The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: February 22, 2024
Cyber Secutiry Incident Management Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft has started testing Wi-Fi 7 support in Windows 11 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has started testing support for Wi-Fi 7 in Windows 11, which offers multi-gigabit speeds and improved throughput, latency, and...
Microsoft now force installing Windows 11 23H2 on eligible PCs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has started force installing Windows 11 23H2 on eligible devices that have reached or are close to their end-of-servicing...
Bitwarden’s new auto-fill option adds phishing resistance – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Bitwarden open-source password management service has introduced a new inline auto-fill menu that addresses the risk of user credentials being...
ScreenConnect servers hacked in LockBit ransomware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Attackers are exploiting a maximum severity authentication bypass vulnerability to breach unpatched ScreenConnect servers and deploy LockBit ransomware payloads on...
FTC to ban Avast from selling browsing data for advertising purposes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Federal Trade Commission (FTC) will order Avast to pay $16.5 million and ban the company from selling the...
Massive AT&T outage impacts US mobile subscribers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Update: AT&T has restored wireless service to all affected customers but the cause has not been disclosed Tens of thousands of...
LockBit ransomware secretly building next-gen encryptor before takedown – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas LockBit ransomware developers were secretly building a new version of their file encrypting malware, dubbed LockBit-NG-Dev – likely to become...
IACS Cyber Security Incident Response Playbook
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
HR Top Priorities for 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Guide to Technical and Organisational Data Protection
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Global Internal Audit Standards 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Global Cyber Security Trends
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Generative AI The Data Protection Implications
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybervergent Cybersecurity Annual Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Career Roadmap
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security in Supplier Relationships Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
TRAINING PROGRAM {CAPTURE THE FLAG}
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Code of Best Practices of Corporate Governance
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cloud & Compromise Gamifying of Cloud Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
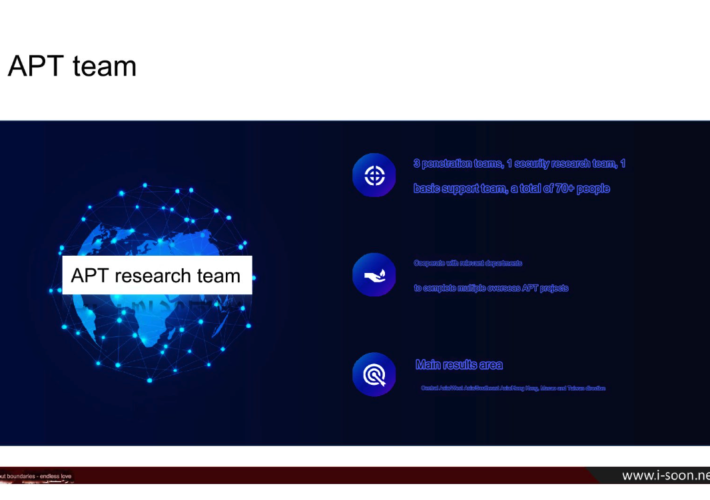
New Leak Shows Business Side of China’s APT Menace – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A new data leak that appears to have come from one of China’s top private cybersecurity firms provides a rare glimpse...
SMBs at Risk From SendGrid-Focused Phishing Tactics – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at Kaspersky have uncovered a new phishing campaign that specifically targets small and medium-sized businesses (SMBs). The attack method...
Change Healthcare Cyber-Attack Leads to Prescription Delays – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Health tech firm Change Healthcare, part of Optum, has been hit by a cyber-attack, leading to delays in prescriptions being issued...
Russian-Aligned Network Doppelgänger Targets German Elections – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A joint effort by SentinelLabs and ClearSky Cyber Security has uncovered a significant propaganda and disinformation campaign, possibly orchestrated by the...
OWASP Releases Security Checklist for Generative AI Deployment – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by Chief information security officers now have a new tool at their disposal to get started with AI securely. The...
Cyber Pros Embrace AI, Over 80% Believe It Will Enhance Jobs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Most cybersecurity professionals believe that AI will have a positive impact on their jobs, helping alleviate pressures caused by the cyber...
Chinese Duo Found Guilty of $3m Apple Fraud Plot – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two Chinese nationals have been found guilty of running a sophisticated fraud scheme in which they attempted to con Apple out...
Ransomware Warning as CVSS 10.0 ScreenConnect Bug is Exploited – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 IT admins have been urged to patch any on-premises ScreenConnect servers immediately, after reports that a recently published maximum severity vulnerability...
Businesses Increase Cybersecurity as Budgets Surge in 2024 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity is a top concern for businesses in 2024, with over two-thirds of IT decision-makers reporting increased budgets. This positive trend...