The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: January 12, 2024
Pharmacies Giving Patient Records to Police without Warrants – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • January 11, 2024 8:58 AM @ ALL, Like the slow drip drip of the Chinese...
SMART CONTRACT SECURITY AUDIT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
HUMANIZING AI
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Playbooks Version 2.0
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Application Security Testing (AST) Explained – Source: securityboulevard.com
Source: securityboulevard.com – Author: Julie Peterson The typical global enterprise has over 12,000 web-based applications, including APIs, SaaS applications, servers, and databases. While these applications play...
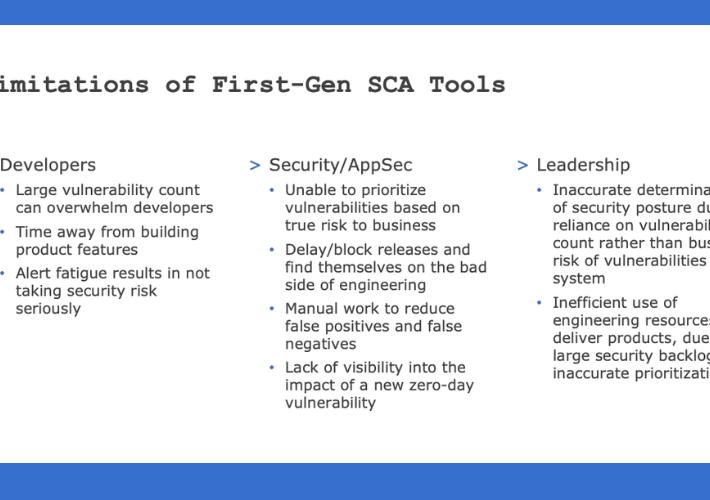
Prioritize Risk and Eliminate SCA Alert Fatigue with SCA 2.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dilan Krishnamurthy Countless data breaches are exposed daily, and finding the vulnerabilities that are leading to these breaches is extremely important. Businesses...
USENIX Security ’23 – Wenjun Zhu, Xiaoyu Ji, Yushi Cheng, Shibo Zhang, Wenyuan Xu ‘TPatch: A Triggered Physical Adversarial Patch’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, January 11, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
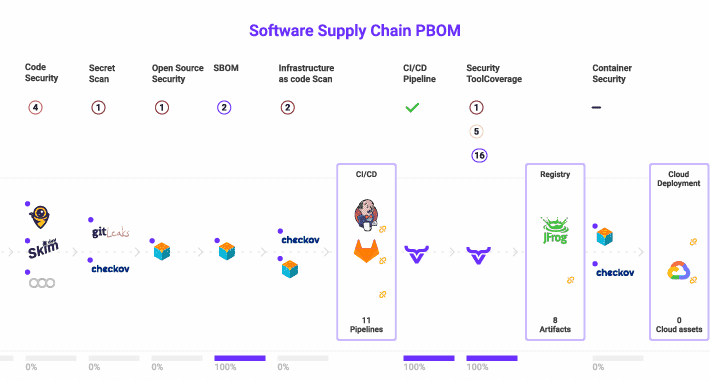
Three ways to manage cybersecurity tool sprawl in your software supply chain – Source: securityboulevard.com
Source: securityboulevard.com – Author: William Penfield Sprawl happens Software development organizations evolve. Teams grow. The number of projects increases. Tech stacks change. Technology and management decisions...
Netskope Report Surfaces Raft of Cybersecurity Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A report published by Netskope today revealed that, on average, 29 out of every 10,000 enterprise users clicked on a...
Cybercriminal Whistleblowers will Get Smarter – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joe Breen If you see something, say something and get paid by the SEC Under the SEC’s whistleblower program, “eligible whistleblowers are...
5 Ways MSPs Can Resolve a Hack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith If you are a managed service provider (MSP) handling small and medium-sized businesses (SMB) clients, there are some sobering stats...
Shopify DMARC Record Setup: Meet Google and Yahoo’s Sender Requirements – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc In response to evolving email authentication standards set by tech giants Google and Yahoo, third-party Email Service Providers (ESPs) like Shopify...
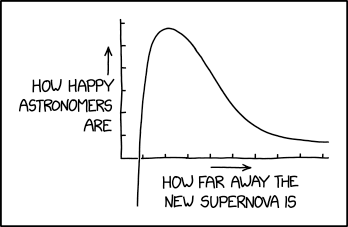
Randall Munroe’s XKCD ‘Supernova’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2024/01/randall-munroes-xkcd-supernova/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
Security firm Mandiant says it didn’t have 2FA enabled on its hacked Twitter account – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Anyone who works in computer security knows that they should have two-factor authentication (2FA) enabled on their accounts. 2FA provides...
Twitter says it’s not its fault the SEC’s account got hacked – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The safety team at Twitter (I refuse to call the site X because that’s the completely daft kind of name...
Smashing Security podcast #354: Chuck Norris and the fake CEO, artificial KYC, and an Airbnb scam – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Chuck Norris gives a helping hand to a mysterious cryptocurrency CEO who may have separated investors from over a billion...
CISA adds Ivanti and Microsoft SharePoint bugs to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Ivanti and Microsoft SharePoint bugs to its Known Exploited Vulnerabilities catalog U.S. Cybersecurity and Infrastructure Security Agency (CISA)...
Two zero-day bugs in Ivanti Connect Secure actively exploited – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Two zero-day bugs in Ivanti Connect Secure actively exploited Ivanti revealed that two threat actors are exploiting two zero-day vulnerabilities...
X Account of leading cybersecurity firm Mandiant was hacked because not adequately protected – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini X Account of leading cybersecurity firm Mandiant was hacked because not adequately protected The X account of cybersecurity firm Mandiant...
Cisco fixed critical Unity Connection vulnerability CVE-2024-20272 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cisco fixed critical Unity Connection vulnerability CVE-2024-20272 Cisco addressed a critical Unity Connection security flaw that can be exploited by...
Turkish Hackers Exploit MS SQL Servers to Deliver Ransomware – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Financially Motivated Actors Targeting US, EU and LATAM Countries Prajeet Nair (@prajeetspeaks) • January 11,...
Top Takeaways From the Hijacking of Mandiant’s X Account – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cryptocurrency Fraud , Fraud Management & Cybercrime , Social Media All Organizations That Use X Should Review Their Two-Factor Authentication Settings...
How the Merck Case Shapes the Future of Cyber Insurance – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Merck & Co.’s proposed settlement with insurers over a $1.4 billion claim related to the NotPetya attack will change the language...
Breach Roundup: FTC Bans Data Broker From Sharing Locations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations Also: Microsoft Fixes 48 Flaws in January Patch Tuesday But No Zero-Days Anviksha More...
LIVE Webinar | Legal Vigilance in the Zero Trust Galaxy: Sailing Through Data Privacy Waters – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Presented by LightBeam.AI 60 minutes Explore the evolving landscape of Zero Trust from a privacy and legal...
Cryptohack Roundup: It’s Raining Phishing Scams on X – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Bitcoin ETP, Gamma and dYdX Attacks, 2023 Hack Stats...
Attackers’ GitHub Abuse Poses Growing Risk, Researchers Warn – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Cybersecurity Researchers Detail Defenses Against Attackers Abusing Cloud Services Mathew J. Schwartz (euroinfosec) • January...
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...