Source: www.infosecurity-magazine.com – Author: 1 Amazon Web Services (AWS) said it will require multi-factor authentication (MFA) for all privileged accounts starting mid-2024, in a bid to...
Day: October 7, 2023
Qakbot Gang Still Active Despite FBI Takedown – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Despite the takedown of the Qakbot threat gang’s infrastructure by the FBI in late August, some of the group’s affiliates are...
CISA and NSA Publish Top 10 Misconfigurations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two leading US government security agencies have shared the top 10 most common cybersecurity misconfigurations, in a bid to improve baseline...
Apple Issues Emergency Patches for More Zero-Day Bugs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Apple has been forced to issue more emergency updates to fix two new zero-day vulnerabilities impacting iOS and iPadOS users. An...
SaaS Security in Healthcare: What You Need to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emile Antone The migration to SaaS has resulted in the distribution of valuable data across a number of highly decentralized cloud applications....
Why Risk-Based Authentication Is Essential to a Zero Trust Strategy – Source: securityboulevard.com
Source: securityboulevard.com – Author: HYPR Team Today’s evolving and expanding threat landscape has rendered traditional security measures inadequate for safeguarding sensitive data and systems. Organizations grapple...
DEF CON 31 – nyxgeek’s ‘Track The Planet! Mapping IDs, Monitoring Presence In The Azure Ecosystem’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Google, Yahoo to Put Tighter Spam Restrictions on Bulk Senders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Email giants Google and Yahoo are putting tighter requirements on bulk email senders in hopes of reducing the massive amounts...
ProtectAI Adds Three Tools to Secure AI Models – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Protect AI this week added three open source tools to detect threats to artificial intelligence (AI) models that are aimed...
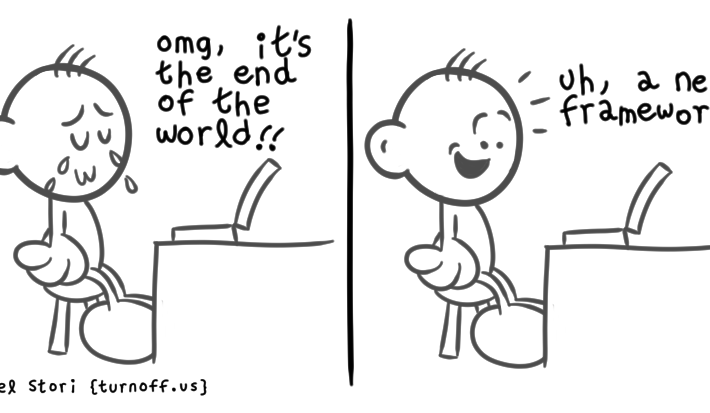
Daniel Stori’s ‘End Of The World’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/10/daniel-storis-end-of-the-world-2/ Category & Tags: Humor,Security Bloggers Network,Daniel Stori,Sarcasm,satire,turnoff.us...
BTS #14 – Protecting The Federal Supply Chain – John Loucaides – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Why Automotive Companies Must Prioritize Secrets Detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Soujanya Ain Today’s cars have come a long way from pure machines run by gears and engines. They’ve evolved into a platform...
iPhone/iPad Warning: Update Now to Avoid Zero-Day Pain – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings iOS 17.0.3 fixes yet more nasty zero-days (and the overheating bug). Apple has updated iOS 17 again, patching two zero-day...
DEF CON 31 – Dan Borgogno’s, Ileana Barrionuevo’s ‘Turning My Virtual Wallet Into A Skimming Device’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
User Protection: Removing the Security Burden From Users – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Eric Eddy, principal technical marketing engineer at Cisco, discusses critical aspects of user-centric security. From alleviating the security burden on users...
ISACA Security Survey 2023: Technical Skills Gaps, Budgeting – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Professional Certifications & Continuous Training , Training & Security Leadership , Video ISACA’s Jon Brandt Discusses Threat Trends, Hiring Challenges, New...
Executive Insights into Manufacturing Cybersecurity with Rockwell Automation and Dragos – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Robert Lee CEO and Co-Founder, Dragos Robert is a recognized authority in the industrial cybersecurity community. He is CEO and co-founder...
ISMG Editors: Can Governments Get a Handle on AI? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Also: EU Policy Updates and...
China-Linked APT Uses New Backdoor for Espionage in Guyana – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Attackers Use Previously Undocumented Backdoor as Well as Traditional Hacking Tools Mihir...
Revealed! The top 10 cybersecurity misconfigurations, as determined by CISA and the NSA – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley A joint cybersecurity advisory from the United States’s National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) has...
Lyca Mobile Affected by Cyberattack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Lyca Mobile has released a statement about an unexpected disruption on its network caused by a cyberattack that may have...
PoC Exploits Released for Major Linux Flaw – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu On the majority of Linux distributions, proof-of-concept attacks for a high-severity vulnerability in the dynamic loader of the GNU C...
Access-as-a-Service: How to Keep Access Brokers Away from Your Organization – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa An attacker’s access to the network is often traced back to a succession of events, which network defenders must unravel....
Drive-by Download Attack – What It Is and How It Works – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In today’s digital age, cybersecurity is more important than ever before. Unfortunately, cybercriminals are constantly finding new ways to infiltrate...