The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2023
Security Operations Center Guidebook – A Practical Guide for a Successful SOC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How to Build a Security Operation Center in Budget by AT&T Cybersecurity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
State of ICS Security in the Age of Cloud by CSA
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
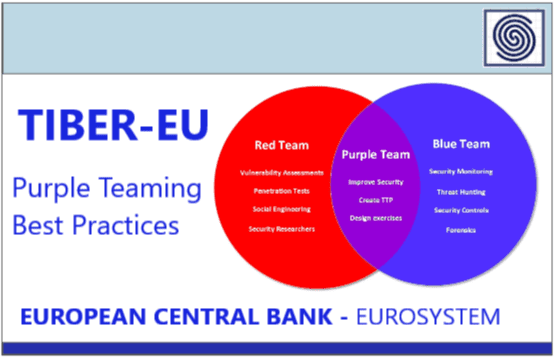
TIBER-EU – Purple Teaming Best Practices – European Central Bank
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Turning a Cybersecurity Strategy Into Reality – A Holistic Performance Management Framework by Boston Consulting Group & Saudi Telecomunication Company
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
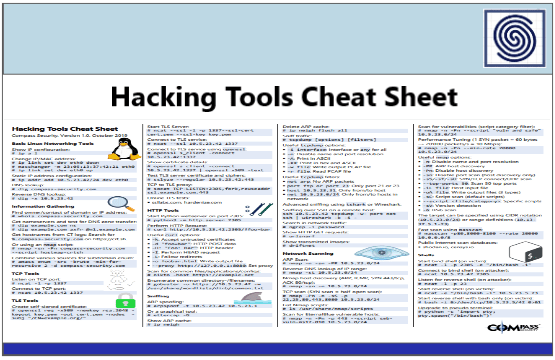
Hacking Tools Cheat Sheet by Compass Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2022 VEEAM Ransomware Trends Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ENISA THREAT LANDSCAPE FOR RANSOMWARE ATTACK REPORT JULY 2022
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
MITRE ATTACK Framework Everything Yoy Need to Know by Hackercombat
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Threat Intelligence in Government by UK Cyber Security Programme Digital Data and Technology DDT.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Enabling 5G Security with Continuos Monitoring by Booz Allen Hamilton
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Complete Guide to Implementing DevSecOps in AWS by aspire
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
State of Kubernetes Security Report 2022 by RedHat
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
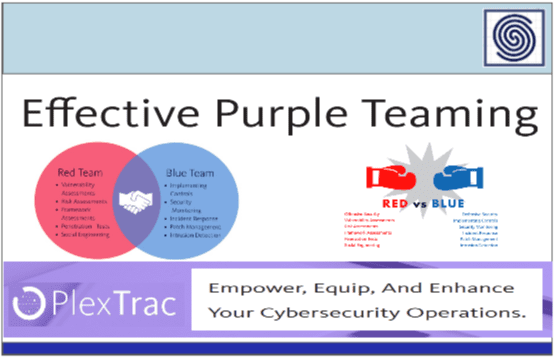
Effective Purple Teaming by PlexTrac
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
BOMA Canada 2022 Cyber Incidents Response Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Modern Malware for Dummies
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
API Security for Dummies Series – Data Theorem Special Edition
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The State of SIEM Detection Risk 2022 Report – Quantifying the gaps in MITRE ATT&CK coverage for productions SIEMs
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Advancing Supply Chain Security in Oil and Gas an Industry Analysis by World Economic Forum
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Introduction to Malware Analysis for Beginners by LetsDefend
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CROWDSTRIKE 2022 Global Threat Report by George Kurtz
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
7 Best Reasons to be a CISO by Michaell Hill UK Editor CSO
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
TELECOM SECURITY INCIDENTS REPORT 2021 BY ENISA
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Nozomi OT IoT Security Report – Cyber War Insights, Threats and Trends, Recommendations
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Allianz 2022 Risk Barometer – The most important business risks for the next 12 months and beyond, based on the insight of 2,650 risk management experts from 89 countries and territories.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Developing Cyber Security as a Profession – A report by the Global Forum on Cyber Security Expertise.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NSA’S Top Ten Cybersecurity Mitigation Strategies
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
COBIT ISACA 5 – A Business Framework for the Governance and Management of Enterprise IT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Guide to Cyber Risk – Managing the Impact of Increasing Interconnectivity by Allianz
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...