The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Month: December 2023
Critical Infrastructure Annual Risk Review
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CREDENTIAL DUMPING CHEATSHEET
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Countering Ransomware Financing
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CompTIA Security + Exam Study Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Daily Malicious Files Soar 3% in 2023, Kaspersky Finds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybercriminals unleashed an average of 411,000 malicious files every day in 2023, representing a 3% increase from the previous year, according...
Carbanak Banking Malware Resurfaces with New Ransomware Tactics – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 26, 2023NewsroomMalware / Cybercrime The banking malware known as Carbanak has been observed being used in ransomware attacks with updated...
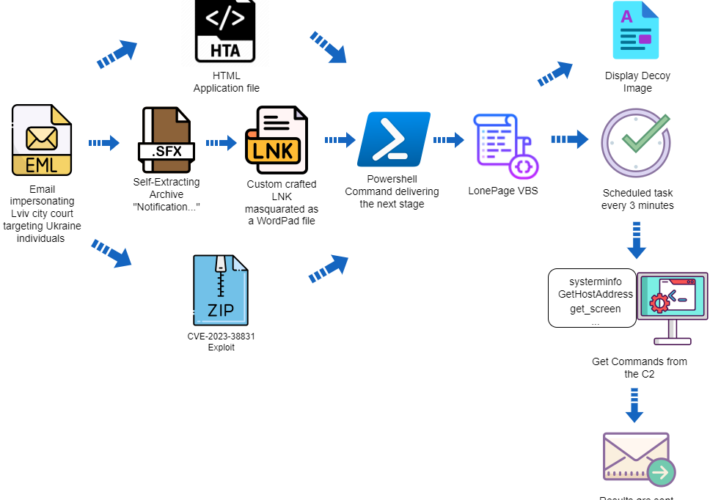
APT group UAC-0099 targets Ukraine exploiting a WinRAR flaw – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini APT group UAC-0099 targets Ukraine exploiting a WinRAR flaw Pierluigi Paganini December 25, 2023 The threat actor UAC-0099 is exploiting a...
Iran-linked APT33 targets Defense Industrial Base sector with FalseFont backdoor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Iran-linked APT33 targets Defense Industrial Base sector with FalseFont backdoor Pierluigi Paganini December 25, 2023 Microsoft reports that the Iran-linked APT33...
GTA 5 source code reportedly leaked online a year after RockStar hack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The source code for Grand Theft Auto 5 was reportedly leaked on Christmas Eve, a little over a year after the...
Google Chrome now scans for compromised passwords in the background – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google says the Chrome Safety Check feature will work in the background to check if passwords saved in the web...
Medical Emergency Assistance – Thank You – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist I have been an active volunteer as part of corporate medical response teams for more than 20 years of my...
Why Use a VLAN? Unveiling the Benefits of Virtual LANs in Network Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Understanding the Basic Concept of VLANs Virtual Local Area Networks, or VLANs, serve as a critical computing technology designed for...
Why a Zero Trust Security Policy Matters and Steps to Implementation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michelle Ofir Geveye Understanding Zero Trust Traditionally, cybersecurity operated on a simple principle: trust what’s inside, be wary of what’s outside. This...
Yahoo “Strongly” Recommends DMARC RUA Tag for Bulk Senders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra Developers at Yahoo have been busy formulating guidelines for bulk senders and the DMARC RUA tag has been mentioned as...
Ubuntu Security Updates Fixed Vim Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina Vim, a powerful and widely used text editor, has recently come under scrutiny due to several vulnerabilities that could potentially...
The Intersection of IoT and Financial Security: Expert Tips for Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: TuxCare Team Sophisticated Internet of Things (IoT) technologies transformed the cybersecurity systems in financial services. They’re continuously evolving and improving. Take credit...
Merry Little Christmas – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
GambleForce Attacks: APAC Firms Targeted With SQL Injections – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja In light of recent GambleForce attacks, a new threat actor has emerged, targeting more than 20 organizations across the Asia-Pacific...
The Year in Review and 2024 Predictions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Eston In our last episode of the year, we replay our predictions for 2023 reviewing what we got right and what...
Learn Cybersecurity Skills From Scratch for Just $30 Through January 1 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Good things are coming your way! In order for us to complete site maintenance, TechRepublic is read-only from December 22...
Domain Name Security Challenges – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Protecting domain name systems finally has the attention of cybersecurity professionals -because every recent large data breach has involved a DNS...
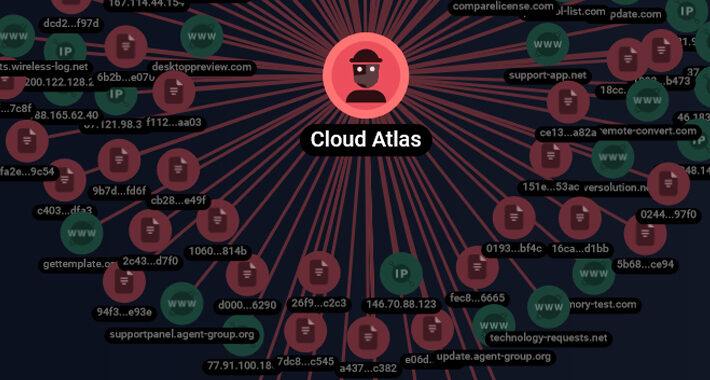
Cloud Atlas’ Spear-Phishing Attacks Target Russian Agro and Research Companies – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 25, 2023NewsroomCyber Espionage / Malware The threat actor referred to as Cloud Atlas has been linked to a set of...
Security Affairs newsletter Round 451 by Pierluigi Paganini – INTERNATIONAL EDITION – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Security Affairs newsletter Round 451 by Pierluigi Paganini – INTERNATIONAL EDITION | Europol and ENISA spotted 443 e-stores compromised with...
Europol and ENISA spotted 443 e-stores compromised with digital skimming – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Europol and ENISA spotted 443 e-stores compromised with digital skimming Pierluigi Paganini December 24, 2023 A joint law enforcement operation...
Video game giant Ubisoft investigates reports of a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Video game giant Ubisoft investigates reports of a data breach Pierluigi Paganini December 24, 2023 Video game publisher Ubisoft is...
Weekly Update 379 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt It’s that time of the year again, time to head from the heat to the cold as we jump on...
USENIX Security ’23 – ‘Sneaky Spy Devices And Defective Detectors: The Ecosystem Of Intimate Partner Surveillance With Covert Devices’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Full Presenters List: Rose Ceccio, Sophie Stephenson, Varun Chadha, Danny Yuxing Huang, Rahul Chatterjee Many thanks to USENIX for publishing...
Democracy 2024: Pro-Hunger ≠ “Pro-Life” – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr Ref AP News: https://apnews.com/article/iowa-summer-ebt-food-assistance-0e878c5c0fc9dd0dd55622cb22a82561. Iowa has decided not to participate in the 2024 Summer Electronic Benefits Transfer for Children (Summer EBT)...
British LAPSUS$ Teen Members Sentenced for High-Profile Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 24, 2023NewsroomCyber Crime / Data Breach Two British teens part of the LAPSUS$ cyber crime and extortion gang have been...