Source: www.securityweek.com – Author: Associated Press The hacking of a municipal water plant is prompting new warnings from U.S. security officials at a time when governments...
Day: January 3, 2024
Are Security Appliances fit for Purpose in a Decentralized Workplace? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Etay Maor Security appliances are amongst the most riskiest enterprise devices and are a often method for threat actors to infiltrate a...
Free Decryptor Released for Black Basta Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in Black Basta ransomware’s encryption algorithm allows researchers to create a free decryptor. The post Free Decryptor Released...
New DLL Search Order Hijacking Technique Targets WinSxS Folder – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Attackers can abuse a new DLL search order hijacking technique to execute code in applications within the WinSxS folder. The...
Steam drops support for Windows 7 and 8.1 to boost security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Steam is no longer supported on Windows 7, Windows 8, and Windows 8.1 as of January 1, with the company...
Orbit Chain loses $86 million in the last fintech hack of 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Orbit Chain has experienced a security breach that has resulted in a loss of $86 million in cryptocurrency, particularly Ether,...
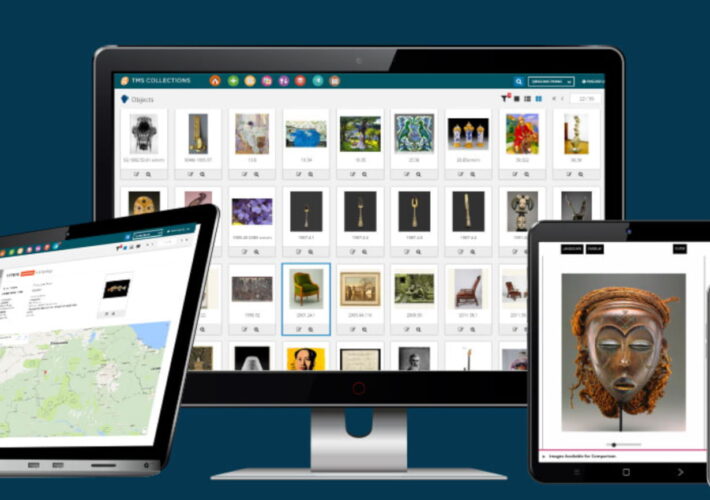
Online museum collections down after cyberattack on service provider – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Museum software solutions provider Gallery Systems has disclosed that its ongoing IT outages were caused by a ransomware attack last...
Xerox says subsidiary XBS U.S. breached after ransomware gang leaks data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The U.S. division of Xerox Business Solutions (XBS) has been compromised by hackers with a limited amount of personal information...
Google Groups is ending support for Usenet to combat spam – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google has officially announced it’s ceasing support for Usenet groups on its Google Groups platform, a move partly attributed to...
Victoria court recordings exposed in reported ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Australia’s Court Services Victoria (CSV) is warning that video recordings of court hearings were exposed after suffering a reported Qilin...
The law enforcement operations targeting cybercrime in 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams In 2023, we saw numerous law enforcement operations targeting cybercrime operations, including cryptocurrency scams, phishing attacks, credential theft, malware development,...
The biggest cybersecurity and cyberattack stories of 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams 2023 was a big year for cybersecurity, with significant cyberattacks, data breaches, new threat groups emerging, and, of course, zero-day...
TikTok Editorial Analysis – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier TikTok seems to be skewing things in the interests of the Chinese Communist Party. (This is a serious analysis, and...
New SEC Cybersecurity Reporting Rules Take Effect – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tova Osofsky In July 2023 the US Security and Exchange Commission (SEC) issued new rules on “Cybersecurity Risk Management, Strategy, Governance, and...
USENIX Security ’23 – Cong Zhang, Yu Chen, Weiran Liu, Min Zhang, Dongdai Lin – ‘Linear Private Set Union From Multi-Query Reverse Private Membership Test’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
GKE Case Highlights Risks of Attackers Chaining Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Palo Alto Network’s cybersecurity recently outlined two vulnerabilities it found in Google Kubernetes Engine (GKE) that, individually, don’t represent much...
Google Cloud Report Spotlights 2024 Cybersecurity Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard As the New Year dawns, a cybersecurity report from Google Cloud suggests that while there are many challenges ahead, it...
GUEST ESSAY: Leveraging DevSecOps to quell cyber risks in a teeming threat landscape – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Yuga Nugraha In today’s digital landscape, organizations face numerous challenges when it comes to mitigating cyber risks. The constant evolution...
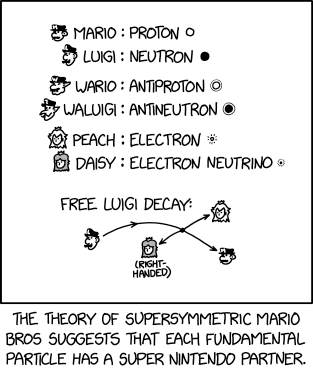
Randall Munroe’s XKCD ‘Supersymmetry’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
What is Security Posture? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Security posture is a term often mentioned in cybersecurity, with businesses often told to improve or maintain a robust security...
Exploiting an API with Structured Format Injection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp Never trust user input. It’s been the mantra for years in popular secure coding books. Yet, even today, we continue...
Google Whistles While OAuth Burns — ‘MultiLogin’ 0-Day is 70+ Days Old – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Infostealer scrotes having a field day with unpatched vulnerability. A zero-day vulnerability, publicly revealed in October, is still unpatched. Google’s...
Top 5 Cyber Predictions for 2024: A CISO Perspective – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepen Desai Amidst the ever-evolving realm of enterprise security, a new year unfolds, introducing a dynamic array of emerging threats. While the...
State AG Hits Hospital With $300K Fine for Web Tracker Use – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , HIPAA/HITECH NewYork-Presbyterian Disabled Website, Patient Portal Trackers in 2022 Marianne Kolbasuk McGee (HealthInfoSec) •...
European Central Bank to Put Banks Through Cyber Stress Test – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Governance & Risk Management , Industry Specific 109 Banks to Participate in Simulated Cyberattacks to Assess Cyber...
Merry ‘Leaksmas’! Hackers Give Away 50 Million Pieces of PII – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Holiday Leaks Could Result in More Digital Identity Theft and...
LockBit 3.0 Claims Attack on Australian Auto Dealer Eagers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Ransomware Eagers Says It Doesn’t Know Full Extent of Hack But Has Started...