Source: thehackernews.com – Author: . Dec 20, 2023NewsroomFinancial Crime / Cyber Threat A six-month-long international police operation codenamed HAECHI-IV has resulted in the arrests of nearly...
Day: December 20, 2023
New Go-Based JaskaGO Malware Targeting Windows and macOS Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 20, 2023NewsroomCryptocurrency / Malware A new Go-based information stealer malware called JaskaGO has emerged as the latest cross-platform threat to...
Sharing stories on the CyberTuesday podcast – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Episode 21 | Cyber Stories with Graham Cluley Thanks to Simon Whittaker, and the rest of the team at Vertical...
The ultimate guide to the CISSP certification – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The ultimate guide to the CISSP includes everything that you need to know about this premiere cyber security leadership...
Comcast’s Xfinity customer data exposed after CitrixBleed attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Comcast’s Xfinity customer data exposed after CitrixBleed attack Pierluigi Paganini December 19, 2023 Comcast’s Xfinity discloses a data breach after...
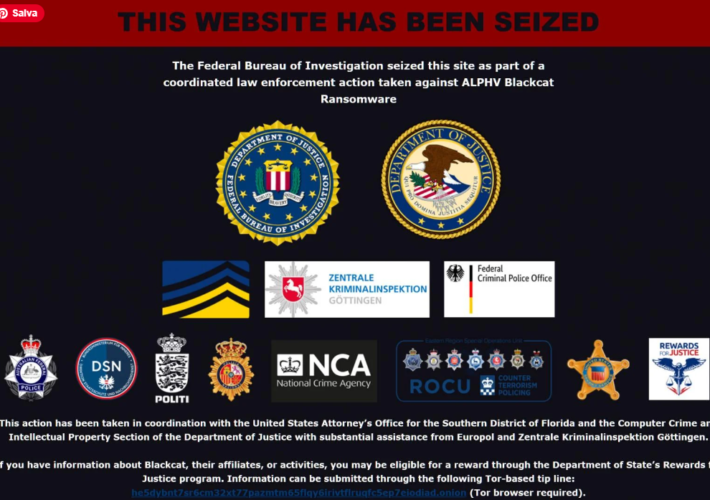
FBI claims to have dismantled AlphV/Blackcat ransomware operation, but the group denies it – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini December 19, 2023 The FBI seized the Tor leak site of the AlphV/Blackcat ransomware group and replaced the...
Smishing Triad: Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Smishing Triad: Cybercriminals Impersonate UAE Federal Authority for Identity and Citizenship on the Peak of Holidays Season Pierluigi Paganini December...
Insight – The Evolving Cybersecurity Landscape in 2024: Predictions and Preparations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Corey Sinclair As we prepare to ring in the new year, the ever-evolving cybersecurity landscape promises to bring new cyber threat actors,...
Cisco Details AI Strategy for Simplifying Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Cisco is moving to pervasively apply artificial intelligence (AI) in a way that should lower the bar in terms of...
DEF CON 31 – Secretary of US Homeland Security Alejandro Mayorkas – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/12/def-con-31-secretary-of-us-homeland-security-alejandro-mayorkas/ Category & Tags: Security Bloggers Network,Cybersecurity,DEF Con...
Play Ransomware Has Hit 300 Entities Worldwide: FBI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The Play ransomware group, which was behind such high-profile attacks as those on the city of Oakland, California, and Dallas...
Securing Against OAuth Exploitation: A Step-By-Step Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Farah Iyer Recent findings from Microsoft Threat Intelligence reveal a concerning trend: threat actors exploiting vulnerabilities in Microsoft 365 and Azure environments...
Explore PCI DSS 4.0: The future of cardholder data security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Aguiar For those in charge of industry standards, ensuring rules are up to date and fit for purpose is a constant...
TrustCloud Product Updates: 2023 Greatest Hits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tejas Ranade TrustCloud’s “Greatest Hits” of 2023 As we bid farewell to 2023, let’s take a stroll down memory lane and groove...
Randall Munroe’s XKCD ‘Puzzles’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/12/randall-munroes-xkcd-puzzles/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
File Integrity Monitoring for PCI Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lauren Yacono The PCI-DSS (Payment Card Industry Data Security Standard) is a set of industry-recommended requirements for business organizations that store, process,...
CMMC Enclaves: What they are. How they help compliance. – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Noël Vestal, PMP, CMMC RP As CMMC Final Rule approaches, one of the most common concerns defense contractors...
BlackCat Ransomware ‘Unseizing’ a Dark Web Stunt – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Ransomware Group Declares Nothing Off Limits Outside of CIS Countries David Perera (@daveperera) • December...
Report Says CISA is Failing to Identify High-Risk Exploits – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Security Operations CISA Failed to Include High-Risk Vulnerabilities in Known Exploit List, Report Says Chris Riotta (@chrisriotta) • December 19, 2023...
Webinar | Securing Skies: Network Firewalls and the Battle Against Zero-Day Threats in the Cloud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Iowa Medical Center Latest Victim of Transcription Firm Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Incident & Breach Response , Industry Specific Lawsuits Keep Stacking Up Against Perry Johnson and Associates Marianne Kolbasuk McGee...
OpenAI Formulates Framework to Mitigate ‘Catastrophic Risks’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development A Preparedness Team Will Warn of Current, Future Dangers in...