Source: www.bleepingcomputer.com – Author: Lawrence Abrams U.S. mortgage lender loanDepot has suffered a cyberattack that caused the company to take IT systems offline, preventing online payments...
Day: January 7, 2024
Stealthy AsyncRAT malware attacks targets US infrastructure for 11 months – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A campaign delivering the AsyncRAT malware to select targets has been active for at least the past 11 months, using...
KyberSlash attacks put quantum encryption projects at risk – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Multiple implementations of the Kyber key encapsulation mechanism for quantum-safe encryption, are vulnerable to a set of flaws collectively referred to...
A cyber attack hit the Beirut International Airport – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A cyber attack hit the Beirut International Airport A cyber attack hit the Beirut International Airport, Rafic Hariri (Lebanon), threat...
Iranian crypto exchange Bit24.cash leaks user passports and IDs – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Iranian crypto exchange Bit24.cash leaks user passports and IDs Bit24.cash has inadvertently exposed sensitive data belonging to nearly 230,000 users,...
Security Affairs newsletter Round 453 by Pierluigi Paganini – INTERNATIONAL EDITION – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A cyber attack hit the Beirut International Airport | Iranian crypto exchange Bit24.cash leaks user passports and IDs | Security...
Turkish Sea Turtle APT targets Dutch IT and Telecom firms – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Turkish Sea Turtle APT targets Dutch IT and Telecom firms Sea Turtle cyber espionage group targeted telco, media, ISPs, IT...
Google: Malware abusing API is standard token theft, not an API issue – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Google is downplaying reports of malware abusing an undocumented Google Chrome API to generate new authentication cookies when previously stolen...
X users fed up with constant stream of malicious crypto ads – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Cybercriminals are abusing X advertisements to promote websites that lead to crypto drainers, fake airdrops, and other scams. Like all...
USENIX Security ’23 – “If I Could Do This, I Feel Anyone Could” *The Design And Evaluation Of A Secondary Authentication Factor Manager’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Garrett Smith, Tarun Yadav, Jonathan Dutson, Scott Ruoti, Kent Seamons“ Many thanks to USENIX for publishing their outstanding USENIX...
Mastering the Linux CLI: Unleashing the Power of Commands – Source: securityboulevard.com
Source: securityboulevard.com – Author: CyB3rBEA$T In the ever-evolving landscape of operating systems, Linux stands out as a robust and versatile solution that has captured the hearts...
What Is the FedRAMP Incident Response Control Family? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hyperproof Team Incident response is a critical piece of any enterprise cybersecurity strategy and is also a key component to achieving FedRAMP...
InfoSec Guide to Third Party Risk Management
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Implementation GuideISO/IEC 27001:2022
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ISO 27001 – 2022 Client Gap Analysis
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ISO 22301:2019 BUSINESS CONTINUITY STANDARD IMPLEMENTATION GUIDE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Introduction to Cybersecurity for Commercial Satellite Operations
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ILO – Protection of workers personal data
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Illicit Financial Flows Cyber Enabled Fraud
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
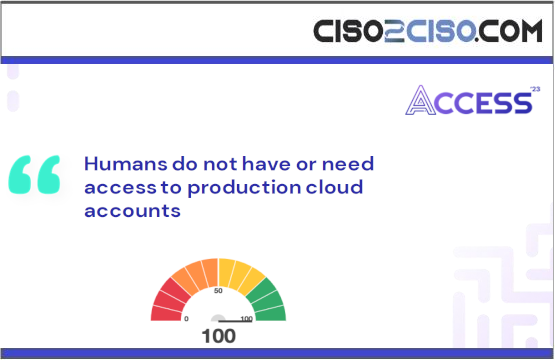
Identity Maturity in the Cloud – Humans do not have or need access to production cloud accounts
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Identidad Digital Corporativa INCIBE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
HPH Sector Mitigation Guide TLP CLEAR 508c
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How to Design a Secure Serverless Architecture
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How I Build Engaging Tabletop Exercises in 6 Steps
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Homeland Threat Assessment 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...