Source: securityaffairs.com – Author: Pierluigi Paganini The Quantum Computing Cryptopocalypse – I’ll Know It When I See It Can quantum computing break cryptography? Can it do...
Day: January 19, 2024
Kansas State University suffered a serious cybersecurity incident – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Kansas State University suffered a serious cybersecurity incident Kansas State University (K-State) suffered a cybersecurity incident that has disrupted part...
CISA adds Chrome and Citrix NetScaler to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Chrome and Citrix NetScaler to its Known Exploited Vulnerabilities catalog U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds...
Google TAG warns that Russian COLDRIVER APT is using a custom backdoor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google TAG warns that Russian COLDRIVER APT is using a custom backdoor Google warns that the Russia-linked threat actor COLDRIVER...
PixieFail: Nine flaws in UEFI open-source reference implementation could have severe impacts – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini PixieFail: Nine flaws in UEFI open-source reference implementation could have severe impacts Experts found multiple flaws, collectively named PixieFail, in...
White House Revamps Cybersecurity Hiring Strategy – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici During his initial statements since becoming the National Cyber Director in December, Harry Coker stated that the White House plans...
Akira Ransomware Attacks Surge. Finnish Companies Among Targets – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși The National Cyber Security Centre Finland announced a surge in Akira ransomware attacks. Threat actors used Akira malware in six...
CISA and FBI Reveal Known Androxgh0st Malware IoCs and TTPs – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși CISA and FBI released an advisory on Androxgh0st malware IoCs (Indicators of Compromise) and warned about hackers using this threat...
The Unseen Threats: Anticipating Cybersecurity Risks in 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist Cybersecurity risks increase every year and bludgeon victims who fail to prepare properly. It can feel like crossing a major...
The Benefits of Using DCIM Software for Data Center Cable Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi In the ever-evolving landscape of information technology, the management of data centers has become increasingly complex. The backbone of these...
What Existing Security Threats Do AI and LLMs Amplify? What Can We Do About Them? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maciej Mensfeld In my previous blog post, we saw how the growth of generative AI and Large Language Models has created a...
Defining Good: A Strategic Approach to API Risk Reduction – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nick Rago The cost of not knowing what good is. Could you imagine our interstate highway system without roadway bridges? I don’t...
USENIX Security ’23 – Xingman Chen, Yinghao Shi, Zheyu Jiang, Yuan Li, Ruoyu Wang, Haixin Duan, Haoyu Wang, Chao Zhang – MTSan: A Feasible and Practical Memory Sanitizer for Fuzzing COTS Binaries – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Network Security Security Bloggers Network Home » Cybersecurity » Network Security » USENIX Security ’23 – Xingman Chen, Yinghao Shi, Zheyu...
API security risks, testing, protection best practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Adam Cheriki, Co-founder & CTO, Entro As per the State of Developer Experience report released in 2023, 98% of developers perceive APIs...
Stopping Alert Fatigue in 3 Simple Steps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Julie Peterson We live in a world filled with constant notifications. From medical devices to severe weather warnings on your phone to...
PixieFail Bugs in UEFI Open Source Implementation Threaten Computers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A collection of security vulnerabilities found within the de facto open source implementation of the UEFI specification could expose systems...
Randall Munroe’s XKCD ‘Bug Thread’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2024/01/randall-munroes-xkcd-bug-thread/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
Are you looking for vulnerabilities in the right places? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ben Hirschberg With the rapid pace of technological evolution, ensuring security within the systems we operate and the software we deploy has...
TeamViewer abused to breach networks in new ransomware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Ransomware actors are again using TeamViewer to gain initial access to organization endpoints and attempt to deploy encryptors based on...
CISA: Critical Ivanti auth bypass bug now actively exploited – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA warns that a critical authentication bypass vulnerability in Ivanti’s Endpoint Manager Mobile (EPMM) and MobileIron Core device management software...
Microsoft tests instant access to Android photos in Windows 11 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft plans to provide Windows 11 users with almost instant access to photos and screenshots they’ve taken on their Android smartphones....
Kansas State University cyberattack disrupts IT network and services – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Kansas State University (K-State) announced it is managing a cybersecurity incident that has disrupted certain network systems, including VPN, K-State...
Haier hits Home Assistant plugin dev with takedown notice – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Appliances giant Haier issued a takedown notice to a software developer for creating Home Assistant integration plugins for the company’s...
US govt wants BreachForums admin sentenced to 15 years in prison – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The United States government has recommended that Conor Brian Fitzpatrick, the creator and lead administrator of the now-defunct BreachForums hacking...
Credentials are Still King: Leaked Credentials, Data Breaches and Dark Web Markets – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Flare Infostealer malware is one of the most substantial and underappreciated risk vectors for corporate information security teams. Infostealers infect...
Google: Russian FSB hackers deploy new Spica backdoor malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google says the ColdRiver Russian-backed hacking group is pushing previously unknown backdoor malware using payloads masquerading as a PDF decryption tool....
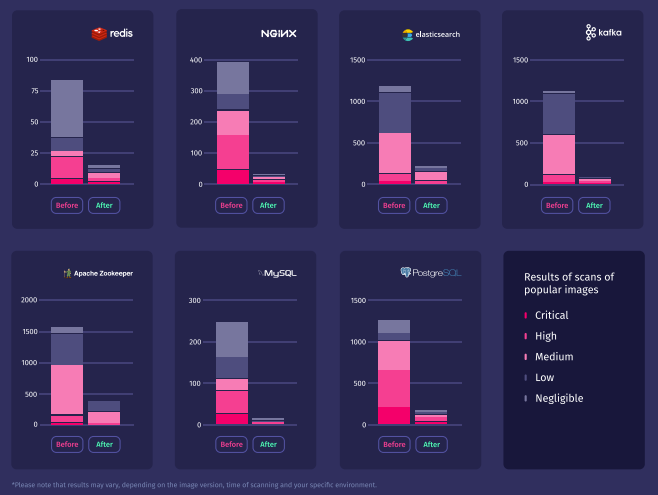
Docker hosts hacked in ongoing website traffic theft scheme – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new campaign targeting vulnerable Docker services deploys an XMRig miner and the 9hits viewer app on compromised hosts, allowing...
Jira down: Atlassian outage affecting multiple cloud services – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Multiple Atlassian Jira products are experiencing an ongoing outage as of this morning. Users of Jira Work management, Jira Software,...
Popular GPUs Used AI Systems Vulnerable to Memory Leak Flaw – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development LeftoverLocals Affects Apple, AMD and Qualcomm Devices Akshaya Asokan (asokan_akshaya)...
Swiss Government Reports Nuisance-Level DDoS Disruptions – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Self-Proclaimed Russian Hacktivists Continue Putin-Aligned Information Operations Mathew...