Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Over the weekend, security researchers released a proof-of-concept (PoC) exploit for a maximum severity remote code execution vulnerability in Progress...
Year: 2023
Arm warns of Mali GPU flaws likely exploited in targeted attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Arm in a security advisory today is warning of an actively exploited vulnerability affecting the widely-used Mali GPU drivers. The...
Motel One discloses data breach following ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Motel One Group has announced that it has been targeted by ransomware actors who managed to steal some customer...
FBI warns of surge in ‘phantom hacker’ scams impacting elderly – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The FBI issued a public service announcement warning of a significant increase in ‘phantom hacker’ scams targeting senior citizens across...
9 Secrets Management Strategies that every company should adopt – Source: securityboulevard.com
Source: securityboulevard.com – Author: Itzik Alvas. Co-founder & CEO, Entro While you might know your secrets vaults to store your organization’s most sensitive assets — API...
Launching Tomorrow: CyberPsych Podcast with Dr. Stacy Thayer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Netography Team Launching Tomorrow: CyberPsych Podcast with Dr. Stacy Thayer I have been studying cyberpsychology since 2002 and the most common question...
DEF CON 31 – Joseph Gabay’s ‘Warshopping- Phreaking Smart Shopping Cart Wheels Through RF Sniffing’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
How to Stop Phishing Attacks with Protective DNS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Zia Hotaki Phishing Threats Are Increasing in Scale and Sophistication Phishing remains one of the most dangerous and widespread cybersecurity threats. This...
Choosing the Unified SASE Provider: The Execution Isolation Factor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Srini Addepalli Shared Processes for Packet-level Security Technologies Networking and security technologies at the packet level, such as stateful inspection firewalls, IPSEC,...
Seceon Announces aiXDR-PMax at DattoCon23 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pushpendra Mishra Seceon, the pioneer of the first cybersecurity platform that augments and automates security operations services for MSPs and MSSPs, with an AI and...
Unlocking the Secrets of Hardened Secure Endpoint in 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Introduction Endpoint security is a critical component of a comprehensive cybersecurity strategy, especially for small businesses. It focuses on safeguarding...
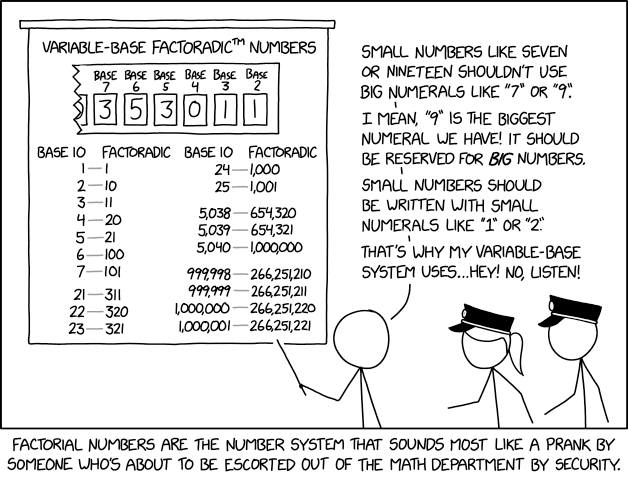
Randall Munroe’s XKCD ‘Factorial Numbers’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
FedRAMP and Federal Cybersecurity Market Roundup September 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Sherman It’s been a few weeks now since Carahsoft’s FedRAMP Headliner Summit, but there is no shortage of moments to recall...
Threat Groups Accelerating the Use of Dual Ransomware Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Ransomware groups are shrinking the time between attacks on the same victim, sometimes targeting the same company twice within 48...
Must-read Cyber Security Awareness Month insights from an industry expert – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Lari Luoma has over 20 years of experience working in the fields of security and networking. For the last 11 years,...
GUEST ESSAY: Has shielding and blocking electromagnetic energy become the new normal? – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Nikoline Arns Surrounded by the invisible hum of electromagnetic energy, we’ve harnessed its power to fuel our technological marvels for...
EU Lawmaker Questions CSAM Proposal ‘Conflicts of Interest’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Encryption & Key Management , Legislation & Litigation , Security Operations LIBE Committee Chair Seeks Clarifications from EU Home Affairs Minister...
Some Prospect Medical Hospitals in Dire State, Post-Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Continued Operation of 3 Connecticut Hospitals Now in Question Marianne Kolbasuk McGee...
Live Webinar ANZ | Achieving Air Gapped Security on VMs in Azure – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Alert: Attackers Actively Exploiting WS_FTP Vulnerabilities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Attack Surface Management , Critical Infrastructure Security Cybersecurity Officials Recommend Immediate Patching to Fix Serious Flaws...
Chertoff Group Arm to Buy Trustwave from Singtel for $205M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Managed Detection & Response (MDR) , Managed Security Service Provider (MSSP) MSSP, MDR Provider Lost Nearly...
Common Errors When Connecting Multiple iPhones to One Apple ID – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Erik Eckel Although connecting two iPhones to the same Apple ID has its advantages — including expanding your or a partner’s access...
Cyberghost VPN Review (2023): Features, Pricing, and Security – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares CyberGhost VPN Fast facts Our rating: 4.3 stars out of 5 Pricing: Starts at $2.11 per month Key features: Offers...
FBI Warns of Dual Ransomware Attacks and Data Destruction Trends – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Federal Bureau of Investigation (FBI) has issued a Private Industry Notification highlighting two concerning trends in the world of...
BunnyLoader Malware Targets Browsers and Cryptocurrency – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Zscaler ThreatLabz has identified a newly emerging Malware-as-a-Service (MaaS) threat known as “BunnyLoader,” available on underground forums. The tool, priced at...
AI-Generated Phishing Emails Almost Impossible to Detect, Report Finds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The potential for cybercriminals to use AI chatbots to create phishing campaigns has been cause for concern and now it has...
Nearly 100,000 Industrial Control Systems Exposed to the Internet – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Thousands of organizations around the world are using industrial control systems (ICS) exposed to the public internet, new analysis from Bitsight...
Cybersecurity Awareness Month Celebrates 20 Years – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity Awareness Month was founded in 2004 and this year sees the initiative celebrate 20 years of raising awareness of security...
Cigna Agrees $172m Payment to Settle Fraud Allegations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading health insurer has agreed to pay over $172m to resolve charges it seriously violated the False Claims Act by...
Royal Family Website Downed by DDoS Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The official website of the UK’s royal family was taken offline by a distributed denial of service (DDoS) attack on Sunday,...