Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 0
Month: September 2023
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 15
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 16
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 0
Friday Squid Blogging: We’re Genetically Engineering Squid Now – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Is this a good idea? The transparent squid is a genetically altered version of the hummingbird bobtail squid, a species...
Spyware Vendor Hacked – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Spyware Vendor Hacked A Brazilian spyware app vendor was hacked by activists: In an undated note seen by TechCrunch, the...
BSides Cheltenham 2023 – Sadi Zane – Attacking And Defending On-Premises And Cloud-Based Kubernetes Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/bsides-cheltenham-2023-sadi-zane-attacking-and-defending-on-premises-and-cloud-based-kubernetes-services/ Category & Tags: CISO Suite,Governance, Risk &...
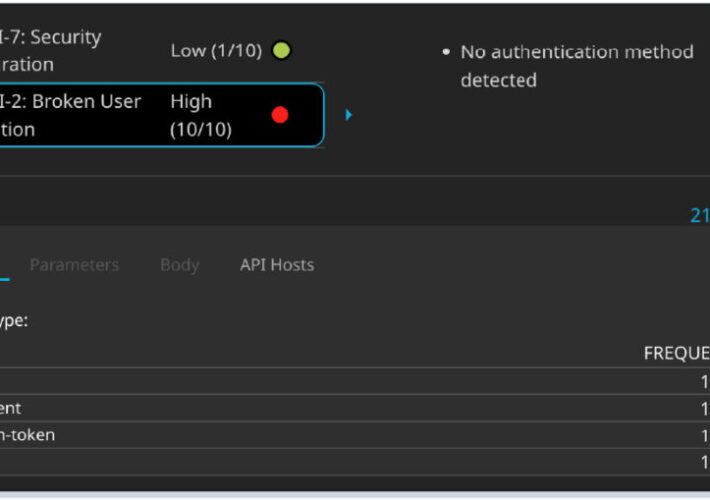
FFIEC API Security Guidance for Financial Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Brent Hansen In an era where technology is the cornerstone of the financial industry, safeguarding sensitive information and maintaining the integrity of...
Daniel Stori’s ‘The Modern Evil’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/daniel-storis-the-modern-evil/ Category & Tags: Humor,Security Bloggers Network,Daniel Stori,Dark...
Audit Management Software: Why You Need It and How to Put it to Work – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Kelly Managing audits is becoming more important, but it’s also more complicated. Luckily, audit management software can help. Audits are everywhere...
Why is .US Being Used to Phish So Many of Us? – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs Domain names ending in “.US” — the top-level domain for the United States — are among the most prevalent in phishing...
Celebrating International Women in Cyber Day: An Interview with Axiad’s Karen Larson – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axiad September 1 is International Women in Cyber Day, a special day earmarked to bring awareness to the issues women face in...
BSides Cheltenham 2023 – Stephen – All Your Firmwares Are Belong To Us: A Guide To Successful Acquisition – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/bsides-cheltenham-2023-stephen-all-your-firmwares-are-belong-to-us-a-guide-to-successful-acquisition/ Category & Tags: CISO Suite,Governance, Risk &...
Fighting Back Against Synthetic Identity Fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Christina Luttrell As the COVID-19 pandemic raged, Adam Arena was getting rich. However, he wasn’t running a prosperous business that was thriving...
Upskilling the nation’s cybersecurity savvy won’t solve the skills gap | NCWES initiative issues | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lisa Vaas, Senior Content Marketing Manager, Contrast Security Friday, September 1, 2023 Security Boulevard The Home of the Security Bloggers Network Community...
dev up 2023: Leveling up our dev skills, security posture, and careers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel One theory about the Gateway Arch is that it is a giant staple connecting the Midwest to the Great Plains....
UK Cyber Agency Warns of Prompt Injection Attacks in AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Hackers Can Deploy Prompt Injection Attacks to Gain Access to...
Threat Modeling Essentials for Generative AI in Healthcare – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 It’s critical for healthcare sector entities that are considering – or are already – deploying generative AI applications to create an...
Tech Companies on Precipice of UK Online Safety Bill – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Geo Focus: The United Kingdom , Geo-Specific , Legislation & Litigation Bill ‘Poses a serious threat’ to end-to-end encryption, Apple Says...
LIVE Webinar | What Not To Do: Avoiding GRC Red Flags for a Successful Business Case – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Mohit Lal Mug Senior Director, Customer Success, SDG Corp Mohit leads the pre-sales & customer success functions for TruOps and works...
Live Webinar | Leveraging MITRE’s 2023 ATT&CK Evaluation to Supercharge Your Security Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
‘Earth Estries’ APT Hackers Are Cyberespionage Pros – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Trend Micro Calls the Group Well-Resourced and Sophisticated Prajeet Nair (@prajeetspeaks) • September 1, 2023 Image: Shutterstock A cyberespionage...