Source: www.bitdefender.com – Author: Graham Cluley The UK’s Sellafield nuclear waste processing and storage site has been fined £332,500 by regulators after its IT systems were...
Day: October 13, 2024
SOC Prime Successfully Completes SOC 2 Type II Compliance – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Reaching Security Compliance Milestone for the Fourth Year in a Row We are excited to share that SOC Prime has...
Shrouded#Sleep Campaign Detection: North Korean Hackers Linked to the APT37 Group Use New VeilShell Malware Targeting Southeast Asia – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko North Korea-affiliated APT groups have consistently ranked among the most active adversaries over the past decade. This year, security experts...
Cybersecurity and compliance: The dynamic duo of 2024 – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Graham Cluley Security News is sponsored this week by the folks at ManageEngine. Thanks to the great team there for...
SOC Prime Threat Bounty Digest — September 2024 Results – Source: socprime.com
Source: socprime.com – Author: Alla Yurchenko Detection Content Creation, Submission & Release In September, the Threat Bounty Program experienced significant growth, with more submissions of detection...
Tick tock.. Operation Cronos arrests more LockBit ransomware gang suspects – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley International law enforcement agencies have scored another victory against the LockBit gang, with a series of arrests and the seizure...
Uncoder AI: A Guide on Contributing Detection Rules to SOC Prime Platform via Threat Bounty Program – Source: socprime.com
Source: socprime.com – Author: Hanna Korostelova Efficiency and collaboration are essential in cybersecurity. As part of the SOC Prime Platform, Uncoder AI is a a professional...
Smashing Security podcast #387: Breaches in your genes, and Kaspersky switcheroo raises a red flag – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley From family tree to jail cell? A hacker is alleged to have exploited information on genealogy websites to steal millions...
Detecting CUPS Exploits: Critical Security Vulnerabilities in Linux and Unix Systems Allow Remote Code Execution – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk Another day, another challenge for cyber defenders. Recently, researchers revealed a series of critical security gaps in the OpenPrinting Common...
The AI Fix #18: ChatGPT’s false memories, and would an inner critic stop AI hallucinations? – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content News and views from the world of artificial intelligence. In episode 18 of “The AI Fix” our...
British man used genealogy websites to fuel alleged hacking and insider trading scheme – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A London-based man is facing extradition to the United States after allegedly masterminding a scheme to hack public companies prior...
Gamaredon Attack Detection: Cyber-Espionage Operations Against Ukraine by the russia-linked APT – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The nefarious state-sponsored russia-aligned Gamaredon (aka Hive0051, UAC-0010, or Armageddon APT) has been launching a series of cyber-espionage campaigns against...
SnipBot Detection: A New RomCom Malware Variant Leverages a Custom Code Obfuscation Method and Sophisticated Evasion Techniques – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk A novel iteration of the RomCom malware family emerges in the cyber threat arena. The new malware, dubbed SnipBot, uses...
Vendor-Agnostic Cybersecurity: Adapting to the Future of Threat Detection – Source: socprime.com
Source: socprime.com – Author: Eugene Tkachenko In today’s fast-moving technological landscape, organizations face unprecedented challenges in managing their security operations. When both threats and technologies change...
NextGen Identity Management – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Federal agencies face a pivotal cybersecurity challenge: prevent unauthorized entities from accessing systems and facilities, while granting authorized federal employees...
Strengthening Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin Integrated Governance, Risk, and Compliance Is Critical Business executives in all sectors place a high premium on security in the quickly...
How AI-Driven Cybersecurity Offers Both Promise and Peril for Enterprises – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Artificial Intelligence (AI) is transforming multiple sectors, driving innovation and enhancing productivity and cybersecurity. The AI market is projected to...
Innovator Spotlight: Zendata – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin In today’s digital landscape, data security and privacy have become top priorities for organizations of all sizes. According to a 2023...
Worried about Insider Risk? Pay More Attention to Offboarding – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Discussions of insider risk inevitably conjure images of disgruntled IT employees stealing sensitive data from the comfort of an air-conditioned...
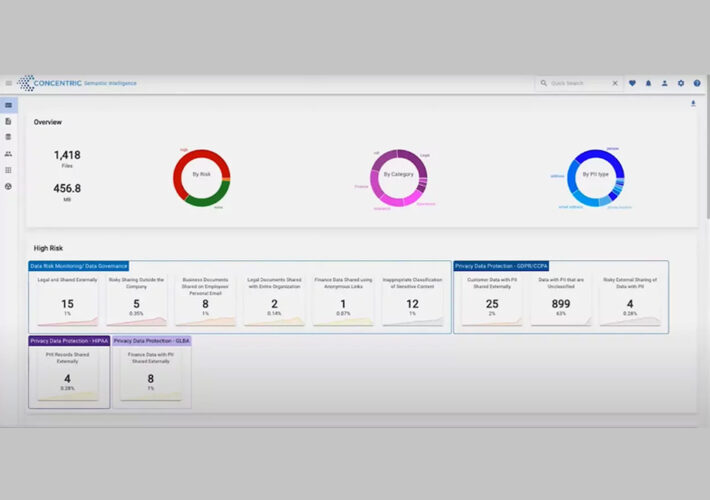
Innovator Spotlight: Concentric AI – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Nick It’s not enough for companies to just discover and monitor sensitive data. They need tools that can proactively fix any security...
Unmasking Shadow Apps to Secure Your SaaS Stack – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team It is a tale almost as old as time: users click download, install, and accept as they adopt new software...
How Automation Can Help Security Policy Optimization – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team One of the recurring questions we hear from network security leaders is “why aren’t our security policies optimized?” The answer,...
USENIX NSDI ’24 – Known Knowns and Unknowns: Near-Realtime Earth Observation Via Query Bifurcation In Serval – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Bill Tao, Om Chabra, Ishani Janveja, Indranil Gupta, Deepak Vasisht Our sincere thanks to USENIX, and the Presenters & Authors...
Transforming Cyber Risk Quantification and Vulnerability Prioritization with KnightVision – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ethan Bresnahan In today’s complex cyber landscape, managing risks effectively isn’t just about identifying threats—it’s about understanding their impact and knowing how...
Cost of Online Brand Impersonation: Customer Acquisition and Loyalty – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mitch Warren Online brand impersonation is an insidious threat compared to more straightforward attacks. Ransomware, for example, is simply extortion. A cybercriminal...
Generational security: The meaning behind this year’s Cyber Security Awareness Month theme – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden This year’s Cyber Security Awareness Month theme is “Generation Cyber Safe: Because online security knows no age”, but what does...
InCyber Forum Canada 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist The InCyber Forum Canada 2024 conference is an outstanding event, packed with multiple stages, many thought-leadership panels, and an expansive...
More on My AI and Democracy Book – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier In July, I wrote about my new book project on AI and democracy, to be published by MIT Press in...
USENIX NSDI ’24 – Democratizing Direct-to-Cell Low Earth Orbit Satellite Networks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Lixin Liu, Yuanjie Li, Hewu Li, Jiabo Yang, Wei Liu, Jingyi Lan, Yufeng Wang, Jiarui Li, Jianping Wu, Qian Wu,...
Identity Under Siege: Responding to the National Public Data Breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: hmeyers Gary Perkins, Chief Information Security Officer, CISO Global October 11, 2024 While the scale of this data breach is alarming –...