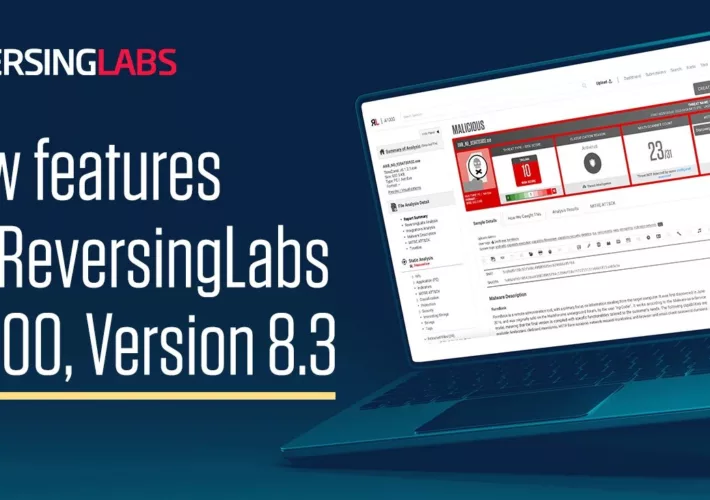
Source: securityboulevard.com – Author: ReversingLabs Our customers rely on ReversingLabs A1000 Threat Analysis and Hunting Solution to provide an instant malware lab, delivering static and dynamic...
Year: 2023
AWS’ MadPot Honeypot Operation Corrals Threat Actors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Engineers with Amazon Web Services more than a decade ago began developing tools to better collect intelligence on the cyberthreats...
Botmasters Unveiled: Exploring the Dual Role of Botnets in Today’s Digital Landscape – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers The duality of the botmaster underscores the versatility of botnets, making them a potent tool that can be leveraged for...
A Day In the Life with Security Solution Architect, Joshua Roback – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelly Dougherty Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
Randall Munroe’s XKCD ‘A Halloween Carol’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Chinese APT Actors Target WeChat Users – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security APT 41 Used Android, iOS Surveillance Malware to Target APAC Victims Since 2018 Jayant Chakravarti (@JayJay_Tech) • October 3,...
Ransomware Actors Exploit Critical Bug, Target DevOps Tool – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 DevSecOps , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Multiple Organizations Victimized Over the Weekend Mihir Bagwe (MihirBagwe)...
Live Webinar | Achieving Air-Gapped Data Security for VMs in Azure – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Panel Discussion | Proactive vs Reactive: Why Using GenAI Needs to be Part of A Proactive Security Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
France Closes in on Digital Safety Bill – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Standards, Regulations & Compliance Lawmakers May Limit VPN Use Akshaya Asokan (asokan_akshaya) • October 3, 2023 The main facade...
NSA Establishes AI Security Center – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The National Security Agency (NSA) has unveiled the AI Security Center, a new entity dedicated to overseeing the development and integration...
FortiGuard Uncovers Deceptive Install Scripts in npm Packages – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A series of malicious packages hidden within the Node Package Manager (npm), the largest software registry for JavaScript, has been uncovered. ...
EU Cyber Resilience Act Could be Exploited for Surveillance, Experts Warn – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The EU’s Cyber Resilience Act (CRA) could be misused by governments for intelligence or surveillance purposes, a group of industry experts...
Predator Spyware Linked to Madagascar’s Government Ahead of Presidential Election – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Madagascar government likely used the Cytrox-developed Predator spyware to conduct political domestic surveillance ahead of the country’s presidential election, according...
Upstream Supply Chain Attacks Triple in a Year – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security experts have warned of surging cyber risk in open source ecosystems, having detected three times more malicious packages in 2023...
Half of Cybersecurity Professionals Report Increase in Cyber-Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over half (52%) of cybersecurity professionals are experiencing an increase in cyber-attacks compared to a year ago, according to new research...
CyberEPQ Course Triples Student Intake for the Coming Year – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Chartered Institute of Information Security (CIISec) has said it hopes to enrol at least 400 students on its CyberEPQ course,...
Fifth of Brits Suspect They’ve Been Monitored by Employers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Nearly one in five (19%) adults polled in a new survey from the UK’s privacy regulator think they’ve been monitored by...
San Francisco’s transport agency Metropolitan Transportation Commission (MTC) exposes drivers’ plate numbers and addresses – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini San Francisco’s transport agency Metropolitan Transportation Commission (MTC) exposes drivers’ plate numbers and addresses A misconfiguration in the Metropolitan Transportation...
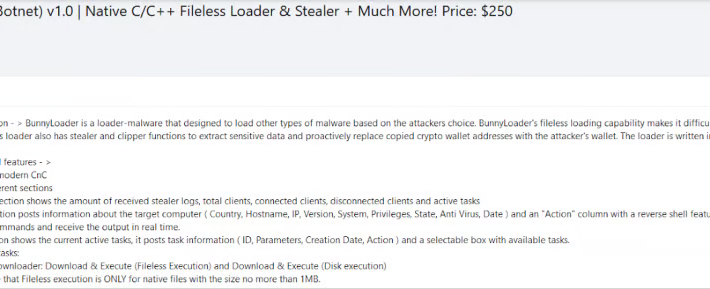
BunnyLoader, a new Malware-as-a-Service advertised in cybercrime forums – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini BunnyLoader, a new Malware-as-a-Service advertised in cybercrime forums Cybersecurity researchers spotted a new malware-as-a-service (MaaS) called BunnyLoader that’s appeared in the threat...
Exclusive: Lighting the Exfiltration Infrastructure of a LockBit Affiliate (and more) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Exclusive: Lighting the Exfiltration Infrastructure of a LockBit Affiliate (and more) Researchers have identified the exfiltration infrastructure of a LockBit...
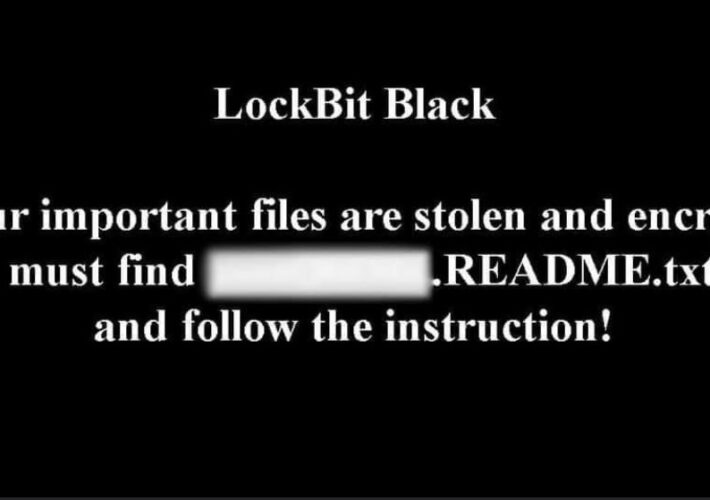
Two hacker groups are back in the news, LockBit 3.0 Black and BlackCat/AlphV – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Two hacker groups are back in the news, LockBit 3.0 Black and BlackCat/AlphV Researchers from cybersecurity firm TG Soft are warning Italian...
European Telecommunications Standards Institute (ETSI) suffered a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini European Telecommunications Standards Institute (ETSI) suffered a data breach The European Telecommunications Standards Institute (ETSI) disclosed a data breach, threat...
Browse Safer and Faster Around the World with JellyVPN — Now Just $34.99 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy on October 3, 2023, 6:02 AM EDT Browse Safer and Faster Around the World with JellyVPN — Now Just $34.99...
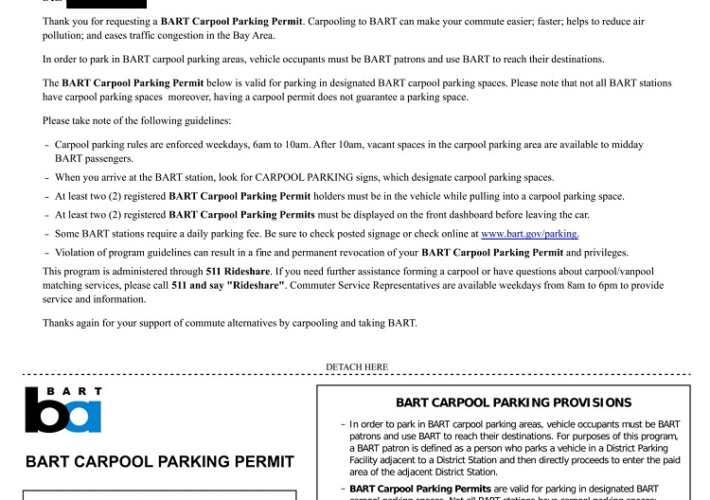
GDPR Data Breach Notification Letter – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: In the current business environment, it is almost inevitable that an organization will experience a security breach that exposes collected personal data...
Security Awareness and Training Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: A security policy is only as valuable as the knowledge and efforts of those who adhere to it, whether IT staff or...
Qualcomm Releases Patch for 3 new Zero-Days Under Active Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 03, 2023THNZero Day / Vulnerability Chipmaker Qualcomm has released security updates to address 17 vulnerabilities in various components, while warning...
Warning: PyTorch Models Vulnerable to Remote Code Execution via ShellTorch – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 03, 2023THNArtificial Intelligence / Cyber Threat Cybersecurity researchers have disclosed multiple critical security flaws in the TorchServe tool for serving...
Over 3 Dozen Data-Stealing Malicious npm Packages Found Targeting Developers – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 03, 2023THNSoftware Security / Hacking Nearly three dozen counterfeit packages have been discovered in the npm package repository that are...
API Security Trends 2023 – Have Organizations Improved their Security Posture? – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 03, 2023The Hacker NewsAPI Security / Data Security APIs, also known as application programming interfaces, serve as the backbone of...