Source: thehackernews.com – Author: . Jan 18, 2024NewsroomCyber Espionage / Threat Intelligence High-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium,...
Day: January 18, 2024
NCSC Builds New “Cyber League” Threat Tracking Community – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 One of the UK’s leading cybersecurity agencies has announced plans to convene a new group of industry experts who will help...
AI, Gaming, FinTech Named Major Cybersecurity Threats For Kids – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The heightened utilization of AI tools and potential vulnerabilities in gaming have been identified as crucial cybersecurity concerns for children in...
iShutdown lightweight method allows to discover spyware infections on iPhones – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini iShutdown lightweight method allows to discover spyware infections on iPhones Researchers devised a “lightweight method,” called iShutdown, to determine whether Apple iOS...
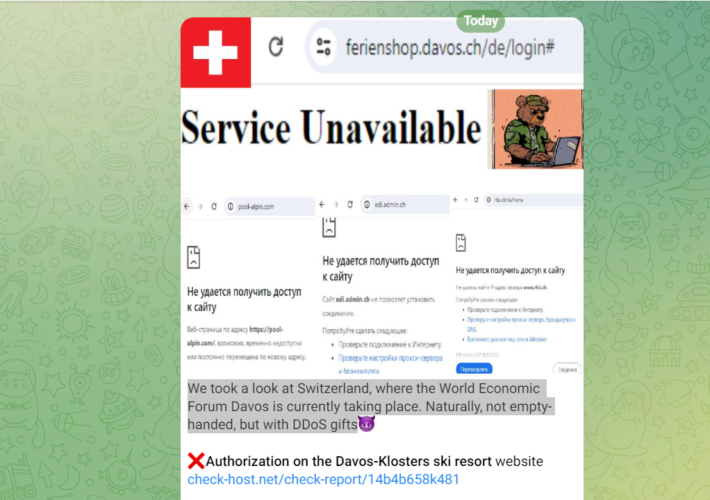
Pro-Russia group hit Swiss govt sites after Zelensky visit in Davos – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pro-Russia group hit Swiss govt sites after Zelensky visit in Davos Switzerland believes that the attack claimed by pro-Russian group...
Github rotated credentials after the discovery of a vulnerability – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Github rotated credentials after the discovery of a vulnerability GitHub rotated some credentials after the discovery of a flaw that...
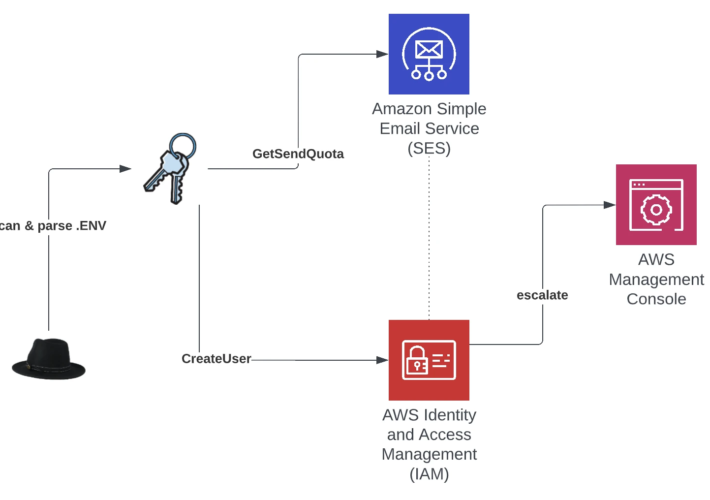
FBI, CISA warn of AndroxGh0st botnet for victim identification and exploitation – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini FBI, CISA warn of AndroxGh0st botnet for victim identification and exploitation U.S. CISA and the FBI warned of AndroxGh0st malware used to...
Citrix warns admins to immediately patch NetScaler for actively exploited zero-days – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Citrix warns admins to immediately patch NetScaler for actively exploited zero-days Citrix fixed two actively exploited zero-day vulnerabilities impacting Netscaler...
Have I Been Pwned adds 71 million emails from Naz.API stolen account list – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Have I Been Pwned has added almost 71 million email addresses associated with stolen accounts in the Naz.API dataset to...
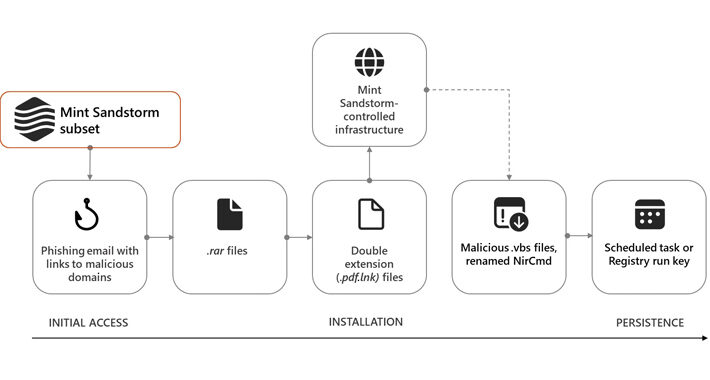
Microsoft: Iranian hackers target researchers with new MediaPl malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says that a group of Iranian-backed state hackers are targeting high-profile employees of research organizations and universities across Europe...
Bigpanzi botnet infects 170,000 Android TV boxes with malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A previously unknown cybercrime syndicate named ‘Bigpanzi’ has been making significant money by infecting Android TV and eCos set-top boxes...
CISA pushes federal agencies to patch Citrix RCE within a week – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Today, CISA ordered U.S. federal agencies to secure their systems against three recently patched Citrix NetScaler and Google Chrome zero-days...
iShutdown scripts can help detect iOS spyware on your iPhone – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers found that infections with high-profile spyware Pegasus, Reign, and Predator could be discovered on compromised Apple mobile devices...
AMD, Apple, Qualcomm GPUs leak AI data in LeftoverLocals attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new vulnerability dubbed ‘LeftoverLocals’ affecting graphics processing units from AMD, Apple, Qualcomm, and Imagination Technologies allows retrieving data from...
Wazuh: Building robust cybersecurity architecture with open source tools – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Wazuh Cybersecurity architecture refers to the design and structure of an organization’s approach to securing its information systems. It outlines...
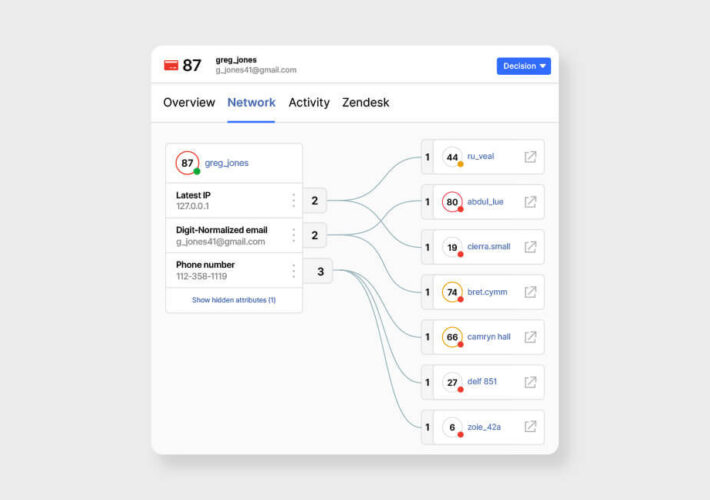
A fortified approach to preventing promo, bonus, and other multi-account abuse – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Product Team The world of iGaming is fiercely competitive, and attracting and retaining players is a constant challenge. Promotions and affiliate...
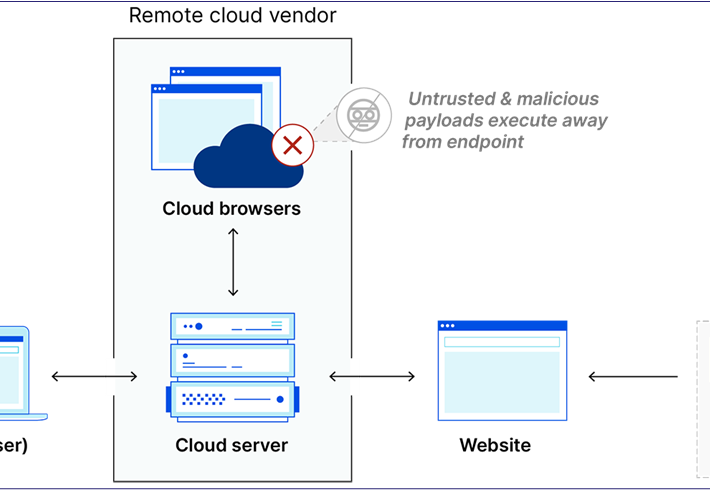
Calling Home, Get Your Callbacks Through RBI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lance B. Cain Authored By: Lance B. Cain and Alexander DeMine Overview Remote Browser Isolation (RBI) is a security technology which has...
Androxgh0st Malware: SafeBreach Coverage for US-CERT Alert (AA24-016A) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On January 16th, the Federal Bureau of Investigation (FBI) and the Cybersecurity and...
USENIX Security ’23 – FloatZone: Accelerating Memory Error Detection using the Floating Point Unit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Floris Gorter, Enrico Barberis, Raphael Isemann, Erik van der Kouwe, Cristiano Giuffrida, Herbert Bos Many thanks to USENIX for...
Over 178K SonicWall Firewalls Vulnerable to DoS, Potential RCE Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire A significant security concern has been raised for organizations using SonicWall next-generation firewalls (NGFW). Here’s what you need to know. ...
Taking on EvilProxy: Advancements in Phishing Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Vikas Shetty Thanks to various 2023 security reports, we know phishing attacks are now the most common form of cybercrime, with an...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #275 — Comic Agilé Consulting – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, January 17, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
News alert: Incogni study reveals overwhelming majority of spam calls originate locally – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido Los Angeles, Calif., Jan. 17, 2024 – Spam calls continue to be a major nuisance in the US, and advice on...
US Judge Again Says Meta Pixel Privacy Case Dismissal Unlikely – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Legislation & Litigation , Privacy Case Against Meta Likely Moving Forward After Court Heard Dismissal Arguments...
How a Novel Legal Maneuver Got a Hospital’s Stolen Data Back – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The ubiquity and anonymity of cryptocurrencies are fueling economic, legal and ethical challenges that put healthcare entities in the crosshairs of...
Chinese Drones Pose Threat to US Infrastructure, CISA Warns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security CISA, FBI Urge Critical Infrastructure Owners to Bolster UAS Security Measures Chris Riotta (@chrisriotta) • January 17, 2024...
Chrome Patches First Zero-Day of 2024 Exploited in the Wild – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Google Fixes Out-of-Bounds Memory Access Flaw, Microsoft Edge Browser Also Affected Mihir Bagwe (MihirBagwe) • January 17, 2024 Google...
OpenAI Combats Election Misinformation Amid Growing Concerns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Government , Industry Specific ChatGPT Maker Wants to Deter Use of AI in Online Election...