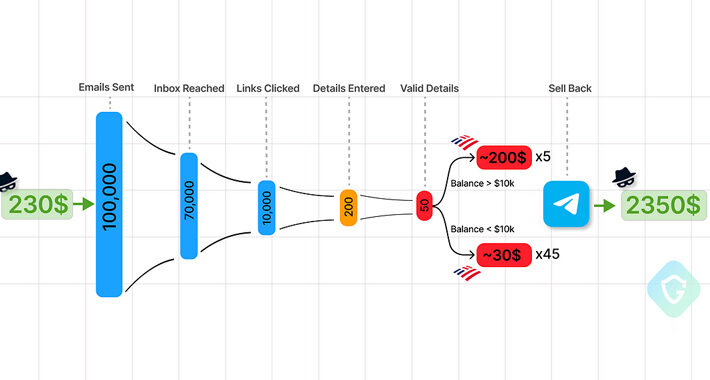
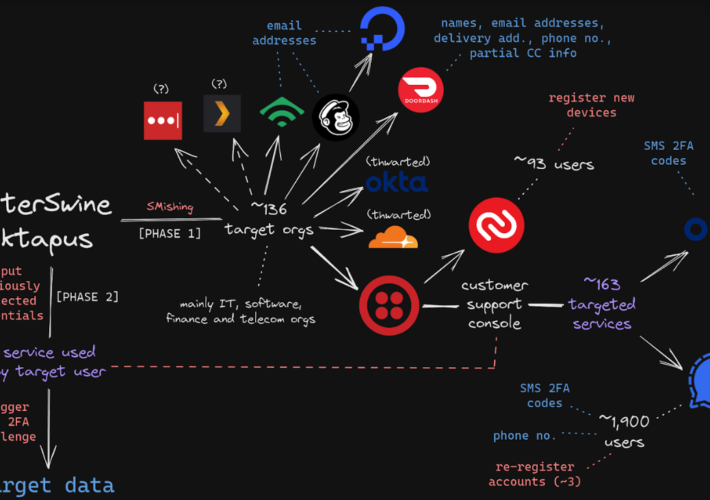
Source: thehackernews.com – Author: . Jan 31, 2024NewsroomCyber Crime / Hacking News Cybersecurity researchers are calling attention to the “democratization” of the phishing ecosystem owing to...
Year: 2024
CISA adds Apple improper authentication bug to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Apple improper authentication bug to its Known Exploited Vulnerabilities catalog U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds...
Ivanti warns of a new actively exploited zero-day – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ivanti warns of a new actively exploited zero-day Ivanti warns of two new vulnerabilities in its Connect Secure and Policy...
Threat actors exploit Ivanti VPN bugs to deploy KrustyLoader Malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors exploit Ivanti VPN bugs to deploy KrustyLoader Malware Threat actors are exploiting recently disclosed zero-day flaws in Ivanti...
Data leak at fintech giant Direct Trading Technologies – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Data leak at fintech giant Direct Trading Technologies Sensitive data and trading activity of over 300K traders leaked online by...
Root access vulnerability in GNU Library C (glibc) impacts many Linux distros – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Root access vulnerability in GNU Library C (glibc) impacts many Linux distros Qualys researchers discovered a root access flaw, tracked...
Italian data protection authority said that ChatGPT violated EU privacy laws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Italian data protection authority said that ChatGPT violated EU privacy laws Italian data protection authority regulator authority Garante said that...
FBI disrupts Chinese botnet by wiping malware from infected routers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The FBI has disrupted the KV Botnet used by Chinese Volt Typhoon state hackers to evade detection during attacks targeting...
CISA: Vendors must secure SOHO routers against Volt Typhoon attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA has urged manufacturers of small office/home office (SOHO) routers to ensure their devices’ security against ongoing attacks attempting to hijack...
Johnson Controls says ransomware attack cost $27 million, data stolen – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Johnson Controls International has confirmed that a September 2023 ransomware attack cost the company $27 million in expenses and led...
Ivanti warns of new Connect Secure zero-day exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Today, Ivanti warned of two more vulnerabilities impacting Connect Secure, Policy Secure, and ZTA gateways, one of them a zero-day...
New Linux glibc flaw lets attackers get root on major distros – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Unprivileged attackers can get root access on multiple major Linux distributions in default configurations by exploiting a newly disclosed local...
Limited Time Deal: a Lifetime of Powerful VPN Protection is Just $35 Through 2/4 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 31, 2024 Updated January 30, 2024 We may earn from vendors via affiliate links or sponsorships. This might...
Gift Yourself a Year of Online Protection for Only $50 Through 2/4 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 31, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
How to Use McAfee True Key: A Complete Beginner’s Guide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares McAfee True Key is a simple password management solution that has a free version and a single paid plan. In...
McAfee True Key Review (2024): Pricing, Features, Pros & Cons – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares McAfee True Key fast facts Our rating: 2.9 stars out of 5 Pricing: Starts at $1.67 per month Key features...
How to Use Zoho Vault Password Manager: A Beginner’s Guide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Zoho Vault is a business-focused password manager that provides convenient monitoring tools for administrators in large organizations. In this article,...
Zoho Vault Review (2024): Pricing, Features, Pros & Cons – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Zoho Vault Password Manager fast facts Our rating: 3.9 stars out of 5 Pricing: Starts at $0.90 per user Key...
Fla. Man Charged in SIM-Swapping Spree is Key Suspect in Hacker Groups Oktapus, Scattered Spider – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs On Jan. 9, 2024, U.S. authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with...
Keenan Data Breach Puts Personal Data Of 1.5 Million People at Risk – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Keenan data breach exposes sensitive data belonging to 1,509,616 individuals. The insurance broker company notified the impacted customers and employees...
Free and Downloadable Threat & Vulnerability Management Templates – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal Threat and Vulnerability Management plays a crucial role in safeguarding information systems. It involves identifying, assessing, and mitigating vulnerabilities in...
Cactus Ransomware behind Schneider Electrics Data Breach – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Cactus Ransomware claims responsibility for the January 17th Schneider Electric data breach. Schneider Electric confirms hackers got access to their...
Heimdal® Launches Partner NEXUS: A Unified and Global Partner Program for Collective Success – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici The Heimdal Partner NEXUS program is now live. NEXUS, or the ‘Network of Excellence, Unity, and Safeguarding’ is a global...
10 Best User Access Review Software (2024) – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu With data breaches on the rise, it’s important to limit access to your organization’s sensitive data. A user access review...
Canada’s ‘most prolific hacker’ jailed for two years – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A 33-year-old man has been sentenced to two years in prison after admitting his part in a series of ransomware...
Ivanti Zero-Day Patches Delayed as ‘KrustyLoader’ Attacks Mount – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading 2 Min Read Source: Peter Etchells via Alamy Stock Photo Attackers are using a pair...
‘Cactus’ Ransomware Strikes Schneider Electric – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Nate Hovee via Shutterstock Schneider Electric has fallen victim to a cyberattack affecting its Sustainability Business division,...
Apple Warns iPhone Sideloading Changes Will Increase Cyber Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: GK Images via Alamy Stock Photo In an effort to comply with the European Union’s Digital Markets Act...
Forcepoint Federal Rebrands As Everfox to Reflect New Era of Defense-Grade Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE HERNDON, Va.–(BUSINESS WIRE)– Forcepoint Federal announced today that it has rebranded as Everfox to reflect its next chapter as a...
Cohesity Research Reveals Most Companies Pay Millions in Ransoms – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN JOSE, Calif. – January 30, 2024 – Research commissioned by Cohesity, a leader in AI-powered data security and management, reveals today’s...