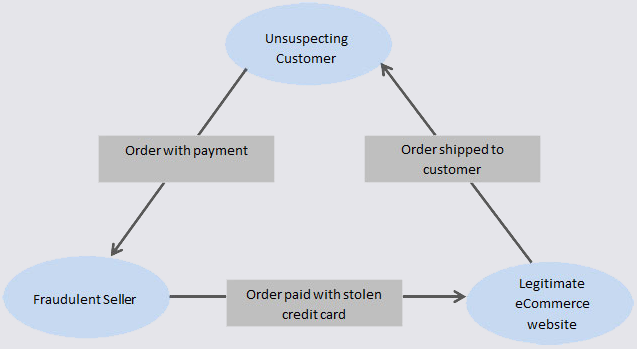
Source: krebsonsecurity.com – Author: BrianKrebs A Canadian man who says he’s been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name....
Day: January 19, 2024
Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 19, 2024NewsroomMalware / Endpoint Security Pirated applications targeting Apple macOS users have been observed containing a backdoor capable of granting...
Payoneer accounts in Argentina hacked in 2FA bypass attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Numerous Payoneer users in Argentina report waking up to find that their 2FA-protected accounts were hacked and funds stolen after...
CISA emergency directive: Mitigate Ivanti zero-days immediately – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA issued this year’s first emergency directive ordering Federal Civilian Executive Branch (FCEB) agencies to immediately mitigate two Ivanti Connect...
FTC bans one more data broker from selling your location info – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The U.S. Federal Trade Commission (FTC) continues to target data brokers, this time in a settlement with InMarket Media, which...
Chinese hackers exploit VMware bug as zero-day for two years – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A Chinese hacking group has been exploiting a critical vCenter Server vulnerability (CVE-2023-34048) as a zero-day since at least late...
Vans, North Face owner says ransomware breach affects 35 million people – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VF Corporation, the company behind brands like Vans, Timberland, The North Face, Dickies, and Supreme, said that more than 35...
VMware confirms critical vCenter flaw now exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VMware has confirmed that a critical vCenter Server remote code execution vulnerability patched in October is now under active exploitation....
This Top-Rated Data Recovery Tool is More Than $100 Off Now – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 19, 2024 Updated January 17, 2024 We may earn from vendors via affiliate links or sponsorships. This might...
35.5 million customers of major apparel brands have their data breached after ransomware attack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Bought some Timberland shoes? Wear a North Face jacket? You, and millions of purchasers of other popular high-street brands, could...
VF Corp Says Data Breach Resulting From Ransomware Attack Impacts 35 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Apparel and footwear brands owner VF Corp shares more details on the impact of a December 2023 ransomware attack. The...
US Gov Publishes Cybersecurity Guidance for Water and Wastewater Utilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire CISA, FBI and EPA document aims to help water and wastewater organizations improve their cyber resilience and incident response. The...
Ivanti EPMM Vulnerability Targeted in Attacks as Exploitation of VPN Flaws Increases – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The number of Ivanti VPN appliances compromised through exploitation of recent flaws increases and another vulnerability is added to exploited...
VMware vCenter Server Vulnerability Exploited in Wild – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs VMware warns customers that CVE-2023-34048, a vCenter Server vulnerability patched in October 2023, is being exploited in the wild. The...
Top Official Says Kansas Courts Need at Least $2.6 Million to Recover From Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Kansas Courts needs funding to cover the costs of bringing computer systems back online, pay vendors, improve cybersecurity and hire...
Unpatched Rapid SCADA Vulnerabilities Expose Industrial Organizations to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Seven vulnerabilities found in Rapid SCADA could be exploited to gain access to sensitive industrial systems, but they remain unpatched....
Software Supply Chain Security Startup Kusari Raises $8 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Kusari has raised $8 million to help organizations gain visibility into and secure their software supply chain. The post Software...
Nigerian Businesses Face Growing Ransomware-as-a-Service Trade – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: Pablo Lagarto via Alamy Stock Photo Ransomware-as-a-service looks set to fuel an increase in attack in Nigeria,...
Google: Russia’s ColdRiver APT Unleashes Custom ‘Spica’ Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo The Russia-backed advanced persistent threat...
Threat Actors Team Up for Post-Holiday Phishing Email Surge – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: devilmaya via Alamy Stock Photo Last week, two different threat actors teamed up to send thousands of...
Citrix Discovers 2 Vulnerabilities, Both Exploited in the Wild – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading 2 Min Read Source: Monticello via Shutterstock Two vulnerabilities have been found in NetScaler ADC and...
Cybercrooks Target Docker Containers With Novel Pageview Generator – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading 2 Min Read Source: Bob Sharples via Alamy Stock Photo Container-focused cyberattackers have a brand-new...
Nigerian Law Enforcement Agency Advised to Retrain African Cybercriminals – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Mykhailo Polenok via Alamy Stock Photo Online scammers and fraudsters should be retrained as information technology specialists, a...
Anti-Ransomware Coalition Bound to Fail Without Key Adjustments – Source: www.darkreading.com
Source: www.darkreading.com – Author: Shmuel Gihon Source: Olekcii Mach via Alamy Stock Photo COMMENTARY Ransomware is a pervasive issue affecting businesses of all sizes and industries,...
Russian Coldriver Hackers Deploy Malware to Target Western Officials – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Russian threat group Coldriver has expanded its targeting of Western officials with the use of malware to steal sensitive data, Google’s...
Experts Urge Clearer Direction in South Africa’s Cyber Strategy – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 South Africa, known to be ‘the world’s most internet-addicted country,’ finds itself plagued by the internet’s dark underbelly: ransomware. It is...
TA866 Resurfaces in Targeted OneDrive Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity researchers at Proofpoint have identified the resurgence of TA866 in email threat campaigns after a hiatus of nine months. Writing...
New Malware Campaign Exploits 9hits in Docker Assault – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have uncovered a novel cyber-attack campaign targeting vulnerable Docker services. The attacks mark the first documented case of malware...
Npm Trojan Bypasses UAC, Installs AnyDesk with “Oscompatible” Package – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 19, 2024NewsroomSoftware Security / Spyware A malicious package uploaded to the npm registry has been found deploying a sophisticated remote...
U.S. Cybersecurity Agency Warns of Actively Exploited Ivanti EPMM Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 19, 2024NewsroomCyber Theat / Zero-Day The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched critical flaw...