Source: thehackernews.com – Author: . Jan 29, 2024NewsroomVulnerability / NTML Security A now-patched security flaw in Microsoft Outlook could be exploited by threat actors to access...
Day: January 29, 2024
493 Companies Share Their SaaS Security Battles – Get Insights in this Webinar – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 29, 2024The Hacker NewsSaaS Security / Webinar In today’s digital world, security risks are more prevalent than ever, especially when...
Albabat, Kasseika, Kuiper: New Ransomware Gangs Rise with Rust and Golang – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 29, 2024NewsroomRansomware / Malware Cybersecurity researchers have detected in the wild yet another variant of the Phobos ransomware family known...
Ransomware’s Impact Could Include Heart Attacks, Strokes & PTSD – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Ransomware incidents cause significant harm at many levels, including to physical and mental health; new research from U.K. security think...
Phobos Ransomware Family Expands With New FAUST Variant – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have recently uncovered a new variant of the notorious Phobos ransomware family named FAUST. Phobos, which first emerged in...
US Senator Exposes NSA Purchase of Americans’ Internet Records – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 US Senator Ron Wyden of Oregon has unveiled documents last week substantiating claims that the National Security Agency (NSA) is actively...
Nigerian ‘Yahoo Boys’ Behind Social Media Sextortion Surge in the US – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Teenagers from Western English-speaking countries are increasingly targeted by financial sextortion attacks conducted by Nigeria-based cybercriminals, the Network Contagion Research Institute...
Microsoft Provides Defense Guidance After Nation-State Compromise – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft has provided new details for responders to the Russian nation-state attack that compromised its systems earlier in January, and issued...
Dark Web Drugs Vendor Forfeits $150m After Guilty Plea – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A prolific dark web drugs vendor has pleaded guilty and agreed to forfeit $150m, the largest single seizure ever taken by...
CI/CD at Risk as Exploits Released For Critical Jenkins Bug – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Software developers have been told to urgently patch their Jenkins servers after exploits were published for a new critical vulnerability in...
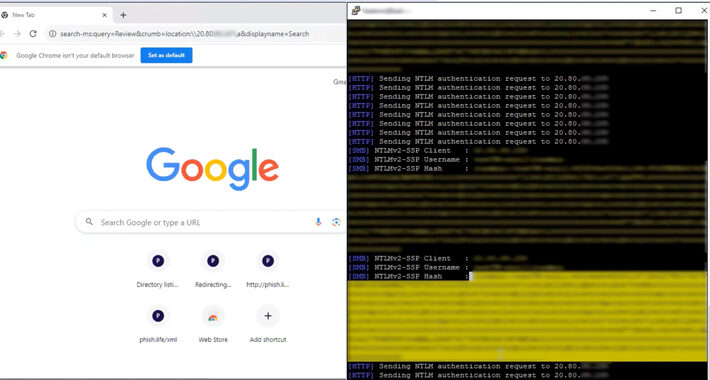
Experts detailed Microsoft Outlook flaw that can leak NTLM v2 hashed passwords – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts detailed Microsoft Outlook flaw that can leak NTLM v2 hashed passwords A flaw in Microsoft Outlook can be exploited...
NSA buys internet browsing records from data brokers without a warrant – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini NSA buys internet browsing records from data brokers without a warrant The U.S. National Security Agency (NSA) admitted to buying...
Ukraine’s SBU arrested a member of Pro-Russia hackers group ‘Cyber Army of Russia’ – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ukraine’s SBU arrested a member of Pro-Russia hackers group ‘Cyber Army of Russia’ Ukraine’s security service, the SBU, announced that it...
Multiple PoC exploits released for Jenkins flaw CVE-2024-23897 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple PoC exploits released for Jenkins flaw CVE-2024-23897 Multiple proof-of-concept (PoC) exploits for recently disclosed critical Jenkins vulnerability CVE-2024-23897 have...
NSA Admits Secretly Buying Your Internet Browsing Data without Warrants – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 29, 2024NewsroomSurveillance / Data Privacy The U.S. National Security Agency (NSA) has admitted to buying internet browsing records from data...
Malicious PyPI Packages Slip WhiteSnake InfoStealer Malware onto Windows Machines – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 29, 2024NewsroomPyPI Repository / Malware Cybersecurity researchers have identified malicious packages on the open-source Python Package Index (PyPI) repository that...
Exploits released for critical Jenkins RCE flaw, patch now – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Multiple proof-of-concept (PoC) exploits for a critical Jenkins vulnerability allowing unauthenticated attackers to read arbitrary files have been made publicly...
Kansas City public transportation authority hit by ransomware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Kansas City Area Transportation Authority (KCATA) announced it was targeted by a ransomware attack on Tuesday, January 23. KCATA...
NASCIO, PTI on What’s Coming in 2024 for State and Local IT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Every January, NASCIO and PTI release their forecasts for the coming year based on what government leaders are saying....
Navigating the Future: DevOps Predictions for 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Esther Han As technology continues to evolve at an unprecedented pace, the field of DevOps is no exception. DevOps, the cultural and...
Doubling Down on Security: The Critical Role of Two-Factor Authentication – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leigh Dow Safeguarding our online accounts has never been more crucial. One of the most effective tools at our disposal is Two-Factor...
Zero-day Confluence RCE Vulnerability Blocked by Contrast Runtime Security | CVE-2023-22527 | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joseph Beeton, Senior Application Security Researcher, Contrast Security Security Bloggers Network Home » Security Bloggers Network » Zero-day Confluence RCE Vulnerability Blocked...