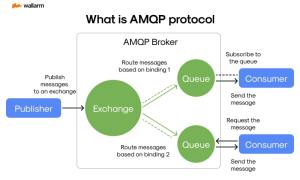
Source: securityboulevard.com – Author: Ivan Novikov The Initial Overview: Learning about MQTT & AMQP In the dynamic arenas of Internet of Things (IoT) and cloud computing,...
Year: 2023
Weekly Blog Wrap-Up (December 25- December 28 , 2023) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tim Walker Welcome to the TuxCare Weekly Blog Wrap-Up – your go-to resource for the latest insights on cybersecurity strategy, Linux security,...
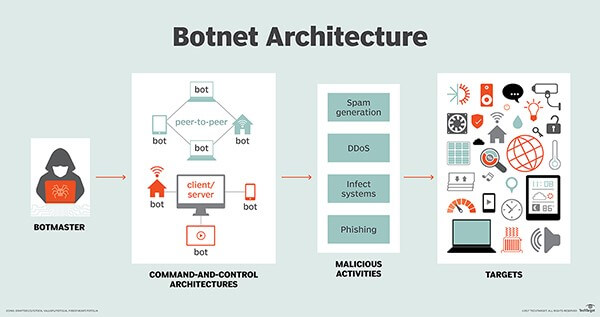
10 Botnet Detection and Removal Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Venkatesh Sundar If your device suddenly behaves like a re-animated zombie, you might be under a Botnet attack. Also known as a...
Indian IT Leaders Identify Security Gap in Data Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra A recent study by Rubrik, a US-based data security firm, has bare concerning reality within the Indian IT sector: an...
Info-Stealing Malware Now Includes Google Session Hijacking – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Access Management , Cybercrime , Cybercrime as-a-service Google OAuth2 Vulnerability Being Actively Abused by Attackers, Researchers Warn Chris Riotta (@chrisriotta) •...
How One University Is Beefing Up Cyber Defenses, Programs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Cybercrime Steve Zuromski, CIO at Bridgewater State University, on New...
Russian Military Intelligence Blamed for Blitzkrieg Hacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Ukrainian Cyber Defenders Trace Government Agency Hits to Phishing Campaign Mihir Bagwe...
OpenAI and Microsoft Face New York Times Copyright Lawsuit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Legislation & Litigation , Standards, Regulations & Compliance Media Giant Alleges ‘Billions of Dollars in Statutory and Actual Damages’ Rashmi Ramesh...
Microsoft Disables Abused Application Installation Protocol – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Attackers Have Been Exploiting App Installer to Evade Malware Defenses in Windows Mihir Bagwe...
Happy 14th Birthday, KrebsOnSecurity! – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs KrebsOnSecurity celebrates its 14th year of existence today! I promised myself this post wouldn’t devolve into yet another Cybersecurity Year in...
Albanian Parliament and One Albania Telecom Hit by Cyber Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomCyber Attack / Web Security The Assembly of the Republic of Albania and telecom company One Albania have been...
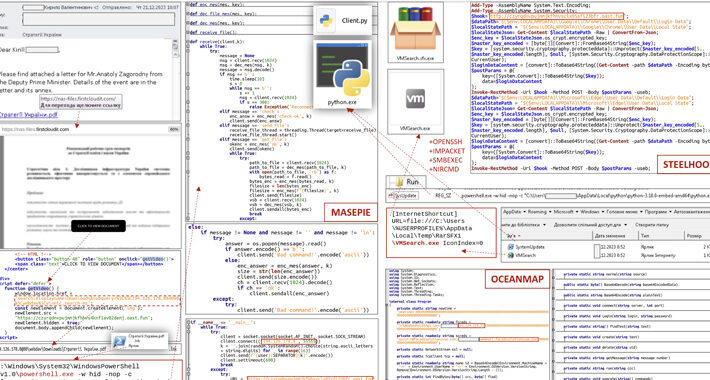
CERT-UA Uncovers New Malware Wave Distributing OCEANMAP, MASEPIE, STEELHOOK – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomEmail Security / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign...
Develop Valuable Security and Risk Management Skills for Just $30 Through 1/1 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Good things are coming your way! In order for us to complete site maintenance, TechRepublic is read-only from December 22...
AI Is Scarily Good at Guessing the Location of Random Photos – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Wow: To test PIGEON’s performance, I gave it five personal photos from a trip I took across America years ago,...
Friday Squid Blogging: Sqids – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier They’re short unique strings: Sqids (pronounced “squids”) is an open-source library that lets you generate YouTube-looking IDs from numbers. These...
Supply chain trends, critical infrastructure & cyber security in 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In 2024, supply chain security must become a top priority. Public agencies and industry experts agree that the supply...
Mastering the dynamic SaaS ecosystem and staying ahead in 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau I’m the co-founder and CTO of Atmosec, which is now under the Check Point umbrella. I’m driven by helping companies confidently...
Clash of Clans gamers at risk while using third-party app – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Clash of Clans gamers at risk while using third-party app Pierluigi Paganini December 29, 2023 An exposed database and secrets...
New Version of Meduza Stealer Released in Dark Web – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini New Version of Meduza Stealer Released in Dark Web Pierluigi Paganini December 29, 2023 The Resecurity’s HUNTER unit spotted a...
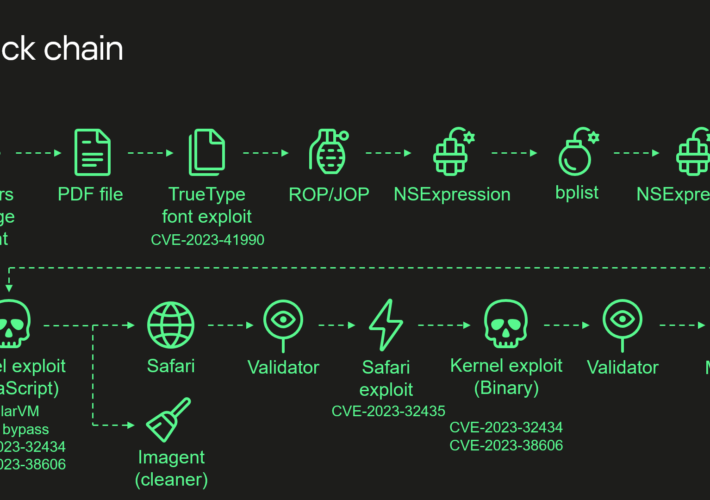
Operation Triangulation attacks relied on an undocumented hardware feature – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Operation Triangulation attacks relied on an undocumented hardware feature Pierluigi Paganini December 28, 2023 Experts discovered that Operation Triangulation targeting Apple...
Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data Pierluigi Paganini December...
Lockbit ransomware attack interrupted medical emergencies gang at a German hospital network – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Lockbit ransomware attack interrupted medical emergencies gang at a German hospital network Pierluigi Paganini December 28, 2023 A Lockbit ransomware...
Critical Apache OFBiz Vulnerability in Attacker Crosshairs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Shadowserver sees possible in-the-wild exploitation of a critical Apache OFBiz vulnerability tracked as CVE-2023-49070. The post Critical Apache OFBiz Vulnerability...
Europe’s Largest Parking App Provider Informs Customers of Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs EasyPark says hackers stole European customer information, including partial IBAN or payment card numbers. The post Europe’s Largest Parking App...
Operations, Trading of Eagers Automotive Disrupted by Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Eagers Automotive, a vehicle dealer in Australia and New Zealand, has halted trading after being targeted in a cyberattack. The...
Cyberattack Targets Albanian Parliament’s Data System, Halting Its Work – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Albania’s Parliament said it had suffered a cyberattack with hackers trying to get into its data system, resulting in a...
Palo Alto Networks Completes Acquisition of Talon – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Palo Alto Networks completed the acquisition of Talon Cyber Security, an Israeli startup selling a secure browser technology to enterprise...
The Emerging Landscape of AI-Driven Cybersecurity Threats: A Look Ahead – Source: www.securityweek.com
Source: www.securityweek.com – Author: Rik Ferguson While AI can significantly bolster defense mechanisms, it also equips adversaries with powerful tools to launch sophisticated cyberattacks. The post...
LoanCare Notifying 1.3 Million of Data Breach Following Cyberattack on Parent Company – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire LoanCare is informing 1.3 million individuals that their personal information was compromised in a data breach. The post LoanCare Notifying...
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomMalware / Cyber Threat Nation-state actors affiliated to North Korea have been observed using spear-phishing attacks to deliver an...