Source: krebsonsecurity.com – Author: BrianKrebs KrebsOnSecurity celebrates its 14th year of existence today! I promised myself this post wouldn’t devolve into yet another Cybersecurity Year in...
Day: December 29, 2023
Albanian Parliament and One Albania Telecom Hit by Cyber Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomCyber Attack / Web Security The Assembly of the Republic of Albania and telecom company One Albania have been...
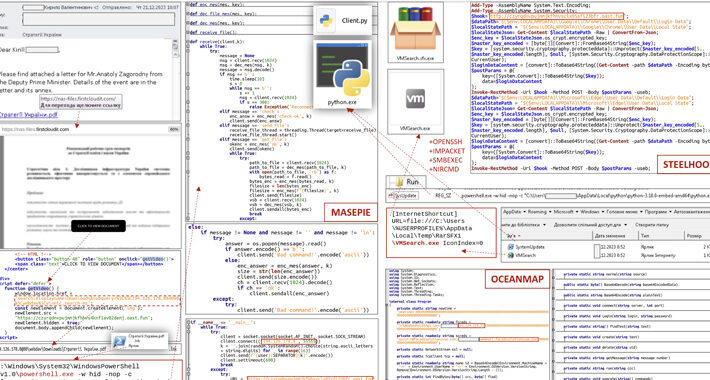
CERT-UA Uncovers New Malware Wave Distributing OCEANMAP, MASEPIE, STEELHOOK – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomEmail Security / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign...
Develop Valuable Security and Risk Management Skills for Just $30 Through 1/1 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Good things are coming your way! In order for us to complete site maintenance, TechRepublic is read-only from December 22...
AI Is Scarily Good at Guessing the Location of Random Photos – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Wow: To test PIGEON’s performance, I gave it five personal photos from a trip I took across America years ago,...
Friday Squid Blogging: Sqids – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier They’re short unique strings: Sqids (pronounced “squids”) is an open-source library that lets you generate YouTube-looking IDs from numbers. These...
Supply chain trends, critical infrastructure & cyber security in 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In 2024, supply chain security must become a top priority. Public agencies and industry experts agree that the supply...
Mastering the dynamic SaaS ecosystem and staying ahead in 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau I’m the co-founder and CTO of Atmosec, which is now under the Check Point umbrella. I’m driven by helping companies confidently...
Clash of Clans gamers at risk while using third-party app – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Clash of Clans gamers at risk while using third-party app Pierluigi Paganini December 29, 2023 An exposed database and secrets...
New Version of Meduza Stealer Released in Dark Web – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini New Version of Meduza Stealer Released in Dark Web Pierluigi Paganini December 29, 2023 The Resecurity’s HUNTER unit spotted a...
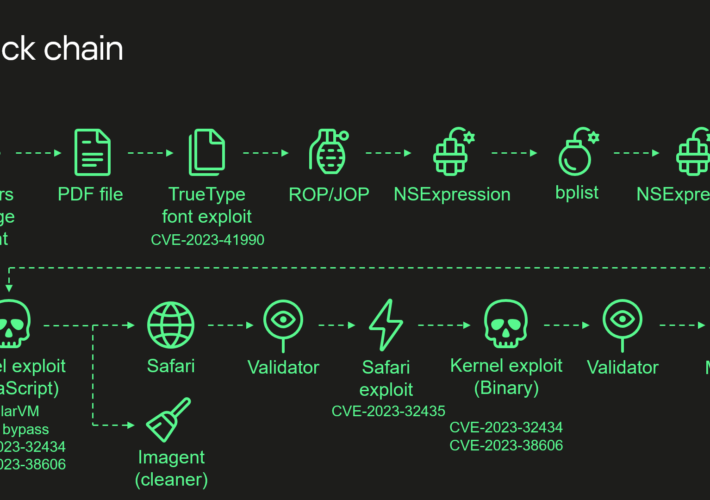
Operation Triangulation attacks relied on an undocumented hardware feature – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Operation Triangulation attacks relied on an undocumented hardware feature Pierluigi Paganini December 28, 2023 Experts discovered that Operation Triangulation targeting Apple...
Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data Pierluigi Paganini December...
Lockbit ransomware attack interrupted medical emergencies gang at a German hospital network – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Lockbit ransomware attack interrupted medical emergencies gang at a German hospital network Pierluigi Paganini December 28, 2023 A Lockbit ransomware...
Critical Apache OFBiz Vulnerability in Attacker Crosshairs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Shadowserver sees possible in-the-wild exploitation of a critical Apache OFBiz vulnerability tracked as CVE-2023-49070. The post Critical Apache OFBiz Vulnerability...
Europe’s Largest Parking App Provider Informs Customers of Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs EasyPark says hackers stole European customer information, including partial IBAN or payment card numbers. The post Europe’s Largest Parking App...
Operations, Trading of Eagers Automotive Disrupted by Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Eagers Automotive, a vehicle dealer in Australia and New Zealand, has halted trading after being targeted in a cyberattack. The...
Cyberattack Targets Albanian Parliament’s Data System, Halting Its Work – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Albania’s Parliament said it had suffered a cyberattack with hackers trying to get into its data system, resulting in a...
Palo Alto Networks Completes Acquisition of Talon – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Palo Alto Networks completed the acquisition of Talon Cyber Security, an Israeli startup selling a secure browser technology to enterprise...
The Emerging Landscape of AI-Driven Cybersecurity Threats: A Look Ahead – Source: www.securityweek.com
Source: www.securityweek.com – Author: Rik Ferguson While AI can significantly bolster defense mechanisms, it also equips adversaries with powerful tools to launch sophisticated cyberattacks. The post...
LoanCare Notifying 1.3 Million of Data Breach Following Cyberattack on Parent Company – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire LoanCare is informing 1.3 million individuals that their personal information was compromised in a data breach. The post LoanCare Notifying...
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomMalware / Cyber Threat Nation-state actors affiliated to North Korea have been observed using spear-phishing attacks to deliver an...
Microsoft Disables MSIX App Installer Protocol Widely Used in Malware Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 29, 2023NewsroomMalware / Endpoint Security Microsoft on Thursday said it’s once again disabling the ms-appinstaller protocol handler by default following...
Game mod on Steam breached to push password-stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Downfall, a fan expansion for the popular Slay the Spire indie strategy game, was breached on Christmas Day to push...
Eagers Automotive halts trading in response to cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Eagers Automotive has announced it suffered a cyberattack and was forced to halt trading on the stock exchange as it...
EasyPark discloses data breach that may impact millions of users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Parking app developer EasyPark has published a notice on its website warning of a data breach it discovered on December...
Microsoft disables MSIX protocol handler abused in malware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has again disabled the MSIX ms-appinstaller protocol handler after multiple financially motivated threat groups abused it to infect Windows...
Kroll reveals FTX customer info exposed in August data breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Risk and financial advisory company Kroll has released additional details regarding the August data breach, which exposed the personal information...
Russian military hackers target Ukraine with new MASEPIE malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Ukraine’s Computer Emergency Response Team (CERT) is warning of a new phishing campaign that allowed Russia-linked hackers to deploy previously...
Apache OFBiz RCE flaw exploited to find vulnerable Confluence servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A critical Apache OFBiz pre-authentication remote code execution vulnerability is being actively exploited using public proof of concept (PoC) exploits. Apache...
USENIX Security ’23 – Xiaojun Xu, Qingying Hao, Zhuolin Yang, Bo Li, David Liebovitz, Gang Wang, Carl A. Gunter ‘How to Cover up Anomalous Accesses to Electronic Health Records’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Cloud Security, Governance and Skills in 2024 Step 1 of 6 16% Who in your organization is responsible for cloud...