Source: thehackernews.com – Author: . Dec 18, 2023NewsroomMalware / Cybersecurity A new wave of phishing messages distributing the QakBot malware has been observed, more than three...
Day: December 18, 2023
CISA Urges Manufacturers Eliminate Default Passwords to Thwart Cyber Threats – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 18, 2023NewsroomSoftware Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging manufacturers to get rid of...
WordPress hosting service Kinsta targeted by Google phishing ads – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar WordPress hosting provider Kinsta is warning customers that Google ads have been observed promoting phishing sites to steal hosting credentials....
Rhadamanthys Stealer malware evolves with more powerful features – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The developers of the Rhadamanthys information-stealing malware have recently released two major versions to add improvements and enhancements across the...
What to do when receiving unprompted MFA OTP codes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Receiving an unprompted one-time passcode (OTP) sent as an email or text should be a cause for concern as it...
Qbot malware returns in campaign targeting hospitality industry – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The QakBot malware is once again being distributed in phishing campaigns after the botnet was disrupted by law enforcement over...
Radar El magazine de ciberseguridad
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ULTIMATE RACI MATRIX
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Horizons
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Privacy technology: What’s next?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Privacy Intro and Implementation Toolkits (GDPR and ISO 27701)
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Powershell Tips & Tricks for r/b/p teamers
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Position-independent code
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CHEATSHEET PORT FORWARD & TUNNELLING
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Planning Considerations for Cyber Incidents
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Pipeline Security Guidelines
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Phishing Email Analysis
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Howto Improve Your Personal Cybersecurity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Personnel Security Maturity Model
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Securing the code: navigating code and GitHub secrets scanning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Itzik Alvas. Co-founder & CEO, Entro Welcome to the high-stakes world of GitHub, where your code isn’t just a collection of functions...
DEF CON 31 – Ceri Coburn’s ‘A Broken Marriage Abusing Mixed Vendor Kerberos Stacks’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/12/def-con-31-ceri-coburns-a-broken-marriage-abusing-mixed-vendor-kerberos-stacks/ Category & Tags: Security Bloggers Network,Cybersecurity,cybersecurity education,DEF...
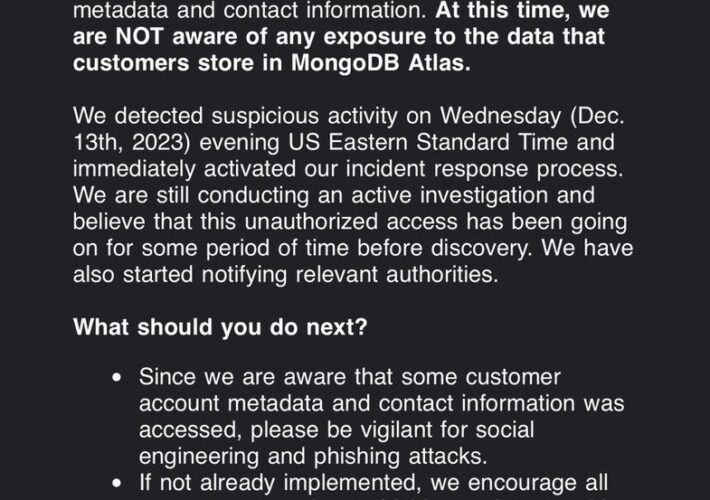
MongoDB investigates a cyberattack, customer data exposed – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini MongoDB investigates a cyberattack, customer data exposed Pierluigi Paganini December 17, 2023 MongoDB on Saturday announced it is investigating a...
InfectedSlurs botnet targets QNAP VioStor NVR vulnerability – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini InfectedSlurs botnet targets QNAP VioStor NVR vulnerability Pierluigi Paganini December 17, 2023 The Mirai-based botnet InfectedSlurs was spotted targeting QNAP...
Security Affairs newsletter Round 450 by Pierluigi Paganini – INTERNATIONAL EDITION – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini MongoDB investigates a cyberattack, customer data exposed | InfectedSlurs botnet targets QNAP VioStor NVR vulnerability | Security Affairs newsletter Round...