Source: thehackernews.com – Author: . Oct 03, 2023The Hacker NewsNetwork Security / XDR / SIEM Security Configuration Assessment (SCA) is critical to an organization’s cybersecurity strategy....
Year: 2023
Hacking Gas Pumps via Bluetooth – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Hacking Gas Pumps via Bluetooth Turns out pumps at gas stations are controlled via Bluetooth, and that the connections...
New Malware-as-a-Service Gains Traction Among Cybercriminals – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Security experts have discovered BunnyLoader, a malware-as-a-service (MaaS) that is rapidly evolving and gaining popularity on different hacker platforms due...
How to DDoS Like an Ethical Hacker – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Before I tell you how to DDoS someone, I want to make a few issues clear. Launching a Distributed Denial...
Nexusflow Slots AI into SOC Automation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer While ChatGPT and other large language model (LLM) applications are either praised as the next “sliced bread” or...
Secure Yeti Appoints Jayson E. Street as Chief Adversarial Officer to Spearhead Cybersecurity Empowerment – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TULSA, Okla., Sept. 28, 2023 /PRNewswire/ — Secure Yeti, a leading global cybersecurity firm, proudly announces the appointment of renowned hacker Jayson E. Street as its first...
Visa Program Combats Friendly Fraud Losses For Small Businesses Globally – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO — (BUSINESS WIRE) — Today, Visa Inc. (NYSE:V), a world leader in digital payments, spotlighted the evolution of its...
In Search of Rust Developers, Companies Turn to In-House Training – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading As the benefits of using memory-safe languages such as Rust become clearer, many organizations are shifting...
North Korea Poses as Meta to Deploy Complex Backdoor at Aerospace Org – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading North Korea’s state-sponsored Lazarus Group appears to have added a complex and still evolving new backdoor...
KillNet Claims DDoS Attack Against Royal Family Website – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The official website of the UK royal family was subject to a distributed denial-of-service (DDoS) attack...
FBI: Crippling ‘Dual Ransomware Attacks’ on the Rise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The FBI has issued a warning about a rising ransomware trend in which separate attacks are conducted just...
Norway Urges Europe-Wide Ban on Meta’s Targeted Ad Data Collection – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A ban on mass Meta user data collection for advertising is set to expire next month in Norway,...
Addressing AI and Security Challenges With Red Teams: A Google Perspective – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 In our digital world, the security landscape is in a constant state of flux. Advances in artificial intelligence (AI) will trigger...
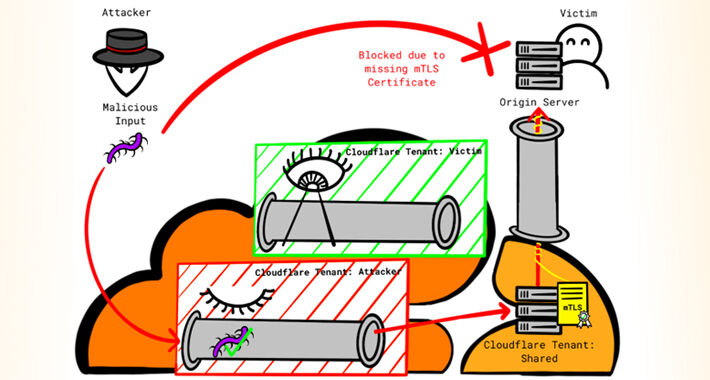
Researcher Reveals New Techniques to Bypass Cloudflare’s Firewall and DDoS Protection – Source:thehackernews.com
Source: thehackernews.com – Author: . Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating...
Arm Issues Patch for Mali GPU Kernel Driver Vulnerability Amidst Ongoing Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 03, 2023THNCyber Attack / Vulnerability Arm has released security patches to contain a security flaw in the Mali GPU Kernel...
EU Lawmaker Questions CSAM Proposal ‘Conflicts of Interest’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Encryption & Key Management , Legislation & Litigation , Security Operations LIBE Committee Chair Seeks Clarifications from EU Home Affairs Minister...
Some Prospect Medical Hospitals in Dire State, Post-Attack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Continued Operation of 3 Connecticut Hospitals Now in Question Marianne Kolbasuk McGee...
Alert: Attackers Actively Exploiting WS_FTP Vulnerabilities – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Attack Surface Management , Critical Infrastructure Security Cybersecurity Officials Recommend Immediate Patching to Fix Serious Flaws...
Chertoff Group Arm to Buy Trustwave from Singtel for $205M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Managed Detection & Response (MDR) , Managed Security Service Provider (MSSP) MSSP, MDR Provider Lost Nearly...
Live Exploitation Underscores Urgency to Patch Critical WS-FTP Server Flaw – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Just days after the release of patches for a critical pre-authentication flaw in Progress Software’s WS_FTP server product, security experts...
European Telecommunications Standards Institute Discloses Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The European Telecommunications Standards Institute (ETSI) has disclosed a data breach following a cyberattack on its member’s portal. Established in...
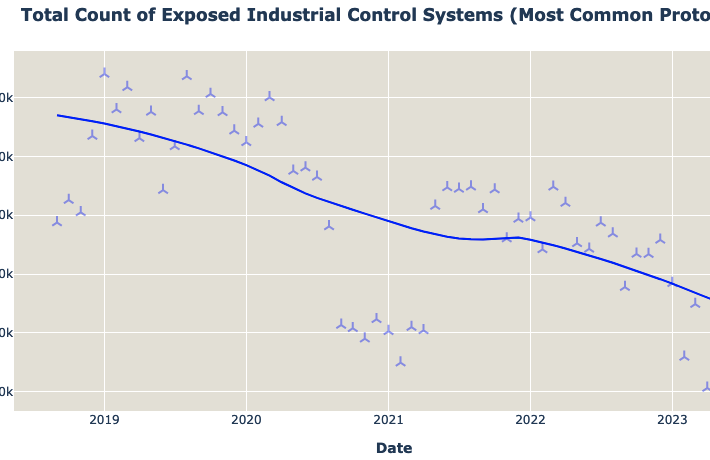
Number of Internet-Exposed ICS Drops Below 100,000: Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The number of internet-exposed industrial control systems (ICS) has continued to decrease over the past years, dropping below 100,000 as...
Johnson Controls Ransomware Attack Could Impact DHS – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Sensitive Department of Homeland Security (DHS) information might have been compromised in a recent ransomware attack aimed at government contractor...
Unpatched Exim Vulnerabilities Expose Many Mail Servers to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The existence of several unpatched vulnerabilities impacting Exim mail transfer agent (MTA) installations was disclosed last week, more than one...
CISA Kicks Off Cybersecurity Awareness Month With New Program – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire To celebrate the 20th Cybersecurity Awareness Month, CISA has launched a new program, meant to promote four critical actions that...
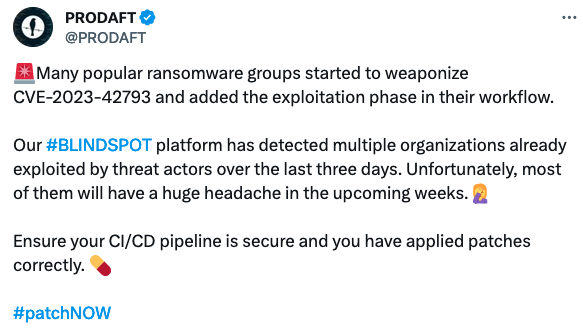
Recently Patched TeamCity Vulnerability Exploited to Hack Servers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs In-the-wild exploitation of a critical vulnerability in JetBrains’ TeamCity continuous integration and continuous deployment (CI/CD) server started just days after...
Microsoft Defender no longer flags Tor Browser as malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Recent versions of the TorBrowser, specifically because of the updated tor.exe file it contained, were being incorrectly flagged as potential...
Exim patches three of six zero-day bugs disclosed last week – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Exim developers have released patches for three of the zero-days disclosed last week through Trend Micro’s Zero Day Initiative (ZDI),...
New BunnyLoader threat emerges as a feature-rich malware-as-a-service – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers discovered a new malware-as-a-service (MaaS) named ‘BunnyLoader’ advertised on multiple hacker forums as a fileless loader that can...
Ransomware gangs now exploiting critical TeamCity RCE flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Ransomware gangs are now targeting a recently patched critical vulnerability in JetBrains’ TeamCity continuous integration and deployment server. The flaw...