Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, Jan. 30, 2024 /PRNewswire/ — Delinea, a leading provider of solutions that seamlessly extend Privileged Access Management (PAM), today published its...
Month: February 2024
Feds Confirm Remote Killing of Volt Typhoon’s SOHO Botnet – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Jeremy Walter via Alamy Stock Photo US law enforcement has disrupted the infrastructure of...
CISA Orders Ivanti VPN Appliances Disconnected: What to Do – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading Source: EyeEm via Alamy Stock Photo The United States Cybersecurity and Infrastructure Security Agency...
Ukraine Military Targeted With Russian APT PowerShell Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: Design Pics Inc via Alamy Stock Photo A sophisticated Russian advanced persistent threat (APT) has launched a...
China Infiltrates US Critical Infrastructure in Ramp-up to Conflict – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: BeeBright via Shutterstock The People’s Republic of China is accelerating the development of its military capabilities —...
FritzFrog Botnet Exploits Log4Shell on Overlooked Internal Hosts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Picture Partners via Alamy Stock Photo A new variant of an advanced botnet called “FritzFrog” has been...
The Imperative for Robust Security Design in the Health Industry – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nielet D’mello Source: Olekcii Mach via Alamy Stock Photo COMMENTARY In an era dominated by digital innovation and technological advancements, healthcare companies...
FritzFrog Returns with Log4Shell and PwnKit, Spreading Malware Inside Your Network – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 01, 2024NewsroomCyber Attack / Botnet The threat actor behind a peer-to-peer (P2P) botnet known as FritzFrog has made a return...
Exposed Docker APIs Under Attack in ‘Commando Cat’ Cryptojacking Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 01, 2024NewsroomCryptojacking / Linux Security Exposed Docker API endpoints over the internet are under assault from a sophisticated cryptojacking campaign...
U.S. Feds Shut Down China-Linked “KV-Botnet” Targeting SOHO Routers – Source:thehackernews.com
Source: thehackernews.com – Author: . The U.S. government on Wednesday said it took steps to neutralize a botnet comprising hundreds of U.S.-based small office and home...
CISA orders federal agencies to disconnect Ivanti VPN instances by February 2 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA orders federal agencies to disconnect Ivanti VPN instances by February 2 Pierluigi Paganini February 01, 2024 CISA is ordering...
Multiple malware used in attacks exploiting Ivanti VPN flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple malware used in attacks exploiting Ivanti VPN flaws Pierluigi Paganini February 01, 2024 Mandiant spotted new malware used by...
Police seized 50,000 Bitcoin from operator of the now-defunct piracy site movie2k – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Police seized 50,000 Bitcoin from operator of the now-defunct piracy site movie2k Pierluigi Paganini February 01, 2024 German police seized...
Crooks stole around $112 million worth of XRP from Ripple’s co-founder – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Crooks stole around $112 million worth of XRP from Ripple’s co-founder Crooks stole around $112 million worth of Ripple XRP...
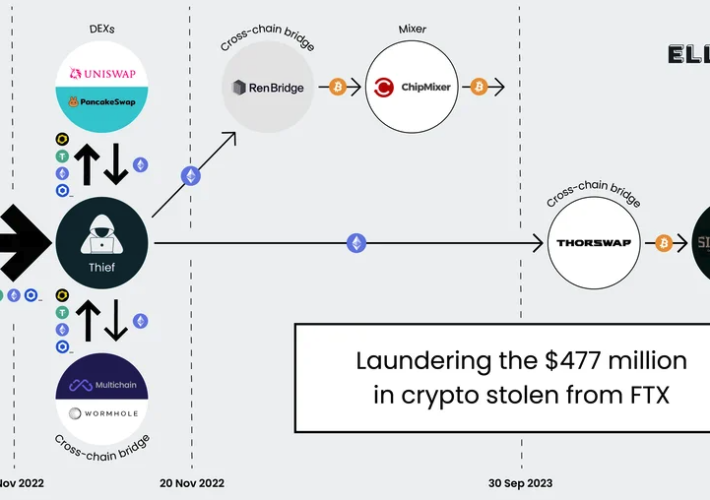
Arrests in $400M SIM-Swap Tied to Heist at FTX? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Three Americans were charged this week with stealing more than $400 million in a November 2022 SIM-swapping attack. The U.S. government...
What Is Cyber Threat Hunting? (Definition & How it Works) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Nicole Rennolds Cyber threat hunting involves proactively searching for threats on an organization’s network that are unknown to (or missed by) traditional...
Hiring Kit: Cyber Threat Hunter – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Professional cyber threat hunters complement cybersecurity programs focusing on potential threats and vulnerabilities that may breach automated cybersecurity tools and traditional systems....
Mobile Device Security Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Mobile devices are commonly used to conduct company business, which can render them more susceptible to risk than desktop or even laptop...
Smashing Security podcast #357: Interview with an iPhone thief, anti-AI, and have we gone too far? – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The iPhone security setting that you should enable right now, the worrying way that AI is predicting what criminals look...
Hackers push USB malware payloads via news, media hosting sites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A financially motivated threat actor using USB devices for initial infection has been found abusing legitimate online platforms, including GitHub,...
Police seize record 50,000 Bitcoin from now-defunct piracy site – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The police in Saxony, eastern Germany, have seized 50,000 Bitcoin from the former operator of the pirate site movie2k.to through...
Europcar denies data breach of 50 million users, says data is fake – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Car rental company Europcar says it has not suffered a data breach and that shared customer data is fake after...
Exploit released for Android local elevation flaw impacting 7 OEMs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A proof-of-concept (PoC) exploit for a local privilege elevation flaw impacting at least seven Android original equipment manufacturers (OEMs) is...
CISA warns of patched iPhone kernel bug now exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA warned today that a patched kernel security flaw affecting Apple iPhones, Macs, TVs, and watches is now being actively...
10 Best Privileged Identity Management Tools (2024) – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu The Importance of Choosing the Right Privilege Identity Management Solution The essence of effective Privileged Identity Management (PIM) lies not...
Cactus Ransomware behind Schneider Electric Data Breach – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Cactus Ransomware claims responsibility for the January 17th Schneider Electric data breach. Schneider Electric confirms hackers got access to their...
HeadCrab 2.0 Goes Fileless, Targeting Redis Servers for Crypto Mining – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 01, 2024NewsroomCryptocurrency / Botnet Cybersecurity researchers have detailed an updated version of the malware HeadCrab that’s known to target Redis...
Why the Right Metrics Matter When it Comes to Vulnerability Management – Source:thehackernews.com
Source: thehackernews.com – Author: . How’s your vulnerability management program doing? Is it effective? A success? Let’s be honest, without the right metrics or analytics, how...
Warning: New Malware Emerges in Attacks Exploiting Ivanti VPN Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 01, 2024NewsroomNetwork Security / Malware Google-owned Mandiant said it identified new malware employed by a China-nexus espionage threat actor known...
CISA Warns of Active Exploitation of Critical Flaws in Apple iOS and macOS – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 01, 2024NewsroomVulnerability / Software Update The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a high-severity flaw impacting...