The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2023
Cybersecurity for SCADA Systems by William T. Shaw
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Kubernetes Security Guide by Sysdig
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Art of Recognizing and Surviving SOC Burnout – A complete Manual for Security Operations Professionals.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Guidance for Reducing data exfiltration by malicious insiders by National Cyber Security Centre (NCSC)
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
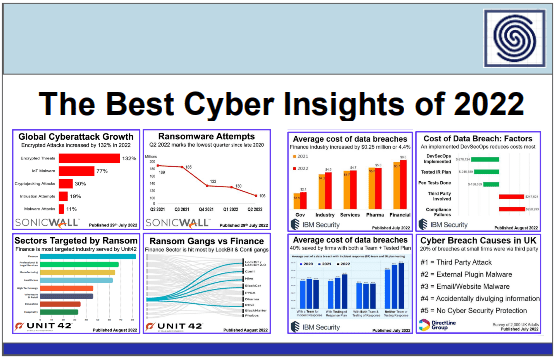
The Best Cyber Insights of 2022 by The Cyber Rescue Alliance
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security Cost Effectiveness for Business Risk Reduction by Cambridge Centre for Risk Studies and Bitsight
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
81 Siem Very important Use Cases for your SOC by SPLUNK
Splunk Use Cases Tags: Splunk 1- Windows Audit Log Tampering Check for any tampering done to Windows audit logs. 2- Finding Large Web Uploads Find large file...
Public Power Cyber Incident Response Playbook by American Public Power Association
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Securing the cloud by design and by Default by NCSC.GOV.UK – To reduce data breaches from cloud services, seek out providers who ensure functionality is ‘secure by default’
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
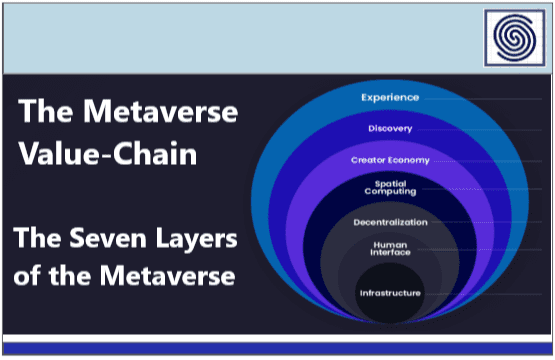
The Metaverse Value Chain – The Seven Layers of the Metaverse by Jon Radoff
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DDoS Threat Landscape Report Q2 2022 by Imperva
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Professional Red Teaming – Conducting Successful Cybersecurity Engagements by Jacob G Oakley – Apress
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Undestanding the Open Cybersecurity Schema Framework by Paul Agbabian.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
TOP Threats to Cloud Computing – Pandemic Eleven 2022 by Cloud Security Alliance report.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Guide for Multi-Cloud Read Team AWS – GCP – AZURE by Joas Antonio
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Endgame Guide to Threat Hunting by Paul Ewing & Devon Kerr
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
History of Supply Chain Attacks in the News by SentinelOne
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ransomware in a Global Context Report 2021 by Virustotal
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
40 Methods for Privilege Escalation P1 by Hadess
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Chemical Sector Cybersecurity – Framework Implementation Guidance by CISA
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Checkpoint Cyber Attack Trend 2022 Mid Year Report by Check Point Research
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
State of ICS Security in the Age of Cloud by CSA
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
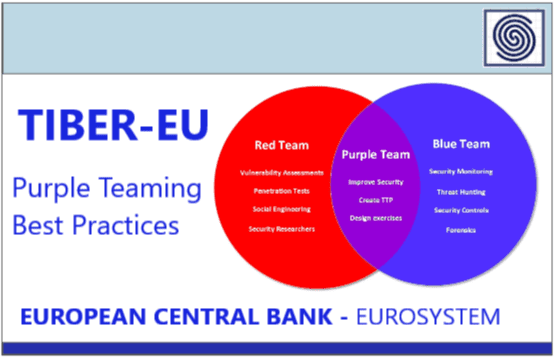
TIBER-EU – Purple Teaming Best Practices – European Central Bank
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Threat Intelligence in Government by UK Cyber Security Programme Digital Data and Technology DDT.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
BOMA Canada 2022 Cyber Incidents Response Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CROWDSTRIKE 2022 Global Threat Report by George Kurtz
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Allianz 2022 Risk Barometer – The most important business risks for the next 12 months and beyond, based on the insight of 2,650 risk management experts from 89 countries and territories.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Developing Cyber Security as a Profession – A report by the Global Forum on Cyber Security Expertise.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
COBIT ISACA 5 – A Business Framework for the Governance and Management of Enterprise IT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...