FBI Says North Korean Hackers Behind $100 Million Horizon Bridge Crypto TheftThe U.S. Federal Bureau of Investigation (FBI) on Monday confirmed that North Korean threat actors...
Year: 2023
Chinese Hackers Utilize Golang Malware in DragonSpark Attacks to Evade Detection
Chinese Hackers Utilize Golang Malware in DragonSpark Attacks to Evade DetectionOrganizations in East Asia are being targeted by a likely Chinese-speaking actor dubbed DragonSpark while employing...
VMware Releases Patches for Critical vRealize Log Insight Software Vulnerabilities
VMware Releases Patches for Critical vRealize Log Insight Software VulnerabilitiesVMware on Tuesday released software to remediate four security vulnerabilities affecting vRealize Log Insight (aka Aria Operations for Logs)...
LastPass Parent Company GoTo Suffers Data Breach, Customers’ Backups Compromised
LastPass Parent Company GoTo Suffers Data Breach, Customers' Backups CompromisedLastPass-owner GoTo (formerly LogMeIn) on Tuesday disclosed that unidentified threat actors were able to steal encrypted backups...
North Korean Hackers Turn to Credential Harvesting in Latest Wave of Cyberattacks
North Korean Hackers Turn to Credential Harvesting in Latest Wave of CyberattacksA North Korean nation-state group notorious for crypto heists has been attributed to a new...
The Definitive Browser Security Checklist
The Definitive Browser Security ChecklistSecurity stakeholders have come to realize that the prominent role the browser has in the modern corporate environment requires a re-evaluation of...
Over 4,500 WordPress Sites Hacked to Redirect Visitors to Sketchy Ad Pages
Over 4,500 WordPress Sites Hacked to Redirect Visitors to Sketchy Ad PagesA massive campaign has infected over 4,500 WordPress websites as part of a long-running operation...
U.S. Federal Agencies Fall Victim to Cyber Attack Utilizing Legitimate RMM Software
U.S. Federal Agencies Fall Victim to Cyber Attack Utilizing Legitimate RMM SoftwareAt least two federal agencies in the U.S. fell victim to a "widespread cyber campaign"...
PY#RATION: New Python-based RAT Uses WebSocket for C2 and Data Exfiltration
PY#RATION: New Python-based RAT Uses WebSocket for C2 and Data ExfiltrationCybersecurity researchers have unearthed a new Python-based attack campaign that leverages a Python-based remote access trojan...
Announcing a stable release of sigstore-python
Announcing a stable release of sigstore-pythonBy William Woodruff Read the official announcement on the Sigstore blog as well! Trail of Bits is thrilled to announce the...
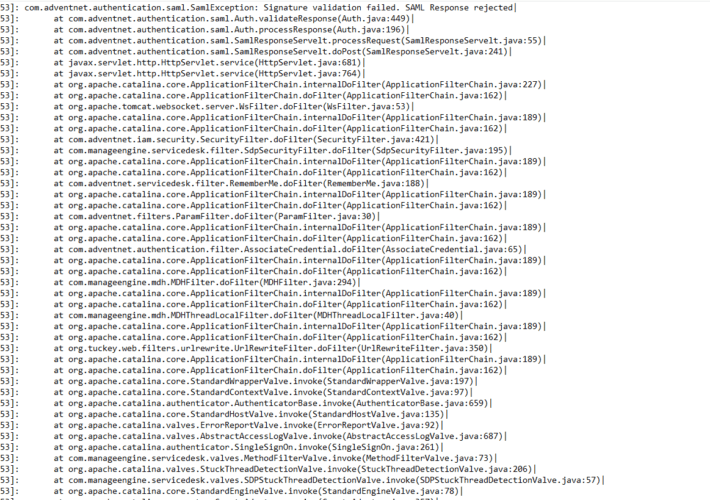
ManageEngine CVE-2022-47966 IOCs
ManageEngine CVE-2022-47966 IOCsIntroduction The recent ManageEngine CVE-2022-47966 is a pre-authentication remote code execution vulnerability. Depending on the specific ManageEngine product, this vulnerability is exploitable if SAML single-sign-on...
Hackers Can Abuse Visual Studio Marketplace to Target Developers with Malicious Extensions
Hackers Can Abuse Visual Studio Marketplace to Target Developers with Malicious ExtensionsA new attack vector targeting the Visual Studio Code extensions marketplace could be leveraged to...
USENIX Security ’22 – Theresa Stadler, Bristena Oprisanu, Carmela Troncoso ‘Synthetic Data – Anonymisation Groundhog Day’
USENIX Security ’22 – Theresa Stadler, Bristena Oprisanu, Carmela Troncoso ‘Synthetic Data – Anonymisation Groundhog Day’Our thanks to USENIX for publishing their Presenter’s outstanding USENIX Security...
Top SaaS Cybersecurity Threats in 2023: Are You Ready?
Top SaaS Cybersecurity Threats in 2023: Are You Ready?Cybercriminals will be as busy as ever this year. Stay safe and protect your systems and data by...
Yikes, Control Web Panel has Critical RCE — Patch NOW
Yikes, Control Web Panel has Critical RCE — Patch NOW Linanto’s popular web hosting control panel, CWP, has a nasty flaw. It’s easily exploitable—in fact, it’s being...
Randall Munroe’s XKCD ‘Washing Machine Settings’
Randall Munroe’s XKCD ‘Washing Machine Settings’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The post Randall Munroe’s XKCD ‘Washing...
Malicious PyPI Packages Using Cloudflare Tunnels to Sneak Through Firewalls
Malicious PyPI Packages Using Cloudflare Tunnels to Sneak Through FirewallsIn yet another campaign targeting the Python Package Index (PyPI) repository, six malicious packages have been found...
Control Web Panel Vulnerability, CVE-2022-44877, Actively Exploited in the Wild
Control Web Panel Vulnerability, CVE-2022-44877, Actively Exploited in the WildThis post offers details on the Control Web Panel Vulnerability, CVE-2022-44877, which is actively being exploited in...
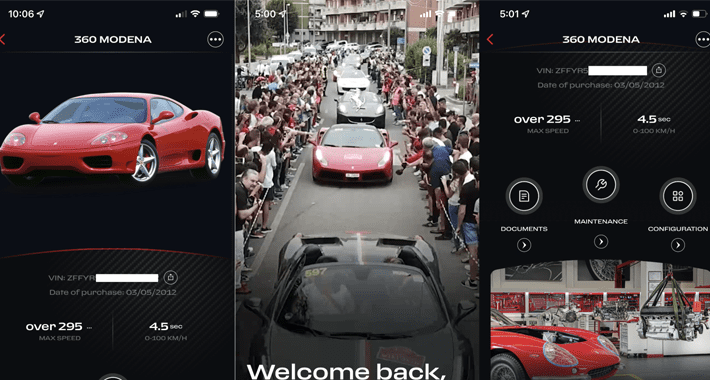
Millions of Vehicles at Risk: API Vulnerabilities Uncovered in 16 Major Car Brands
Millions of Vehicles at Risk: API Vulnerabilities Uncovered in 16 Major Car BrandsMultiple bugs affecting millions of vehicles from 16 different manufacturers could be abused to...
Sonatype Nexus Lifecycle Boosts Open Source Security and Dependency Management
Sonatype Nexus Lifecycle Boosts Open Source Security and Dependency Management The post Sonatype Nexus Lifecycle Boosts Open Source Security and Dependency Management appeared first on...
USENIX Security ’22 – Aloni Cohen, University of Chicago – ‘Attacks on Deidentification’s Defenses’
USENIX Security ’22 – Aloni Cohen, University of Chicago – ‘Attacks on Deidentification’s Defenses’Distinguished Paper Award Winner Our thanks to USENIX for publishing their Presenter’s outstanding...
Why Do User Permissions Matter for SaaS Security?
Why Do User Permissions Matter for SaaS Security?Earlier this year, threat actors infiltrated Mailchimp, the popular SaaS email marketing platform. They viewed over 300 Mailchimp customer accounts...
Tesla Factories Pollute Schools? A Story Nobody is Talking About
Tesla Factories Pollute Schools? A Story Nobody is Talking AboutFrom a long list of horrible societal harms from Tesla, some obviously criminal, this one surprised me...
New Study Uncovers Text-to-SQL Model Vulnerabilities Allowing Data Theft and DoS Attacks
New Study Uncovers Text-to-SQL Model Vulnerabilities Allowing Data Theft and DoS AttacksA group of academics has demonstrated novel attacks that leverage Text-to-SQL models to produce malicious...
Microsoft January Patch Tuesday 2023: 98 Security Vulnerabilities and a Zero Day
Microsoft January Patch Tuesday 2023: 98 Security Vulnerabilities and a Zero DayOn January 10th, 2023 Microsoft released their January Patch Tuesday fixes and revealed 98 vulnerability...
Kinsing Crypto Malware Hits Kubernetes Clusters via Misconfigured PostgreSQL
Kinsing Crypto Malware Hits Kubernetes Clusters via Misconfigured PostgreSQLThe threat actors behind the Kinsing cryptojacking operation have been spotted exploiting misconfigured and exposed PostgreSQL servers to obtain initial...
Severe Security Flaw Found in “jsonwebtoken” Library Used by 22,000+ Projects
Severe Security Flaw Found in "jsonwebtoken" Library Used by 22,000+ ProjectsA high-severity security flaw has been disclosed in the open source jsonwebtoken (JWT) library that, if...
Italian Users Warned of Malware Attack Targeting Sensitive Information
Italian Users Warned of Malware Attack Targeting Sensitive InformationA new malware campaign has been observed targeting Italy with phishing emails designed to deploy an information stealer...
Expert Analysis Reveals Cryptographic Weaknesses in Threema Messaging App
Expert Analysis Reveals Cryptographic Weaknesses in Threema Messaging AppA comprehensive analysis of the cryptographic protocols used in the Swiss encrypted messaging application Threema has revealed a...
StrongPity Hackers Distribute Trojanized Telegram App to Target Android Users
StrongPity Hackers Distribute Trojanized Telegram App to Target Android UsersThe advanced persistent threat (APT) group known as StrongPity has targeted Android users with a trojanized version of the...