Source: securityaffairs.com – Author: Pierluigi Paganini Over 178,000 SonicWall next-generation firewalls (NGFW) online exposed to hack Researchers from Bishop Fox found over 178,000 SonicWall next-generation firewalls...
Day: January 16, 2024
Phemedrone info stealer campaign exploits Windows smartScreen bypass – Source: securityaffairs.com
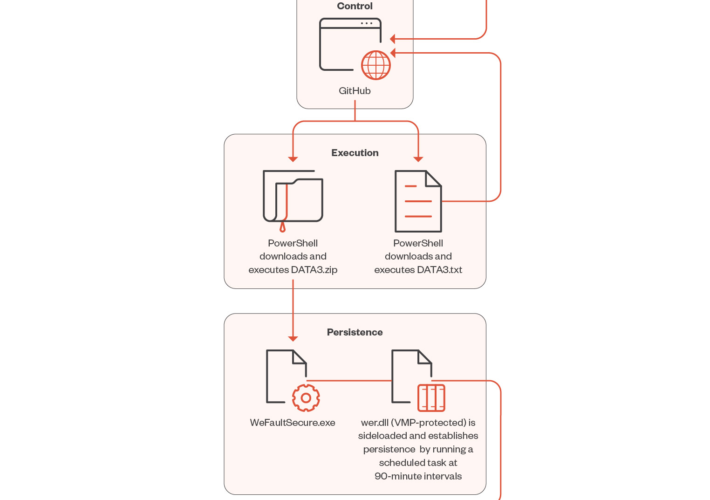
Source: securityaffairs.com – Author: Pierluigi Paganini Phemedrone info stealer campaign exploits Windows smartScreen bypass Threat actors exploit a recent Windows SmartScreen bypass flaw CVE-2023-36025 to deliver...
Balada Injector continues to infect thousands of WordPress sites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Balada Injector continues to infect thousands of WordPress sites Balada Injector malware infected more than 7100 WordPress sites using a...
Attackers target Apache Hadoop and Flink to deliver cryptominers – Source: securityaffairs.com
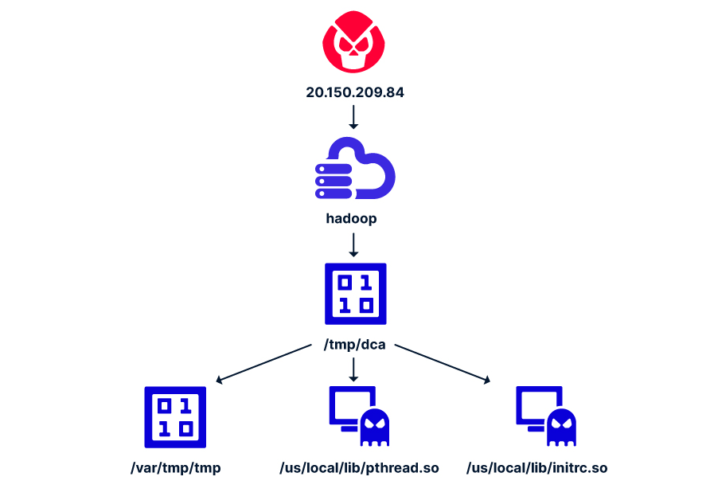
Source: securityaffairs.com – Author: Pierluigi Paganini Attackers target Apache Hadoop and Flink to deliver cryptominers Researchers devised a new attack that exploits misconfigurations in Apache Hadoop...
SOC ANALYST SERIES
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Detecting the Unknown: A Guide to Threat Hunting
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THREAT HUNTING MALWARE INFRASTRUCTURE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
TOP ASIA/APAC CYBERSECURITY THREATS OF 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Infra Pentest Course
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Information security aspects of Industrial Control Systems
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Compression Methods
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
IOS Hacking Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Tree of Attacks: Jailbreaking Black-Box LLMs Automatically
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Incident Response Play Book
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security Incident Response Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Incident Response Business Continuity Disaster Recovery
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
User Account Control / Uncontrol
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Using ISA/IEC 62443 Standards to Improve Control System Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Industry 4 0 Current Status and Future Trends
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Web Application Penetration Testing
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Web Security Testing Guide v4.2
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Windows Reverse Shell
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Hillstone ZTNA Solution
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Futures 2030 New Foundations
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Incident Response
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
HOW BREACH SIMULATION FITS INTO A MULTI LAYERED STRATEGY
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Identity Fraud Report 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Wireless Pentesting – CheatSheet
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Handbook for Cloud Risk Governance
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
hacking the infrastructure UPGRADE Visaggio
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...