Source: www.securityweek.com – Author: Ryan Naraine Business software maker Atlassian on Wednesday called immediate attention to a major security defect in its Confluence Data Center and...
Day: October 5, 2023
New Supermicro BMC Vulnerabilities Could Expose Many Servers to Remote Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Server and computer hardware giant Supermicro has released updates to address multiple vulnerabilities in Baseboard Management Controllers (BMC) IPMI firmware....
Lyca Mobile Services Significantly Disrupted by Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs International mobile virtual network operator Lyca Mobile has confirmed that its services were significantly disrupted in recent days due to...
Severe Glibc Privilege Escalation Vulnerability Impacts Major Linux Distributions – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Major Linux distributions such as Debian, Fedora, and Ubuntu are affected by a GNU C Library (glibc) vulnerability that could...
Google, Yahoo Boosting Email Spam Protections – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google and Yahoo on Tuesday announced a series of new requirements meant to improve email phishing and spam protections for...
Mozilla Warns of Fake Thunderbird Downloads Delivering Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Mozilla issued a warning this week over malicious websites offering Thunderbird downloads after a ransomware group was caught using this...
Qualcomm Patches 3 Zero-Days Reported by Google – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs US chip giant Qualcomm this week announced patches for more than two dozen vulnerabilities found in its products, including three...
The 10 best phishing email templates to send to employees – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Contributed by George Mack, Content Marketing Manager, Check Point Software. Are your employees properly trained to spot the red flags in a...
STEPS FORWARD Q&A: Will ‘proactive security’ engender a shift to risk-based network protection? – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido Something simply must be done to slow, and ultimately reverse, attack surface expansion. Related: What Cisco’s buyout...
Safe, Secure, Anonymous, and Other Misleading Claims – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Imagine you wanted to buy some shit on the internet. Not the metaphorical kind in terms of “I bought some...
Play the Password Game! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rick Wednesday, October 4, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features...
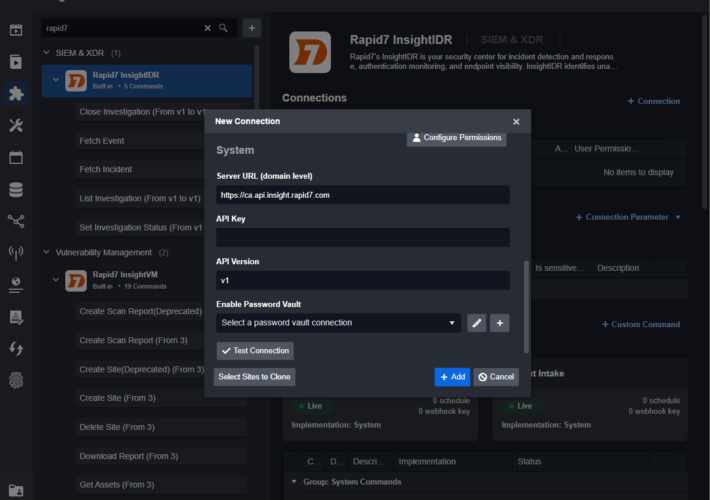
Automated Incident Response with Rapid7 and Smart SOAR – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim Integration between platforms has become a necessity rather than a nice-to-have. Smart SOAR offers a single platform to act as...
DevSecOps Trend Drivers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deb Radcliff Interview with Vince Arneja, Chief Product Officer of CodeSecure (formerly the products division of GrammaTech) Software product security has undergone...
DEF CON 31 – Daniel Wegemer’s ‘Unlocking Hidden Powers In Xtensa Based Qualcomm Wifi Chips’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/10/def-con-31-daniel-wegemers-unlocking-hidden-powers-in-xtensa-based-qualcomm-wifi-chips/ Category & Tags: Security Bloggers Network,DEF Con...
Fortifying Cybersecurity in the Finance Industry with Managed Detection & Response – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hurricane Labs Financial institutions are entrusted with a vast treasure trove of sensitive data. In this digital age, protecting this data and...
Cloud Security in Financial Services: Strategies for Safe Migration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hurricane Labs In today’s rapidly evolving digital landscape, the financial services industry is undergoing a profound transformation. The shift to cloud computing...
The Benefits of Penetration Testing and Purple Teaming for Financial Security Assessments – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hurricane Labs In an era of persistent cyber threats, financial institutions must take every possible step to protect their assets and customer...
A Guide to IAM Compliance: Set Your Organization Up for Success – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Knowles When it comes to successfully securing your organization today, the three most important words may be who, what, and how....
Two Campaigns Drop Malicious Packages into NPM – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The popular NPM code registry continues to be a target of bad actors looking to sneak their malicious packages into...
LightSpy iPhone Spyware Linked to Chinese APT41 Group – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Banking security firm ThreatFabric has found evidence that LightSpy, an iPhone spyware discovered in 2020, is more sophisticated than previously reported...
EvilProxy Phishing Attack Strikes Indeed, Targets Executives – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new EvilProxy phishing attack has taken aim at the job search platform Indeed while focusing on executives in various industries. ...
Malware-Infected Devices Sold Through Major Retailers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Human Security has exposed a significant monetization method employed by a sophisticated cyber-criminal operation. This operation involved the sale of backdoored...
Police Issue “Quishing” Email Warning – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Police in Northern Ireland have warned organizations in the province to be on their guard after issuing a new Crime Prevention...
Arm and Qualcomm Chips Hit by Multiple Zero-Day Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Qualcomm and Arm have been forced to release security updates to patch several zero-day vulnerabilities exploited in recent targeted attacks against...
Red Cross Issues Wartime Hacktivist Rules – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The International Committee of the Red Cross (ICRC) has published a new set of rules urging hacktivists to abide by international...
Apple fixed the 17th zero-day flaw exploited in attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Apple fixed the 17th zero-day flaw exploited in attacks Apple released emergency security updates to address a new actively exploited...
Atlassian Confluence zero-day CVE-2023-22515 actively exploited in attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Atlassian Confluence zero-day CVE-2023-22515 actively exploited in attacks Atlassian fixed a critical zero-day flaw in its Confluence Data Center and...
A cyberattack disrupted Lyca Mobile services – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A cyberattack disrupted Lyca Mobile services International mobile virtual network operator Lyca Mobile announced it has been the victim of...
Chipmaker Qualcomm warns of three actively exploited zero-days – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Chipmaker Qualcomm warns of three actively exploited zero-days Chipmaker Qualcomm addressed 17 vulnerabilities in various components and warns of three...
DRM Report Q2 2023 – Ransomware threat landscape – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini DRM Report Q2 2023 – Ransomware threat landscape The DRM Report Q2 2023 report provides a detailed insight into the...