybersecurity issue disclosure – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A German court has charged a programmer investigating an IT problem with hacking and fined them €3,000 ($3,265) for what...
USENIX Security ’23 – Kaiming Cheng, Jeffery F. Tian, Tadayoshi Kohno, Franziska Roesner – Exploring User Reactions and Mental Models Towards Perceptual Manipulation Attacks in Mixed Reality – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
Welcome to Data Privacy Week: Empowering Your Cybersecurity with BlackCloak – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Pierson The importance of data privacy continues to grow exponentially. We recognize this critical need and are excited to kick off...
Cybersecurity Challenges at the World Economic Forum – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity The 54th Annual Meeting of The World Economic Forum took place in Davos, Switzerland, this past week, and cybersecurity...
Webinar: Join us for the latest in API Threats on January 24, 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: girishwallarm In today’s complex digital landscape, the security of APIs has become paramount. As we move into 2024, it’s essential to stay...
Security Affairs newsletter Round 455 by Pierluigi Paganini – INTERNATIONAL EDITION – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Security Affairs newsletter Round 455 by Pierluigi Paganini – INTERNATIONAL EDITION | Admin of the BreachForums hacking forum sentenced to...
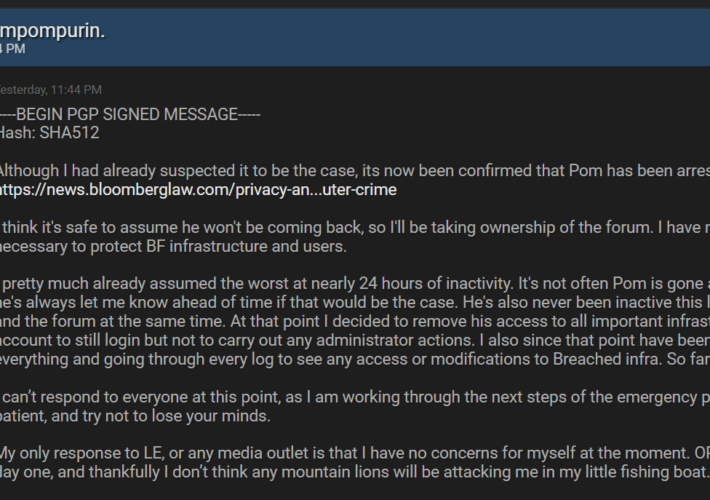
Admin of the BreachForums hacking forum sentenced to 20 years supervised release – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Admin of the BreachForums hacking forum sentenced to 20 years supervised release Conor Brian Fitzpatrick, the admin of the BreachForums...
Russia-linked Midnight Blizzard APT hacked Microsoft corporate emails – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked Midnight Blizzard APT hacked Microsoft corporate emails Microsoft revealed that the Russia-linked APT Midnight Blizzard has compromised some of...