Source: thehackernews.com – Author: . Oct 06, 2023NewsroomCyber Crime / Cryptocurrency As much as $7 billion in cryptocurrency has been illicitly laundered through cross-chain crime, with...
Day: October 6, 2023
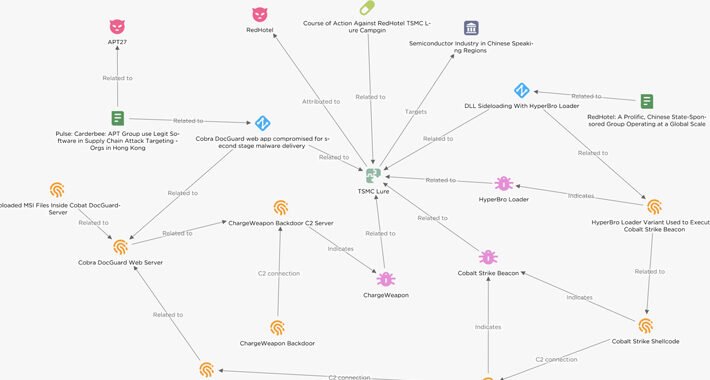
Chinese Hackers Target Semiconductor Firms in East Asia with Cobalt Strike – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomCyber Attack / Malware Threat actors have been observed targeting semiconductor companies in East Asia with lures masquerading as...
Microsoft Redesigns OneDrive for Business Layout – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse on October 5, 2023, 4:06 PM EDT Microsoft Redesigns OneDrive for Business Layout Microsoft OneDrive is adding new SharePoint features...
‘Operation Jacana’ Reveals DinodasRAT Custom Backdoor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A fresh malware threat dubbed “DinodasRAT” has been uncovered, after being used in a targeted...
Quash EDR/XDR Exploits With These Countermeasures – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ricardo Villadiego, Founder and CEO of Lumu In early 2023, a user named “spyboy” promoted a tool for evading endpoint defense on...
Legions of Critical Infrastructure Devices Subject to Cyber Targeting – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading There are at least 100,000 industrial control systems (ICS) exposed to the public Internet around...
10 Routine Security Gaffes the Feds Are Begging You to Fix – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) have issued a plea to...
Madagascar Drops Predator Spyware on Citizens in Watering Hole Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Madagascar’s government services — such as police or domestic intelligence — have apparently purchased and leveraged Predator...
Group-IB: ‘GoldDigger’ Banking Trojan Targets Vietnamese Organizations – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Group-IB discovered an Android Trojan in August targeting more than 50 financial organizations in Vietnam that it’s...
Stealthy, Thieving Python Packages Slither Onto Windows Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A threat actor has been delivering a “relentless campaign” since early April to seed the software supply...
Critical ‘ShellTorch’ Flaws Light Up Open Source AI Users, Like Google – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A newly discovered set of critical vulnerabilities in a machine learning framework known as TorchServe could allow...
Microsoft officially removes Cortana for Windows 11 Insiders – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft finally removed the Cortana standalone app from Windows 11 in the latest preview build for Insiders in the Canary...
Exploits released for Linux flaw giving root on major distros – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Proof-of-concept exploits have already surfaced online for a high-severity flaw in GNU C Library’s dynamic loader, allowing local attackers to...
China-linked cyberspies backdoor semiconductor firms with Cobalt Strike – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers engaging in cyber espionage have targeted Chinese-speaking semiconductor companies with TSMC-themed lures that infect them with Cobalt Strike beacons....
NSA and CISA reveal top 10 cybersecurity misconfigurations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) revealed today the top ten most common...
New OS Tool Tells You Who Has Access to What Data – Source:thehackernews.com
Source: thehackernews.com – Author: . Ensuring sensitive data remains confidential, protected from unauthorized access, and compliant with data privacy regulations is paramount. Data breaches result in...
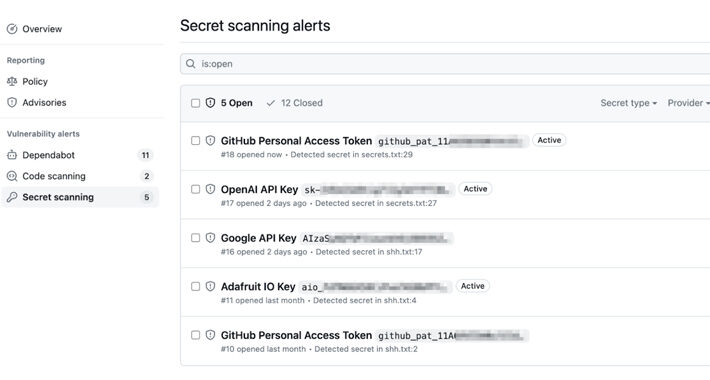
GitHub’s Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomProgramming / Software Security GitHub has announced an improvement to its secret scanning feature that extends validity checks to...
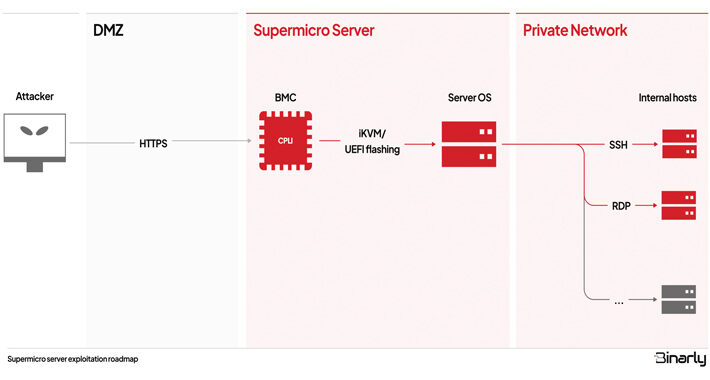
Supermicro’s BMC Firmware Found Vulnerable to Multiple Critical Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomServer Security / Vulnerability Multiple security vulnerabilities have been disclosed in the Intelligent Platform Management Interface (IPMI) firmware for...
Hospital Lobbyists Press Senator on Online Tracking Limits – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , HIPAA/HITECH , Privacy Sen. Bill Cassidy Considering Sector Feedback on Recent RFI Marianne Kolbasuk McGee (HealthInfoSec)...
Joe Sullivan: What’s a Breach? ‘It’s a Complicated Question’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Incident & Breach Response , Security Operations The Question is Also One for the Legal Team to Own, Says Uber’s Former...
Clorox Expects Double-Digit Sales Drop Following Cyberattack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Ransomware Bleach Manufacturing Giant Spent $25M Cleaning Up Huge Cyberattack in Initial Weeks Michael...
Breach Roundup: Still Too Much ICS Exposed on the Internet – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Also, Apple and Qualcomm Issue Emergency Patches Anviksha More (AnvikshaMore)...
Attackers Exploiting Atlassian Confluence Software Zero-Day – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Breach Notification , Cybercrime Critical Privilege Escalation Bug Helps Create Admin Accounts Mihir Bagwe (MihirBagwe) •...
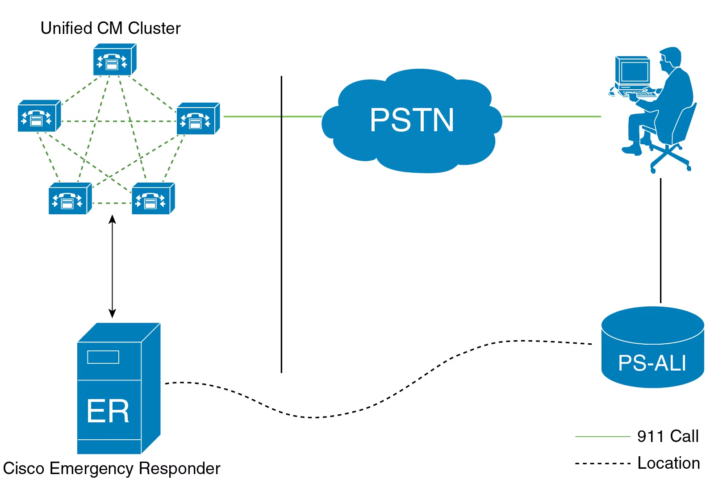
Cisco Plugs Gaping Hole in Emergency Responder Software – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine A remotely exploitable vulnerability in the Cisco Emergency Responder software could allow an unauthenticated attacker to log in to an...
GitHub Improves Secret Scanning Feature With Expanded Token Validity Checks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Software development giant GitHub on Wednesday announced an enhancement to its secret scanning feature, now allowing users to check the...
BlackBerry to Split Cybersecurity, IoT Business Units – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Canadian tech giant BlackBerry has announced plans to split its cybersecurity and IOT (Internet of Things) businesses and pursue an...
Red Cross Publishes Rules of Engagement for Hacktivists During War – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The International Committee of the Red Cross (ICRC) is urging hacking groups involved in conflict during war to abide by...
CISA, NSA Publish Guidance on IAM Challenges for Developers, Vendors – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US cybersecurity agency CISA and the NSA have published new guidance on implementing identity and access management (IAM), focusing...
Linux Foundation Announces OpenPubkey Open Source Cryptographic Protocol – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Linux Foundation on Wednesday announced OpenPubkey, an open source cryptographic protocol that should help boost supply chain security. OpenPubkey...
Qakbot Hackers Continue to Push Malware After Takedown Attempt – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The cybercriminals behind the Qakbot malware have been observed distributing ransomware and backdoors following the recent infrastructure takedown attempt by...