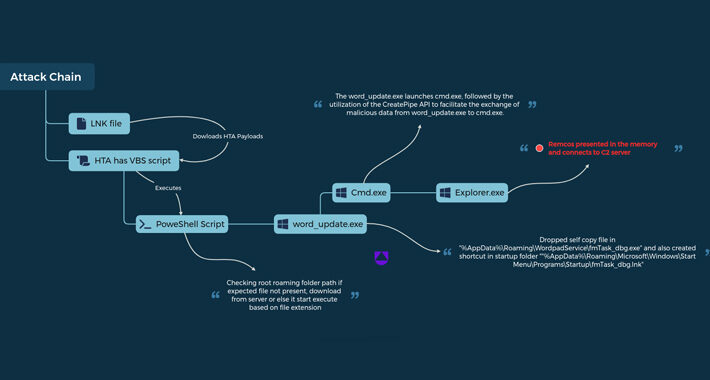
Source: thehackernews.com – Author: . Jan 04, 2024NewsroomSoftware Security / Malware The threat actor known as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT using...
Day: January 4, 2024
Mandiant’s Twitter Account Restored After Six-Hour Crypto Scam Hack – Source:thehackernews.com
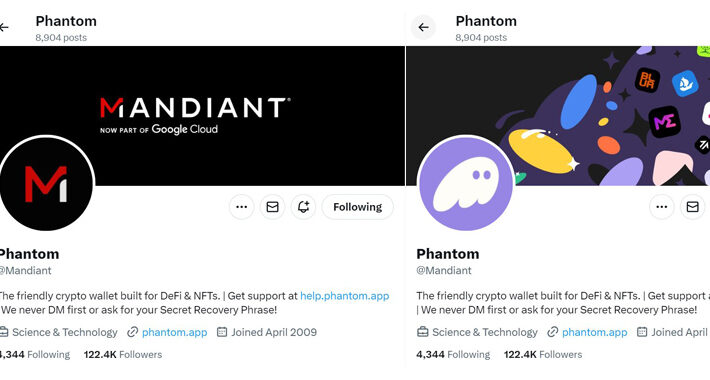
Source: thehackernews.com – Author: . Jan 04, 2024NewsroomCryptocurrency / Social Media American cybersecurity firm and Google Cloud subsidiary Mandiant had its X (formerly Twitter) account compromised...
Facial Recognition Systems in the US – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier A helpful summary of which US retail stores are using facial recognition, thinking about using it, or currently not planning...
Live Webinar | Dancing with Shadows: Vendor Risk Management in the Age of AI and Cyber Intrigue – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Nate Smolenski Head of Cyber Intelligence Strategy, Netskope Nate Smolenski is an experienced CISO, Advisor, and technology leader with over two...
Aqua Security Scores $60M Series E Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Late-stage player in the CNAPP space secures a $60 million extended Series E funding round at a valuation north of...
SentinelOne Snaps up Seed-Stage CNAPP Startup PingSafe – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine SentinelOne plans to acquire PingSafe in a cash-and-stock deal that adds cloud native application protection platform (CNAPP) technologies. The post...
SonicWall Buys Banyan Security For ZTNA Technology – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine SonicWall announces the acquisition of Banyan Security, a deal that adds zero-trust network access tooling to its product portfolio. The...
Over 900k Impacted by Data Breach at Defunct Boston Ambulance Service – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The personal information of more than 900,000 individuals was stolen in a data breach at Fallon Ambulance Service. The post...
Several Infostealers Using Persistent Cookies to Hijack Google Accounts – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in Google’s authentication process allows malware to restore cookies and hijack user sessions. The post Several Infostealers Using...
Hacker Conversations: Runa Sandvik – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek interviews Runa Sandvik, a cybersecurity researcher focused on protecting journalists, defenders of human rights and lawyers, The post Hacker...
Uncertainty Is the Biggest Challenge to Australia’s Cyber Security Strategy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matthew Sainsbury Just the highlights Australia’s cyber security vision extends to 2030, with two federal elections occurring in that time frame. A...
Cybersecurity M&A Roundup: 25 Deals Announced in December 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Twenty-five cybersecurity-related merger and acquisition (M&A) deals were announced in December 2023. The post Cybersecurity M&A Roundup: 25 Deals Announced...
Palestinian Hackers Hit 100 Israeli Organizations in Destructive Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A group of claimed Palestinian state cyber warriors has hit over 100 Israeli organizations with wipers and data theft. The...
21 New Mac Malware Families Emerged in 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A total of 21 new malware families targeting macOS systems were discovered in 2023, a 50% increase compared to 2022. ...
Xerox Confirms Data Breach at US Subsidiary Following Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Xerox says personal information was stolen in a cyberattack at US subsidiary Xerox Business Solutions. The post Xerox Confirms Data...
Massive Fallon Ambulance Data Breach Impacts Nearly One Million People – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Transformative Healthcare announces Fallon Ambulance data breach exposed sensitive information of 911,757 customers. Fallon ceased operations in December 2022 but...
Democracy 2024: Stakes vs. Horses – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr The 2024 U.S. Presidential election isn’t just another tick on the political timeline. It’s a crucial juncture for — quite literally...
Top 3 SEC Cyber Rule Misconceptions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joe Breen Cloud Security, Governance and Skills in 2024 Step 1 of 6 16% Who in your organization is responsible for cloud...
The state of container security: 5 key steps to locking down your releases – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jai Vijayan Container technologies are rapidly transforming application development and deployment practices at many organizations. But they also present a minefield of...
USENIX Security ’23 – Bingyu Shen, Tianyi Shan, Yuanyuan Zhou – ‘Improving Logging to Reduce Permission Over-Granting Mistakes’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Comprehensive Guide to Fraud Detection, Management, & Analysis – Source: securityboulevard.com
Source: securityboulevard.com – Author: Webzoly SEO Fraud is everywhere, and it’s affecting you whether you realize it or not. From fraudulent credit card charges to identity...
Q4 2023 Security Use Cases: Insights From Success Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast As part of Success Services, this past quarter LogRhythm consultants have been hard at work helping customers improve their defenses...
The Complete Guide to Smishing (SMS Phishing) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Webzoly SEO It’s unfortunately become an all-to-common scenario: you’re waiting for a package to be delivered—but then you receive an SMS text...
Abnormal Security Shares Examples of Attacks Using Generative AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Abnormal Security has published examples of cyberattacks that illustrate how cybercriminals are beginning to leverage generative artificial intelligence (AI) to...
Addressing the Rising Threat of API Leaks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jaweed Metz In the realm of cybersecurity, the metaphor of “Leaky Buckets” has become an increasingly prevalent concern, particularly in the context...
Randall Munroe’s XKCD ‘Iceland’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Industry 4.0 and OT security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
INFORMATION SECURITY MANAGEMENT PRINCIPLES
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DNS Security Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DNS LAYER SECURITY FROM THE MITRE ATT&CK PERSPECTIVE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...