Source: thehackernews.com – Author: . Dec 20, 2023NewsroomNetwork Security / Data Breach Ransomware groups are increasingly switching to remote encryption in their attacks, marking a new...
Day: December 20, 2023
Comcast Ties Breach Affecting 36M Customers to Citrix Bleed – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Governance & Risk Management , Patch Management Attackers Apparently Stole Authenticated Sessions to Hit Telecommunications Giant Mathew J....
BlackCat Ransomware ‘Unseizing’ a Dark Web Stunt – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware Ransomware Group Declares Nothing Off Limits Outside of CIS Countries David Perera (@daveperera) • December...
OpenAI Formulates Framework to Mitigate ‘Catastrophic Risks’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development A Preparedness Team Will Warn of Current, Future Dangers in...
Report Says CISA Is Failing to Identify High-Risk Exploits – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Security Operations CISA Did Not Include Critical Vulnerabilities in Known Exploit List, Report Says Chris Riotta (@chrisriotta) • December 19, 2023...
Okta to Acquire Israeli Startup Spera Security – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Okta agreed to acquire Spera Security in a move broaden Okta’s Identity threat detection and security posture management capabilities. The...
Mozilla Patches Firefox Vulnerability Allowing Remote Code Execution, Sandbox Escape – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Firefox and Thunderbird security updates released this week address multiple memory safety bugs in both products. The post Mozilla Patches...
NSA Blocked 10 Billion Connections to Malicious and Suspicious Domains – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The National Security Agency has published a new yearly report detailing its cybersecurity efforts throughout 2023. The post NSA Blocked...
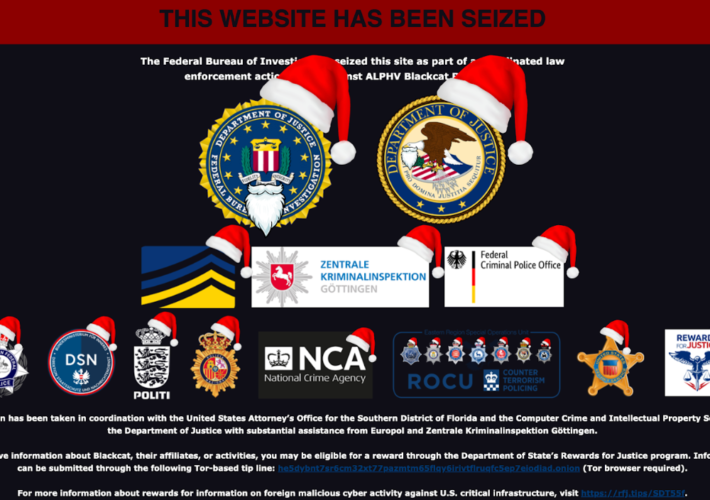
BlackCat Strikes Back: Ransomware Gang “Unseizes” Website, Vows No Limits on Targets – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The BlackCat/Alphv ransomware group is dealing with the government operation that resulted in website seizures and a decryption tool. The...
Xfinity Data Breach Impacts 36 Million Individuals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The recently disclosed Xfinity data breach, which involved exploitation of the CitrixBleed vulnerability, impacts 36 million individuals The post Xfinity...
3,500 Arrested, $300 Million Seized in International Crackdown on Online Fraud – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Authorities in 34 countries have cooperated to dismantle cyber-enabled scams as part of a six-month operation. The post 3,500 Arrested,...
Microsoft fixes Wi-Fi issues triggered by recent Windows updates – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has fixed a known issue causing Wi-Fi network connectivity problems on Windows 11 systems triggered by recently released cumulative...
Healthcare software provider data breach impacts 2.7 million – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas ESO Solutions, a provider of software products for healthcare organizations and fire departments, disclosed that data belonging to 2.7 million...
The password attacks of 2023: Lessons learned and next steps – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software It should take more than eight characters to bring a business to a halt. However, the relentless onslaught...
German police takes down Kingdom Market cybercrime marketplace – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Federal Criminal Police Office in Germany (BKA) and the internet-crime combating unit of Frankfurt (ZIT) have announced the seizure...
BlackCat Ransomware Raises Ante After FBI Disruption – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. Federal Bureau of Investigation (FBI) disclosed today that it infiltrated the world’s second most prolific ransomware gang, a Russia-based...
GCHQ Christmas Codebreaking Challenge – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
What Australia’s Digital ID Means to How Citizens Interact With Businesses Online – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matthew Sainsbury Australia is about to get a national online ID system — the Digital ID — which promises to improve the...
12 Essential Steps Mac Users Need To Take At Year End – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Erik Eckel Business users often experience a year-end slowdown that presents a timely opportunity to catch up on a few overdue tasks....
Feds Snarl ALPHV/BlackCat Ransomware Operation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Source: Imagebroker via Alamy Stock Photo After nearly two weeks of speculation, the US Department of Justice...
Fresh Qakbot Sightings Confirm Recent Takedown Was a Temporary Setback – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Irina Anosova via Shutterstock Qakbot malware is back less than four months after US and international law...
SANS Institute Research Shows What Frameworks, Benchmarks, and Techniques Organizations Use on their Path to Security Maturity – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Respondents overwhelmingly prefer the NIST CSF framework Results show that companies lag in training and cyber-readiness exercises Herndon, Va., December...
Comcast Xfinity Breached via CitrixBleed; 35M Customers Affected – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Sunrise Photos via Alamy Stock Photo The now-infamous CitrixBleed vulnerability has claimed possibly its biggest kill yet:...
Console & Associates, P.C.: Comcast Xfinity Reports Data Breach Exposing Confidential Information of 35M Customers – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MARLTON, N.J., Dec. 19, 2023 /PRNewswire/ –– Approximately 35 million consumers are being notified that their confidential information was compromised due to a...
Salvador Technologies Raises $6M to Empower Cyber Resilience in Operational Technologies and Critical Infrastructures – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE REHOVOT, Israel Salvador has built its market-leading cyber-attack recovery platform with its patented security failover technology to prevent downtime damage and ensure...
Microsoft Outlook Zero-Click Security Flaws Triggered by Sound File – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer 3 Min Read Source: monticello via Shutterstock Researchers this week disclosed details on two security vulnerabilities in Microsoft...
Microsoft: Multiple Perforce Server Flaws Allow for Network Takeover – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Igor Stevanovic via Alamy Stock Photo Microsoft has identified four vulnerabilities in the Perforce source-code management platform,...
Why I Chose Google Bard to Help Write Security Policies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alex Haynes Source: James Brown via Alamy Stock Photo COMMENTARY Ever since large language models (LLMs) like ChatGPT burst onto the scene...
Product Explained: Memcyco’s Real-Time Defense Against Website Spoofing – Source:thehackernews.com
Source: thehackernews.com – Author: . Hands-On Review: Memcyco’s Threat Intelligence Solution Website impersonation, also known as brandjacking or website spoofing, has emerged as a significant threat...
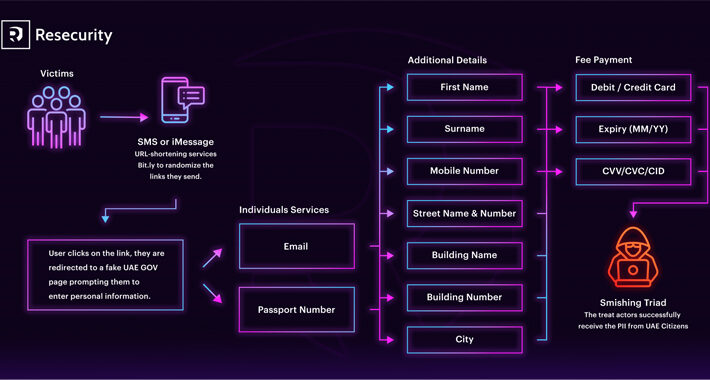
Alert: Chinese-Speaking Hackers Pose as UAE Authority in Latest Smishing Wave – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 20, 2023NewsroomIdentity Theft / SMS Phishing The Chinese-speaking threat actors behind Smishing Triad have been observed masquerading as the United...